A public preview of Unlock with Okta is now available.
We’re pleased to announce that a public preview of Unlock with Okta is now available for all 1Password Business customers. This allows admins to set up their 1Password account so that team members sign in to 1Password with their Okta username and password, rather than their account password and Secret Key.
How did we get here?
A few years ago, unlocking 1Password with SSO began to come up more and more in conversations with our customers. While the value and benefits were clear, we didn’t pursue this feature because at the time we didn’t have a way to build it that met our stringent security standards. Unlocking with SSO has its own risk considerations that differ from 1Password’s traditional unlock model, and we wanted to make sure our solution was truly secure.
After many months of research and listening to our customers, we’ve engineered a solution with the same careful consideration for our customers' privacy and security as every other feature we’ve rolled out.
The SSO project officially kicked off in 2022 and since then, we’ve had over a dozen unique teams and over 100 people here at 1Password working to bring this feature to our users in the most secure way possible.
SSO: the 1Password way
Other enterprise password managers support SSO by taking one of two approaches.
The first is an auth bridge, which creates a large and attractive target for an attacker, and requires customers to maintain on-premise infrastructure. The second is a shared encryption key, which means if a single employee is compromised, the entire company is put at risk. Neither of these approaches meet our stringent security requirements.
We opted for using a trusted device model, which means that if your identity provider credentials are ever compromised, attackers still won’t have access to your 1Password data. Unlock with Okta shifts away from needing the Secret Key that you are used to with your 1Password account, but it does so in a way that keeps all data secured on-device and at the same time increases your convenience. This is because a bad actor would still need a trusted device in order to prove your identity and access the data locked away inside your vaults. Your data will remain protected and now it’ll be even easier to sign into new devices that you own.
Our approach maintains zero knowledge, and is end-to-end encrypted, as decryption still occurs on device. We don’t store or have access to the keys needed to decrypt your data.
How Unlock with Okta works
Here’s the short version of how our SSO solution works. Once a team member authenticates with Okta and returns to 1Password, the 1Password app downloads the user’s encrypted credentials. The team member’s device key, which is stored only on the user’s device, is then used to decrypt the credentials and complete the 1Password authentication process. After authenticating, team members can access their data just like before with biometrics (which can be configured by admins).
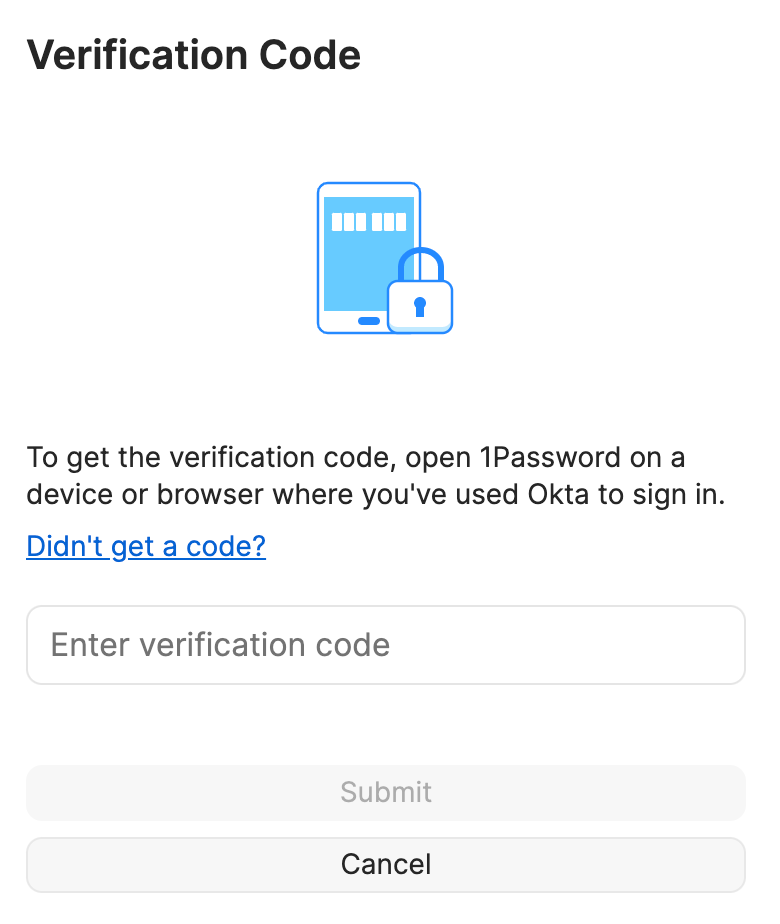
To add a new trusted device, the team member signs in to Okta again, thereby proving their identity. Then, using an existing trusted device, they enter a randomly-generated verification code (which is used to authenticate an end-to-end encrypted exchange between the new device and existing trusted device). This setup is only needed once for every additional trusted device that’s added to a user’s account. This is because 1Password’s server will store an encrypted version of the account’s unlock key for each trusted device within the user’s account.
Why start with Okta?
We’ve had hundreds of requests over the years for various IdP integrations (including Azure, Duo, OneLogin and others). Okta, however, was by far the most requested identity provider, which is why we started with this integration.
Until now, our Unlock with Okta project was in a private beta, with a large group of 1Password customers deploying and testing the feature. The feedback helped us identify and solve bugs, make general improvements, and simplify our onboarding experience and documentation to make the deployment even easier.
We’re excited that many more customers can now try Unlock with Okta through our public preview. We’ll share more information as we get closer to general availability and the rollout of additional identity provider integrations.
The experience
Using 1Password alongside Okta can greatly improve manageability and ease-of-use of your organization’s security. As an administrator, you can automate provisioning, enforce stronger, auditable security policies from your identity provider, and give your employees a simpler way to access their passwords and other digital secrets – like documents, Secure Notes, and SSH keys – that aren’t covered by Okta.
We designed the setup wizard to be as simple as possible so you can roll out Unlock with Okta with as few clicks as possible. You’ll start by adding your client ID and Okta domain to the 1Password setup wizard. Once that’s configured, you’ll add the 1Password application directly to Okta, configure the grant type and sign-in redirect URIs, and make a few small tweaks to the 1Password application you’re configuring.
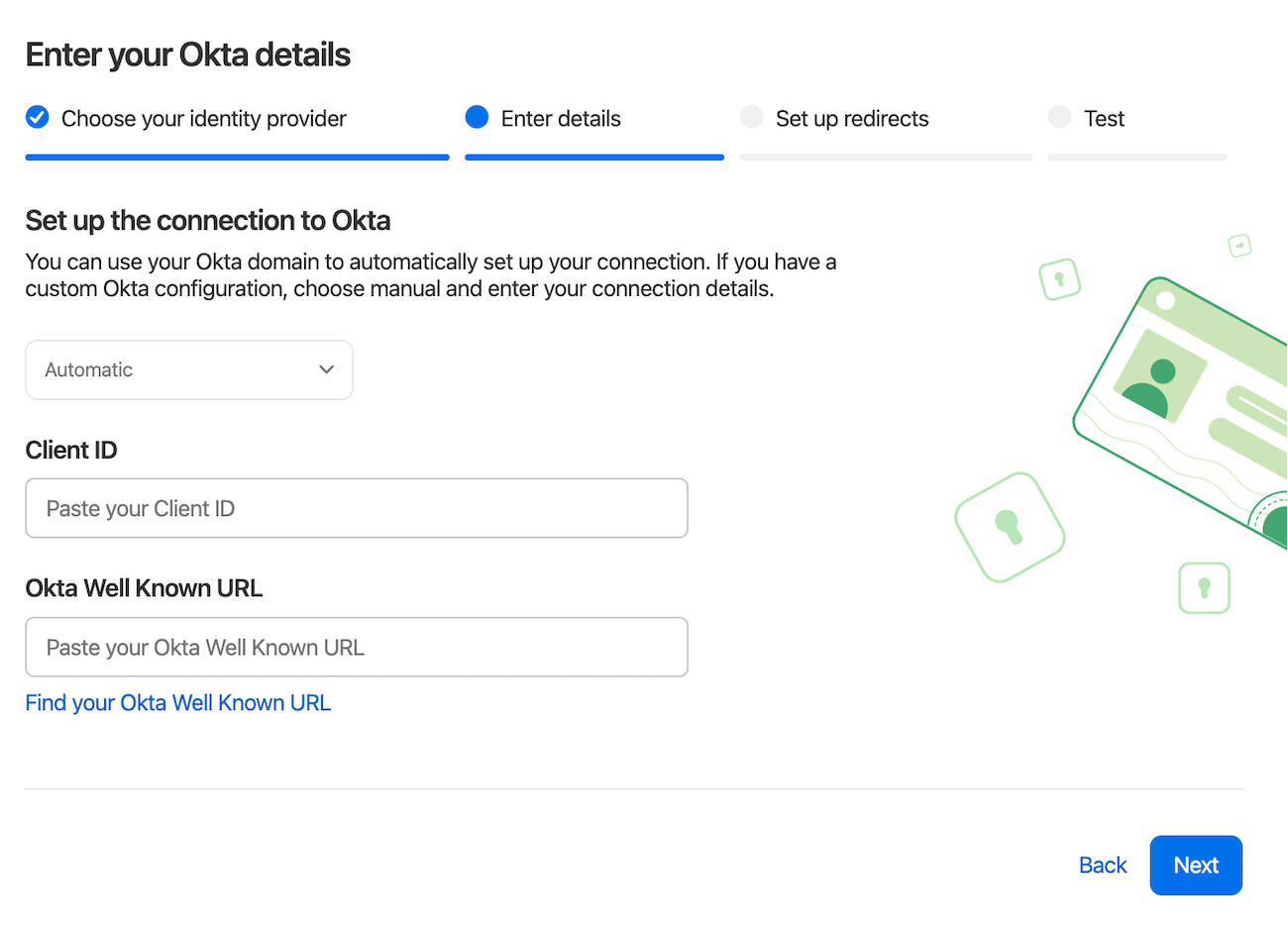
Once you’ve assigned yourself to the Okta application (ensuring your Okta email matches your user profile in 1Password), you can then start testing the initial configuration.
Deployment strategies
After you’ve successfully authenticated with Okta, you can move on to configuring how to deploy SSO to your employees. The first choice you’ll make is who will need to sign in and unlock with Okta. We have several options for you to choose from, including:
- Selected groups
- Everyone but guests and owners
- Everyone but owners
The choice is up to you, however, we recommend a staged rollout for most companies: start with a few groups and add more later. You can even create a custom group and assign users to it for your initial rollout. Or, you can jump in with both feet and select “Everyone but Owners”.
Configuring the migration grace period
Afterwards, you’ll configure the “grace period” that employees have to change their sign-in method from our traditional Secret Key and account password. Team members will then see a migration wizard the next time they authenticate with one of their devices.
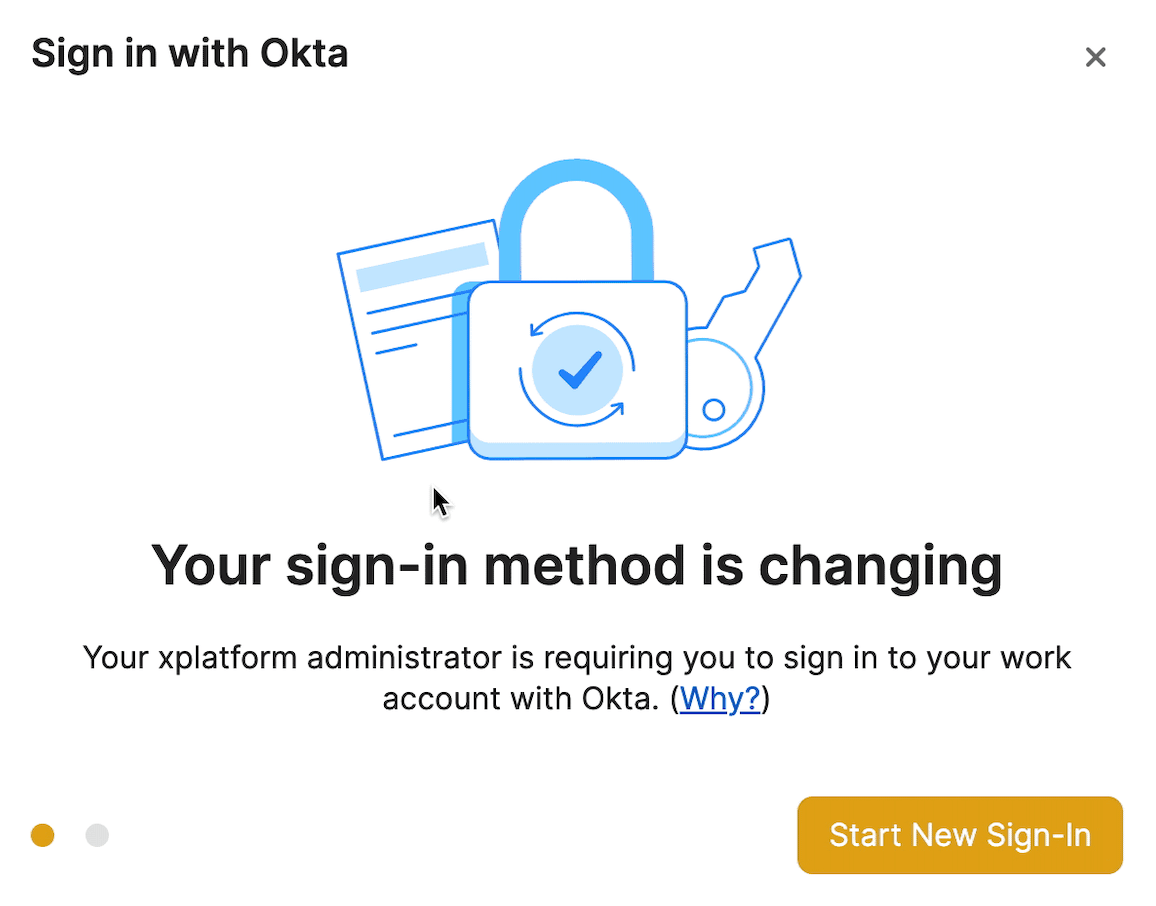
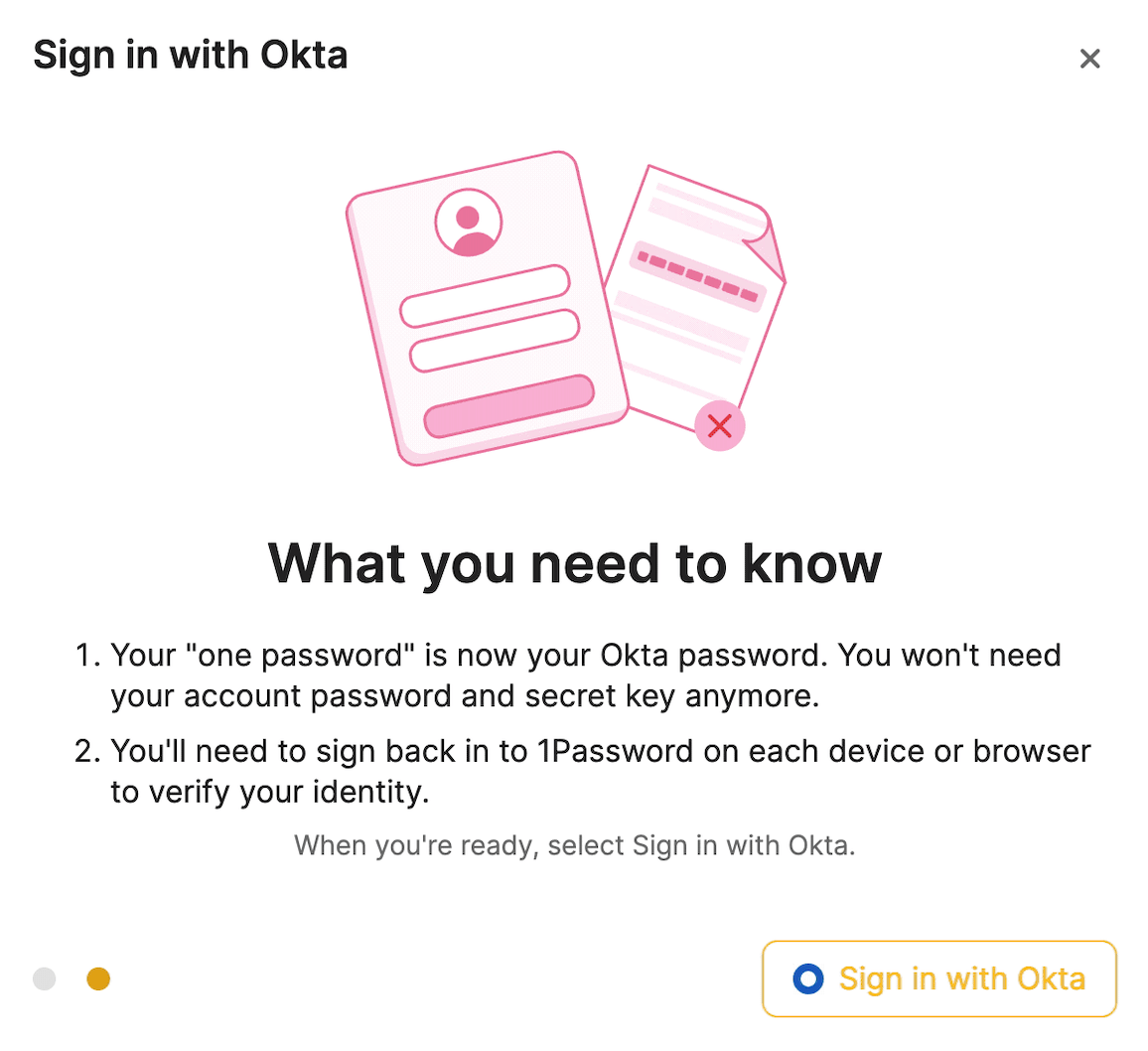
If a team member doesn’t complete the migration within the allotted time, they’ll be locked out and an administrator will need to recover their account before being able to access their data.
Biometric Unlock
We have one final configuration option for you when rolling out SSO support: biometric unlock. Enabling this feature will allow team members to access their data offline and sign in to the 1Password apps with Touch ID, Face ID, and Windows Hello.
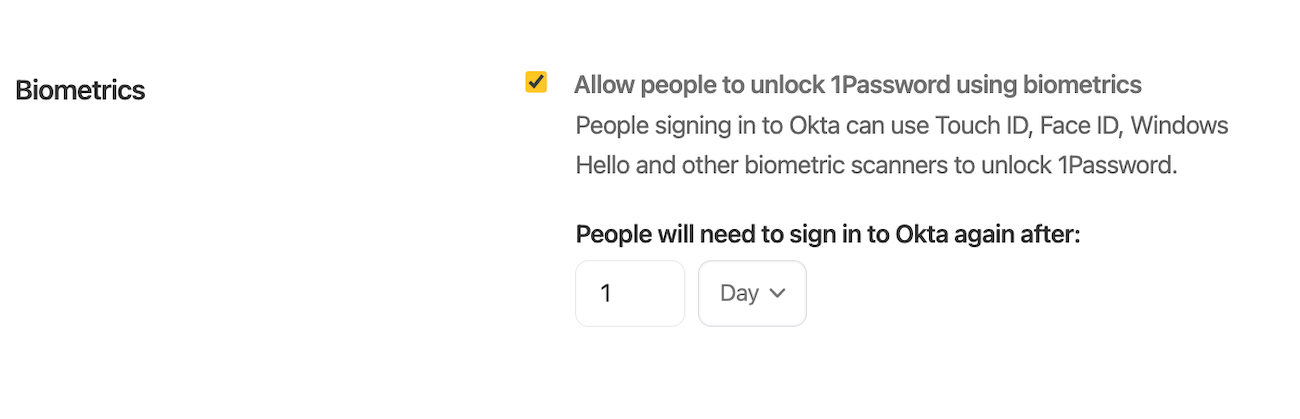
What does all of this mean for your team and their account passwords? Once they make the switch to sign in with Okta, they’ll no longer have an account password to sign into 1Password. Instead, they’ll be authenticating with Okta. If you’re an admin, make sure that your rollout of this integration also includes a full review of your Okta configuration. You’ll need to adjust any existing password policy for Okta to ensure users have a “memorable” password set.
In addition, if your employees are storing 2FA within 1Password, that too will need to be changed since they’ll be unlocking 1Password with Okta after the initial rollout.
What the future holds
The public-ready version of Unlock with Okta will be available to all 1Password Business customers soon. Afterwards, we’ll be focused on Azure, followed by other identity providers like Duo, OneLogin, and more. Our initial flurry of releases will focus on OIDC but SAML is also on our roadmap.
Here’s a sneak preview of our work on Azure, which will be coming soon as well.
Is there a particular identity provider you would like us to support? Send an email to business@1password.com so we can record your request and any additional information that you’d like to share.
(Editor’s note: This post was last updated on 15/02/2023)
 by Tyler Durkin on
by Tyler Durkin on