Editor’s note: This blog post was written in 2011. You can now protect your 1Password account with two-factor authentication, using an app like Authy or a security key. Teams can also use Duo’s authentication app as an extra layer of protection for employee accounts.
“Why doesn’t 1Password offer two factor authentication?” That is a question we face regularly, and one we often ask of ourselves. Ultimately, the question boils down to two kinds of data security risk: threats to confidentiality versus threats to availability.
What is Multi-factor Authentication?
Before we descend into the buzzwords that this topic requires, let me first say that “authentication” means proving who you are to some system. When you log into our forums with your username and password, knowing your password proves that you are the same person who set up the account. Your knowledge of your password is an authentication factor.
Of course, if you use a password manager like 1Password, you probably don’t know most of your saved passwords. I naturally use the 1Password Strong Password Generator to create most of my passwords, which means I not only don’t know those passwords, I haven’t even seen most of them. So to be more precise when talking about logging into a site, I really should have said: “your ability to correctly enter your site password based on some knowledge in your head (your 1Password Master Password)” is an authentication factor, instead of “knowing your password” for the site. But for the sake of simplicity, I’m going to stick with just “knowing your password”.
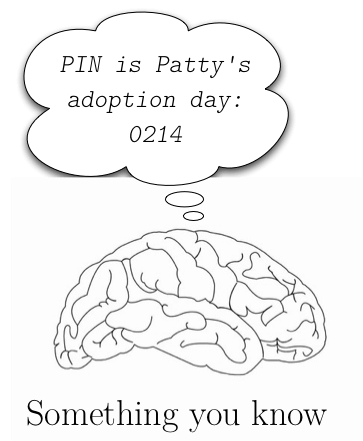
When you use a bank cash card at an automated teller machine (ATM) you must provide the machine with both your physical card (something you have) and with your PIN (something you know). Each of these, the card and the PIN, are authentication factors. So even if you’ve never heard the term “two factor authentication” you have almost certainly been using it for a while. Another example of two factor authentication is with a safe deposit box in a bank. You need ID and signature, as well as a physical key, to gain access.
Because bank ATM authentication requires the card, the PIN can be a weak password; and because the PIN is required, theft or duplication of the card isn’t a disaster (of course, in these cases, access will be completely and necessarily shut down after a small number of failed authentication attempts). The point of this example is to show that two factor authentication allows for each factor to be fairly weak on its own, while still providing an authentication system strong enough that banks and their customers are willing to trust it.

Many social media platforms, online stores, and other internet services have recently added two (or multi-) factor authentication systems. One way that these work is that when you begin your traditional web login on a new device, the system will send a text message to your phone with a random, one time code. In addition to your username and password, you will need to enter that code to demonstrate you have possession of your phone, which has become a separate factor in this case from knowing your password.
Other two factor systems involve knowledge of the contents of some piece of paper. That is, you may be prompted for the second letter of the third word on the fifth row of your credit card. You would be expected to carry this card with you while keeping your password in your head.
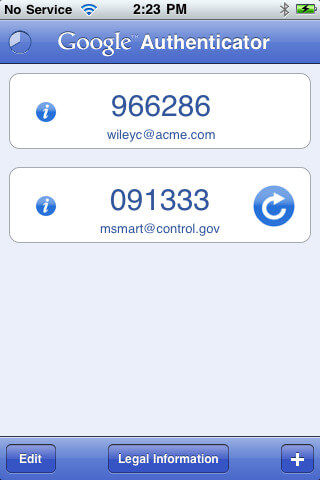
Still other mechanisms involve a higher level of gadgetry. One variant involves a USB device that you would need to plug into your computer. In other cases, a gadget would generate a seemingly random one time code that you would use as one factor along with your knowledge of your password as the other.
How do you solve a problem like passwords?
What you may have noticed from the examples above is that two factor authentication systems are designed, in part, to address the password problem. The password problem is that because most people reuse passwords from one site to another and their passwords are weak, passwords are easily compromised. With what we know about how most people use passwords, those passwords don’t provide very reliable authentication.
1Password is designed to solve the password problem by making it easy for people to have strong, unique passwords. So what we have is a different way of solving the same fundamental problem. If you use 1Password and our Strong Password Generator, then there is little added security gain by using two factor authentication.
There are other proposed solutions to the password problem, but this is already a digression from the big question of using multi-factor authentication to get at your 1Password data.
One and a Half Factors?
Currently 1Password uses less than two factors to gain access to all of your passwords, but in a sense it also uses more than one factor.
Let’s look at what it takes for someone to gain access to, say, someone’s Gmail account. What is needed is an Internet connection, the victim’s Gmail address, and the user’s Gmail password. Two of those are easy to obtain, especially since most people’s email addresses aren’t secret. So there is only one factor that matters here: the victim’s password. Once that password is obtained, the Gmail account is completely compromised.
Now let’s consider this case with 1Password. If someone gets hold of your Master Password, do they instantly have access to all of your data? No, they need to actually get hold of your encrypted 1Password data. This can be done either through the theft of a computer on which the data is stored or through a breach at Dropbox. That is, getting your 1Password master password isn’t the only thing that is needed.
I know that computers do get stolen and a compromise of a syncing service remains a non-negligible possibility. That is why I am not calling what we currently have “two factor authentication”. But 1Password does require access to both data and the master password, so it is fair to consider it as involving more than one factor, even though it isn’t two factor.
Your Master Password: A very strong factor
Your 1Password master password is better secured than typical website passwords. For one thing, it is never transmitted over the network. I hope that it is also unique; it is not a password that you use anywhere else. Some ways to steal a password (listed from easiest to hardest) are:
- Ask for it: Phishing attacks use this method. People give their webmail passwords to, say, a carefully crafted website that they shouldn’t be giving it to. No phishing scam is likely to trick anyone into providing their 1Password Master Password into anything that isn’t 1Password.
- Sniffing it from network traffic: It is frighteningly easy to sit in a coffee shop with free Wi-Fi and collect usernames and passwords or cookies that also enable authentication. I’m preparing a separate blog post on that topic. Again, your 1Password master password is never transmitted over the network, so it can’t be captured this way.
- Password reuse: Using the same password in multiple places dramatically increases the opportunity for that password to be captured. Here I have to trust that our users are taking some of our advice to heart about selecting strong and, more importantly, unique Master Passwords.
- Brute-force attacks: I’ve already written about what we do to hinder password crackers as well as what you can do.
All of this means that the factor which does most of the work—your Master Password—is very strong indeed. It is not vulnerable in the ways that typical login passwords are. This, coupled with the fact that our design requires separate access to your encrypted data, has led me to believe that adding two factor authentication to 1Password would be an exercise mostly in “security theater” than actual security.
First, Do No Harm
As two factor authentication can be, I’ve listed why it really wouldn’t add much practical security to 1Password. But those reasons, on their own, don’t fully answer the question of why we don’t make it available as an option to those who would like it. Let me start with the biggest reason.
Data availability
For every one report of “someone stole my computer, is my data safe?” query that we get, we get 100 “I’ve forgotten my master password” queries. (That’s an exceedingly rough estimate. We don’t keep a tally of these, but that 1 to 100 ratio seems about right to me.) We know that people lose access to their 1Password data, while we know of no case of someone breaking into someone’s data.
I’ve written earlier about how “data availability” is a part of “data security”, which people often overlook. The concept is indeed far less glamorous than “data confidentiality”. Data availability means that the legitimate user of the data can access it when they need to. I have many hundreds of unique passwords stored in 1Password. If I lost access to those, I would be sad.
There are many ways 1Password works behind the scenes to do help reduce the risk of data loss, but for this discussion I want to describe the backups that 1Password for Mac and 1Password for Windows automatically make. Every backup can be opened with the Master Password from the time the backup was created. This is particularly useful for people who change their Master Password and then forget their new one.
Two factor authentication dramatically increases the ways that a legitimate user can lose access to their 1Password data. Loss or damage to the second factor will leave someone locked out of their data forever. If two factor authentication is to really require the second factor, then we can’t back up the information that is in that second factor. Nothing we could do will help protect users against the loss of the second factor. The layers of defense we have for data availability are stripped away with requiring a second factor.
Other drawbacks
There are a few additional things to consider as potential reasons to not include multi-factor authentication. Adding complexity in both our system and in what users deal with should be limited to cases where that complexity provides a clear benefit.
We would also need to get any second factor working on all of the platforms we support: Mac, Windows, iPhone, iPad, and Android. (This rules out the often suggested use of something that depends on a physical dongle to be plugged into the computer.) Adding the feature isn’t an insurmountable problem, but it is something that can be easily overlooked by those who only use 1Password on their desktop computers.
For a second factor to provide any security, it must be able to unlock your data even if your data is accessed outside of the 1Password application. We have to assume that the bad guys who get hold of your data can attack the data directly without going through our software. This means that your data is useless to an attacker without the second factor, even if the attacker knows your master password. (This is the whole point of multi-factor authentication). The second factor must be required no matter where your data appears, whether it is on your desktop computer or on your iPad.
Now that the foundation of our new browser extensions is settling, we can continue building some great new things along these lines that we believe 1Password users will love. We’re delighted to start shifting our development focus to these new advancements.
Never a Final Word
I’ve tried to show why the need for multi-factor authentication in 1Password is not as strong as it might initially appear. Master Passwords are not vulnerable to the kinds of threats which target passwords that are used online. Plus, the 1Password data file represent a bit of a factor itself.
I’ve also tried to explain that there is a downside to adding complexity, both in the code and for users, and the biggest drawback is the dramatically increased risk of legitimate users losing the ability to decrypt their data. Does this mean that our final word on multi-factor authentication is “no”? Of course not. We don’t issue final words. “Agile” is part of our name for a reason.
We’ve had great discussions in our forums about two factor authentication previously, and I would like direct discussion of this topic there. Let’s hear your concerns and desires. I’ve created a new forum topic specifically for discussing this post. See you there.

 by Jeffrey Goldberg on
by Jeffrey Goldberg on

