
I have said it before, and I’ll say it again: 1Password and Knox cannot provide complete protection against a compromised operating system. There is a saying (for which I cannot find a source), “Once an attacker has broken into your computer [and obtained root privileges], it is no longer your computer.” So in principle, there is nothing that 1Password can do to protect you if your computer is compromised.
In practice, however, there are steps we can and do take which dramatically reduce the chances that some malware running on your computer, particularly keystroke loggers, could capture your Master Password.
Safe at rest
Let me clarify one thing before going on. 1Password does protect you from the attacker who breaks into your computer and steals your 1Password data. The 1Password data format is designed with just such attacks in mind. This is why your data is encrypted with keys derived from your Master Password. It is also why we’ve put in measures to make it much harder for an attacker to try to guess your Master Password in the event that they do capture your data.
Even if an attacker gains access to your computer and 1Password data, there is little she can do without your Master Password. In this article, I’m focusing on another kind of attack in which the attacker tries to “listen in” to you typing your Master Password. This attacker is running a program on your computer that attempts to record everything you type on the keyboard or enter through some sort of keyboard-like device.
Countering counter-counter measures
I will get to the details below, but this article aims to describe and explain a change in how 1Password for Windows secures its Secure Desktop, a counter measure against a common type of keystroke logger. This change was added recently to 1Password 1 for Windows and has been included in 1Password 4 for Windows since its launch.
Márcio Almeida de Macêdo and Bruno Gonçalves de Oliveira of Trustwave SpiderLabs have discovered a way that a keystroke logger could work around our use of Secure Desktop and reported this to us. They have now reported this publicly (link might be having trouble, but it’s listed among their Security Advisories). We have since added a mechanism which prevents that particular counter measure to Secure Desktop. We very much appreciate SpiderLabs for giving us the opportunity to put a fix in place before announcing their discovery to the public. Trustwave SpiderLabs might grab fewer headlines by having done the right thing, but they have done the right thing.
Secure Desktop itself is a counter measure to keystroke loggers. De Macêdo and de Oliveira’s discovery is a counter measure to our counter measure. We have now introduced a counter-counter-counter measure. All of this will be explained, but it requires a lot of background into how keystroke loggers work and various ways to defend against them.
Keystroke loggers
Keystroke loggers attempt to capture everything that is typed on a particular computer or keyboard and pass that information on to a third party.
There are one or two legitimate uses of these (such as in research on writing), but those all involve the consent of those whose key strokes are being logged. More typically, keystroke loggers run surreptitiously, and are an attack on user privacy. I know that people don’t come to this blog for relationship advice, but if you are seriously tempted to install a keystroke logger to spy on a spouse or lover – a popular use of these things – then I have my doubts about the future of your relationship. Since you didn’t come here for relationship advice (and if you did you came to the wrong place), let’s return to how keystroke loggers work.
Logger in the middle
There are many different ways that keystroke loggers can work, but one useful way to think about this is as something (either hardware or software) that sits between your keyboard and the program you are typing into, something which shouldn’t be there.
For keyboards that are attached to a computer with a cable, the simplest keystroke loggers are little physical devices that the attacker plugs into the computer, and then plugs the keyboard cable into that.
The keystroke logger is, in this case, sitting between the keyboard and the computer. The computer thinks it is talking directly to the keyboard, and the keyboard thinks it is talking to the computer, but the keystroke logger is sitting between them.
Alternatively, software keystroke loggers sit between components deep within the operating system and silently grab data. Things that are embedded that deeply or are using hardware loggers are not things that user software can detect or defend against.
Most keystroke logging is shallow
Most keystroke loggers take a simpler approach, rather than inserting themselves deep within the system. It is much simpler to write a program that says “hey, I am a program that needs to know everything that is coming in from the keyboard.” Operating systems provide hooks for programs to do exactly that.
You might be asking why operating systems might make writing keystroke loggers so easy. What business does any program running in the background have in seeing the input to some other program? One reason is to help my poor dog Molly, who suffers from (among other things) diabetes. This has led to sufficient necrosis in her paws so that she cannot easily type using a standard keyboard. The specialized device that she uses involves some clever software that looks at the input and uses various predictive technologies to replace the actual input with the intended text. This system intercepts (and changes) input bound for any program running on her computer; however, as far as most programs know, they are just getting input from a “keyboard”. Assistive technologies similar to the one Molly uses are a big part of making computing and communication accessible to more people.
Not only is a basic keystorke logger easy to write, it doesn’t require a complete break into a system. Different processes on a computer run with different privileges. When Molly logs in to her account and runs a program on a computer, the program is run under her user ID and with her privileges. This means that she isn’t able to interfere with processes that are run by Patty (the other dog). She also isn’t able to interfere with the system as a whole. If Mr Talk (the neighbor’s cat) tricks Molly into running a malicious program, that malware will be limited in the damage it can do.
The really deep and hard-to-avoid keystroke loggers would require full power over the system to install. But one of these simpler keystroke loggers requires only the privileges of the user whose keystrokes are to be recorded. So if Molly gets tricked into running a keystroke logger, it won’t affect Patty even if they use the same computer (as long as they are using different accounts). As you can imagine, the bulk of malicious keystroke loggers that spread through computer infection are of this shallower sort.
Counter measures
Now that we have some idea of how the typical keystroke logger works, it’s time to look at some counter-measures. The two most important counter-measures are:
- keep your system and software up to date
- exercise caution in what software you install and run
But let me focus a couple of the counter-measures that 1Password takes.
Counter measures on Mac: Secure Input
On Mac OS X, there are two simple provisions that makes it easy to thwart those shallow key loggers. The first one of these is called “Secure Input” and was introduced with OS X 10.3 Panther in 2003. A program—1Password for example—can say, “when the user types something into this particular input field, it must be done in a way that other processes can’t interfere.” Secure Input needs to be used sparingly, as it blocks all of the sorts legitimate activity, including assistive technologies that many people (and a few dogs) rely on. And Secure Input blocks TextExpander, which I rely on.
1Password declares the field in which you type your Master Password as a “Secure Input field”, then ordinary key loggers won’t have access to it. Since last year’s OS X 10.9 Mavericks, there is another defense built into the operating system. A program can only capture all of a users’ keystrokes if the user has explicitly granted it that permission in System Preferences > Security & Privacy > Privacy under Accessibility. As I described earlier, most (but not all) such software are components of assistive technologies designed to make computers accessible to more people. That is why this system preference is ultimately under Accessibility.
Between these two mechanisms – Secure Input and that any application which has the capacity to log keystrokes must have explicit user approval to do so – OS X defends against these otherwise common sorts of keystroke loggers.
Counter measures on Windows: Secure Desktop
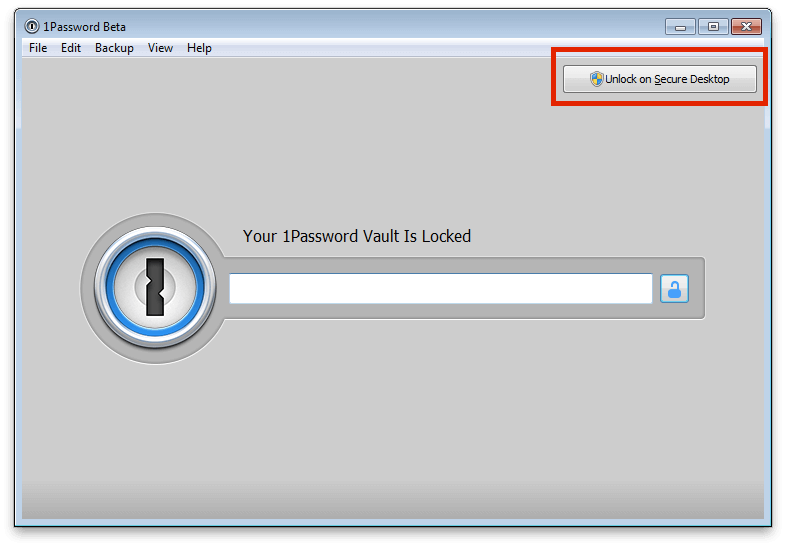
Windows doesn’t offer the same sorts of defenses that OS X has, but it does allow for the creation of somewhat isolated environments called “Desktops”. On Windows, one can set up different Desktops in which only your program is running (along with system processes). A program running in one Desktop will not be able to listen in on keyboard input in a separate Desktop.
You will find a button that says “Unlock with Secure Desktop” in the upper right corner of the lock screen in 1Password 4. Clicking on that launches the Secure Desktop in which you will be prompted for your Master Password.
Countering Secure Desktop
What de Macêdo and de Oliveira have discovered is that there is a way to set up a keystroke logger that does operate in all desktops, not just the one it was started in. Quite simply, their system launches a process that is able to listen for the creation of new desktops and add a process to each desktop created.
The ease at which they were able to do this (well, everything looks easy in retrospect) reflects the fact that the SwitchDesktop function in Windows was not designed for security purposes. We and others who use Secure Desktop as a mechanism for evading keystroke loggers have been taking advantage of the relatively isolated environment of a separate Desktop. Once the authors of keystroke loggers take our counter measures into account, they can launch counter-counter measures like the one Trustwave describes.
Knowing your environment
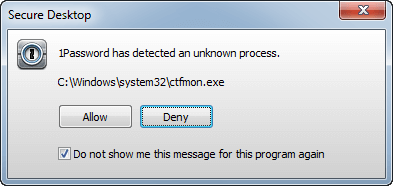
We want nothing but system processes and 1Password’s Master Password entry to be running in a Secure Desktop. We don’t want other, probably malicious, processes joining that Desktop. And so, our counter-counter-counter measure is to simply look around and see if there is anything running in the SecureDesktop that is unexpected.
If some unexpected process is found in the Secure Desktop environment, you’ll be prompted to close the Secure Desktop.
Lessons
- Keep your system and software up to date
The single biggest thing you can do for your computer security is to keep your system and software up to date. The overwhelming majority of actual break-ins are through vulnerabilities that have already been fixed by the software vendors.
- Pay attention to what software you install and where you get it from
Keystroke loggers and other malware are often installed unwittingly by the victims themselves. Try not to be one of those victims. Be particularly careful of anything that tries to frighten you into installing it. Fake security software and alerts are a common way to get people to install malicious software.
The move toward curated app stores offers additional protections, but it isn’t a complete solution. Still, using those where available will reduce your risks.
- Use Windows Defender on Windows
I have long been skeptical of most anti-virus software, but Microsoft Security Essentials is something I can unequivocally recommend for those using Windows 7. In Windows 8, Windows Defender is automatically built in and enabled.
- Understand what software can and can’t do for you
The core security design of 1Password is extremely strong. Quite simply: if you have a good Master Password, nobody who gets a copy of your 1Password data will be able to decrypt it. 1Password can and does offer outstanding security.
At the same time, 1Password is limited in what it can do to protect you when you are using a compromised computer. It can (and does) offer some protection against shallow (the most common) attacks. But this is a bit of an arms race. As you see, we have had to put into place a counter measure to a counter measure to our counter measure against common keystroke loggers.
This is why the first two items on this list are so important.
In conclusion
1Password takes extraordinary and effective steps to protect your data. This is built into every aspect of its design. But you have to help protect 1Password from malware running on your machine. We do what we can to make things harder for the malware writers, but we can’t do it alone. You must try to provide a safe environment for 1Password and all of your software to run in.
This shared responsibility is similar to that which we have with your Master Password. We provide excellent encryption and protections and defenses against automated password guessing. But you have to pick a good Master Password and treat it well. For those who might be wondering, displaying your password on a giant screen is not treating a password well.


 by Jeffrey Goldberg on
by Jeffrey Goldberg on

