Starting today, you can review and mitigate potential SSH key security risks in 1Password Watchtower.
When was the last time you reviewed the SSH keys on your local disk? Do you know which encryption algorithm your keys use? Is every key secured with a passphrase, or are some stored as plaintext?
We take care to protect many of the credentials we work with everyday. But too often we store SSH keys – the keys we use to access servers, databases, and other infrastructure – on the local drive and promptly forget about them.
When left unaddressed, insecure and unencrypted SSH keys are security vulnerabilities that can be exploited by bad actors. Just this month, researchers discovered malicious NPM packages designed to upload stolen SSH keys to GitHub. Fortunately both packages were removed before they could be widely distributed, but this was yet another example of malicious actors using open-source package managers to target developers and engineering organizations.
A new way to monitor the security of your SSH keys
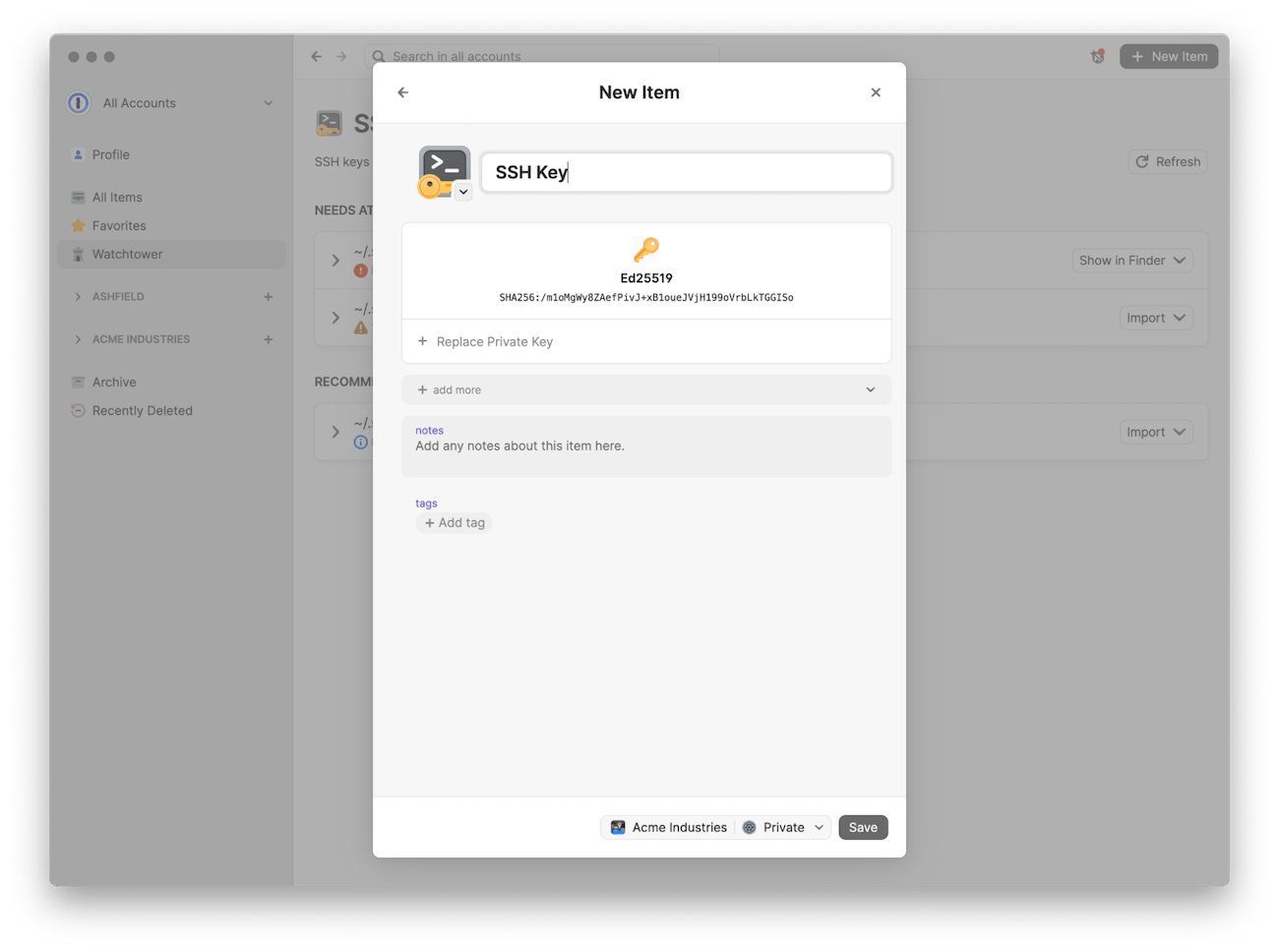
You can now choose to let 1Password Watchtower review the SSH keys stored on your local disk. 1Password will then provide security alerts and recommendations so you can easily address potential SSH key security risks. This is in addition to the many ways 1Password for SSH and Git can make SSH keys less of a headache.
Watchtower recommendations can include the option to import your SSH keys into 1Password for safekeeping. Once your SSH keys are imported, you can use the built-in SSH agent to securely create, organize, and use SSH keys wherever they are needed.
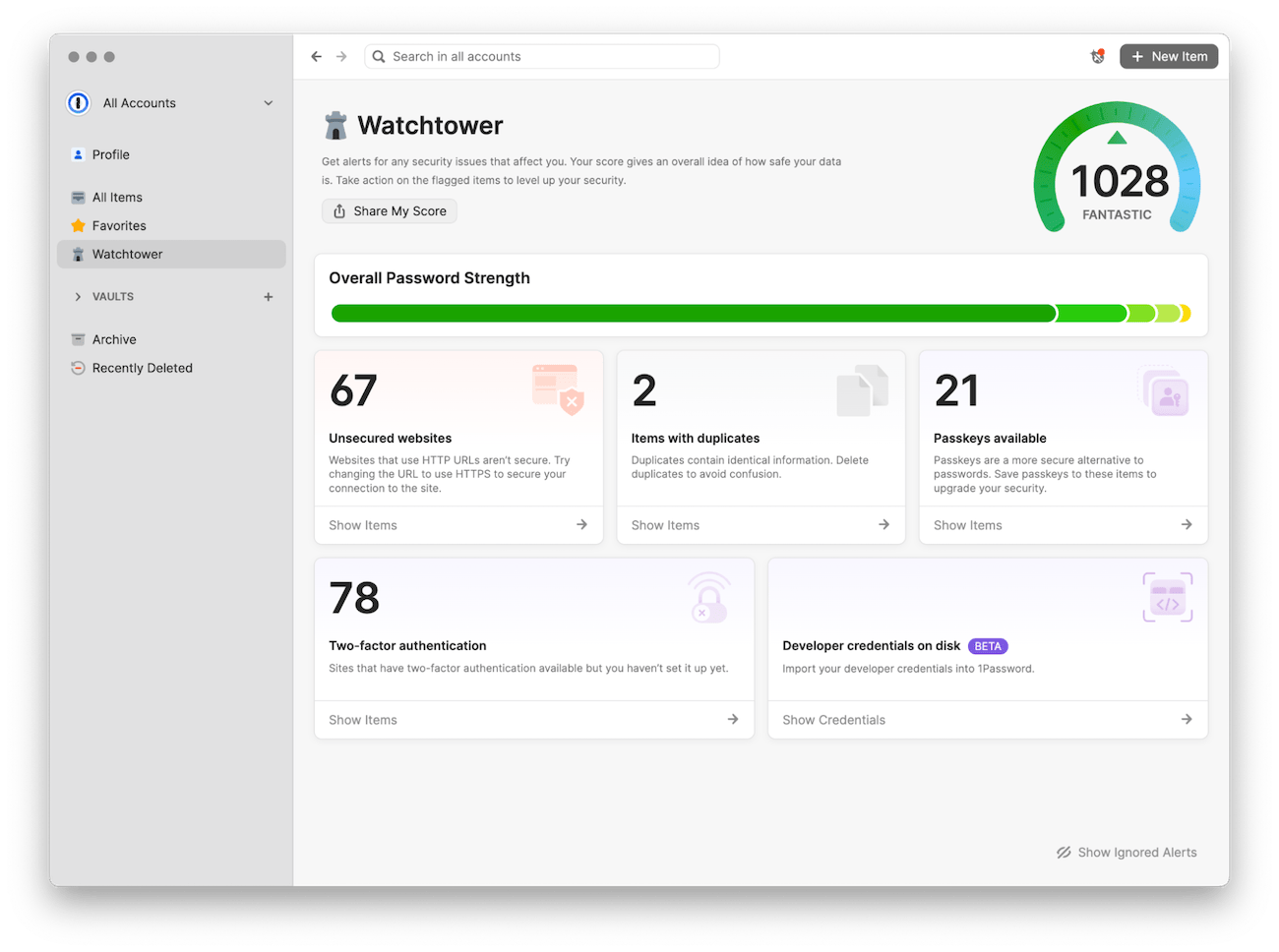
If the feature (now in beta) is enabled, Watchtower will let you know about:
- SSH keys that don’t have a passphrase set. It can be easy to forget to set a passphrase when creating a new SSH key – resulting in an unencrypted SSH key being stored on a local disk and increasing the risk of the key being compromised.
- Outdated and vulnerable SSH keys. Over time, SSH keys that were once considered secure can become outdated and vulnerable, such as those created using Digital Signature Algorithm (DSA) or RSA with a small bit length.
How to get started
You can get started with SSH keys in Watchtower in just three steps.
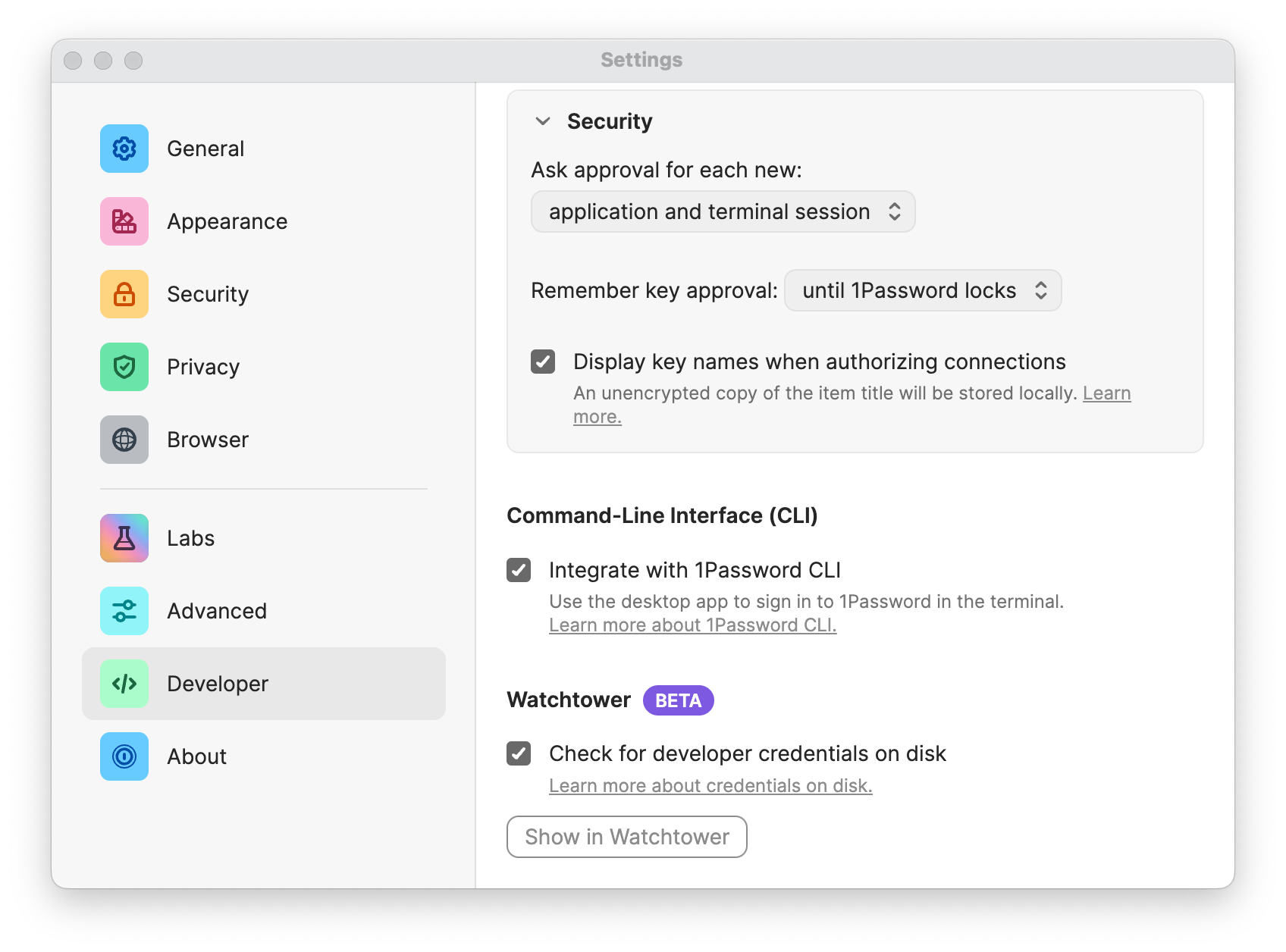
First, enable “Check for developer credentials on disk” in 1Password developer settings. This will allow the 1Password application to look on your local disk for developer credentials. (You can learn more about how this works in the documentation).
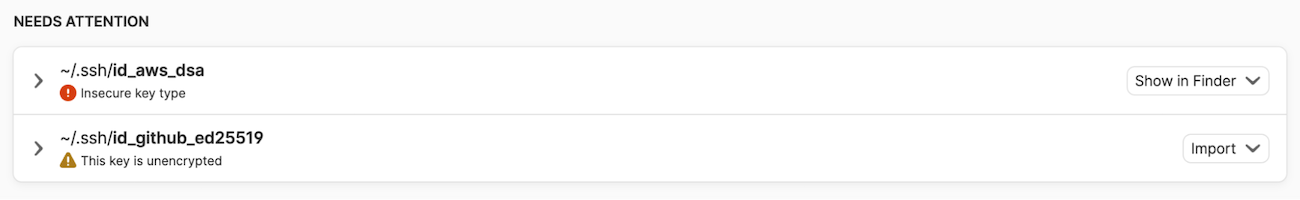
Next, open Watchtower to review alerts and recommendations. If Watchtower finds any SSH keys in your ~/.ssh directory, you’ll be presented with a list of alerts and recommendations.
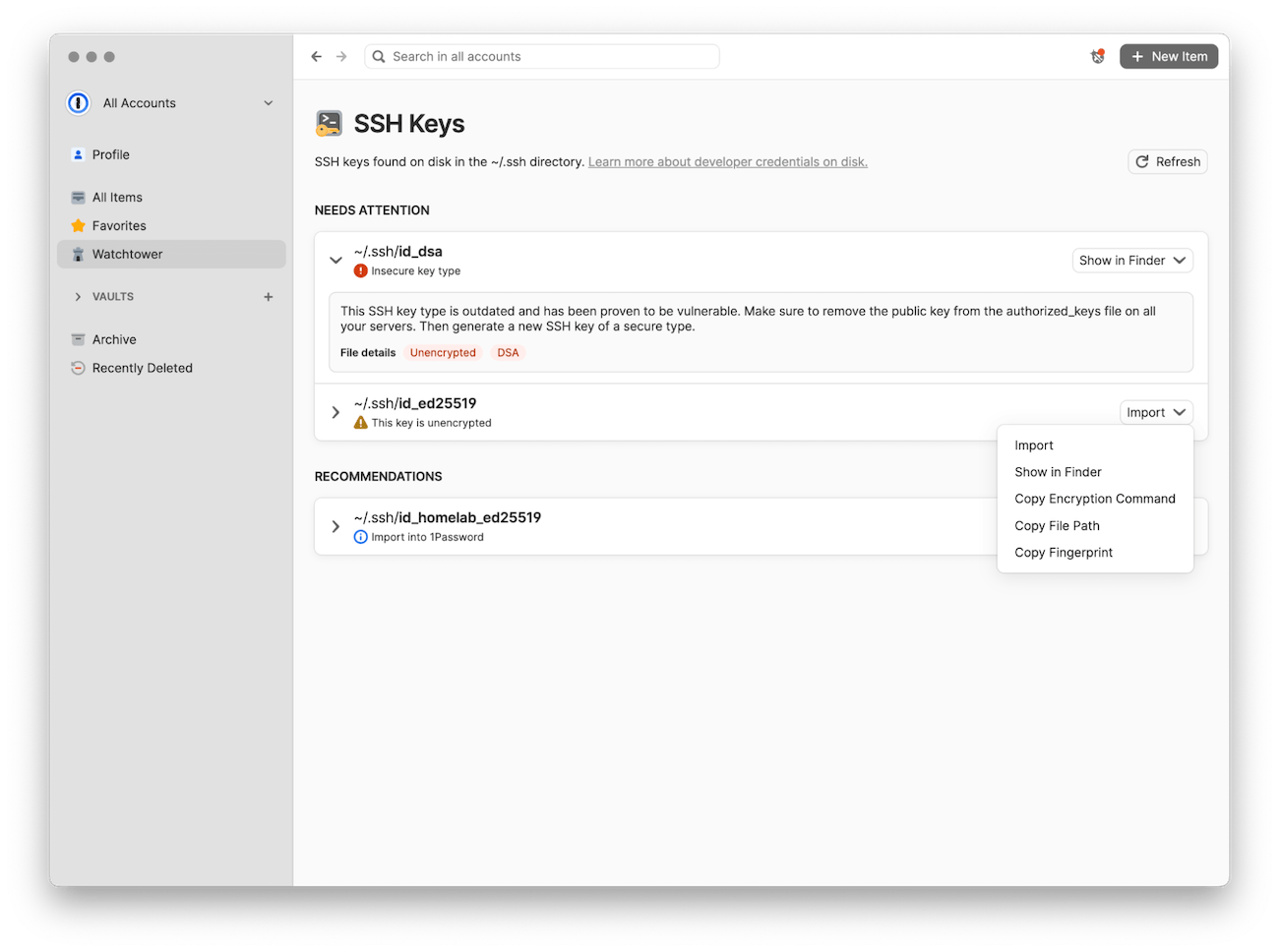
Finally, take action on the recommendations. Copy suggested commands or file paths, or import supported key types directly into 1Password to use with the SSH agent.
Simplify your SSH workflows with 1Password
The 1Password SSH agent has changed the way developers work. Signing Git commits, authenticating SSH clients, and managing SSH keys is easier than ever. 1Password has always been about making the secure way the easy way. Now Watchtower makes it simple for developers and software engineering teams to secure their SSH keys.

 by Bryan Byrne & Floris van der Grinten on
by Bryan Byrne & Floris van der Grinten on

Tweet about this post