When talking about reports of tools that break into iPhones, it is very important to remember that the seller may be inclined to overemphasize its capabilities. It is also wise to keep in mind that the more sensational claims are the ones that tend to be picked up, and perhaps amplified, by the press. In this light, let’s talk about Micro Systemation’s XRY, a cracking/forensics tool for extracting data from iOS and Android devices.
XRY, despite its recent press attention, does not appear to represent anything new. Everything that we said in Lost iPhone? Safe passwords! still holds true. Your 1Password data remains encrypted. That is, even if an attacker gets through all of the iOS security, including capture of the device passcode, he or she would still have to break your 1Password Master Password to get at your 1Password data.

News of XRY has been circulating since Andy Greenberg of Forbes drew attention to it and to Micro Systemation’s video demonstration.
The demo shows discovery of an iPhone’s passcode in a matter of second. This should naturally cause concern for everyone who cares about their privacy.
But I’m going to try to sort out what the real concerns are, and what you can do to to better protect yourself.
Cracking passcodes
Even though your 1Password data remains protected, tools like XRY or Elcomsoft’s iOS forensic toolkit do represent a threat to the secrecy of other data stored on your device. Furthermore, most people will have weaker 1Password Master Passwords on their phones than they will on their desktop systems. This means that we do need to be a bit more concerned about what happens if people steal your encrypted 1Password data from your iOS device than if they steal your encrypted 1Password data from your desktop or Dropbox. Therefore it is worth spending a bit of time talking about device passcodes and the security of your iOS device in general.
Note that when I talk about your “device passcode” I’m talking about the passcode that is used to unlock your iPhone, iPad or iPod touch in the first place (assuming you set one, of course). I am not talking about your 1Password unlock code or master password. Those are different things. The tools described are all about breaking the device passcode and what can be done once that is available.
First, these tools jailbreak the device. This allows the user to then run a brute force attack on the device passcode. That attack must be run on the phone itself because it is tied to a unique device key. You may think that running through all of the passcodes, 0000—9999 would just take a fraction of a second, and under normal circumstances you would be absolutely correct. But Apple has protected the passcode with PBKDF2, which forces each trial to perform thousands of complex computations. Although things will differ from device to device, Apple appears to have tuned things so that it takes about one quarter of a second to process a single guess.
Without having hands on experience with XRY I can’t be absolutely certain of this, but I strongly suspect that the reason that it was able to discover the passcode so quickly in the demonstration was because the passcode was “0000”. That is, “0000” may be the first passcode it tried. At four guesses per second, it would take about 40 minutes to try all possibilities, with an average break time of 20 minutes. As we’ve seen, sometimes it can hit upon the correct guess quickly, but in other cases it may take the full 40 minutes.
Not so simple passcodes
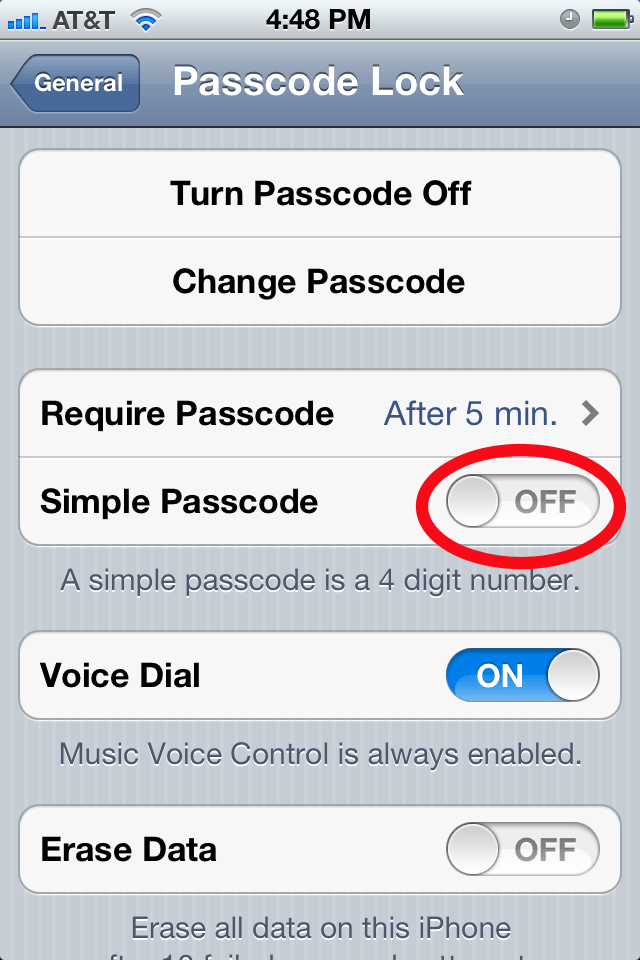
Twenty minutes to break into your device is still too quick for many of us to be comfortable with. Fortunately it is easy to set a longer passcode on your device. Launch the Settings app and go to General > Passcode Lock. You will be asked to re-enter your passcode at this point; after all, you wouldn’t want anyone who picks up your unlocked phone to be able to fiddle with its security settings. Once you’ve done that, you will have a screen with lots of options. One is called “Simple Passcode”—switch that to “Off” (the Simple Passcode means using a simple 4-digit number). Once you switch Simple Passcode to “Off” you can have longer and more complex passcodes.
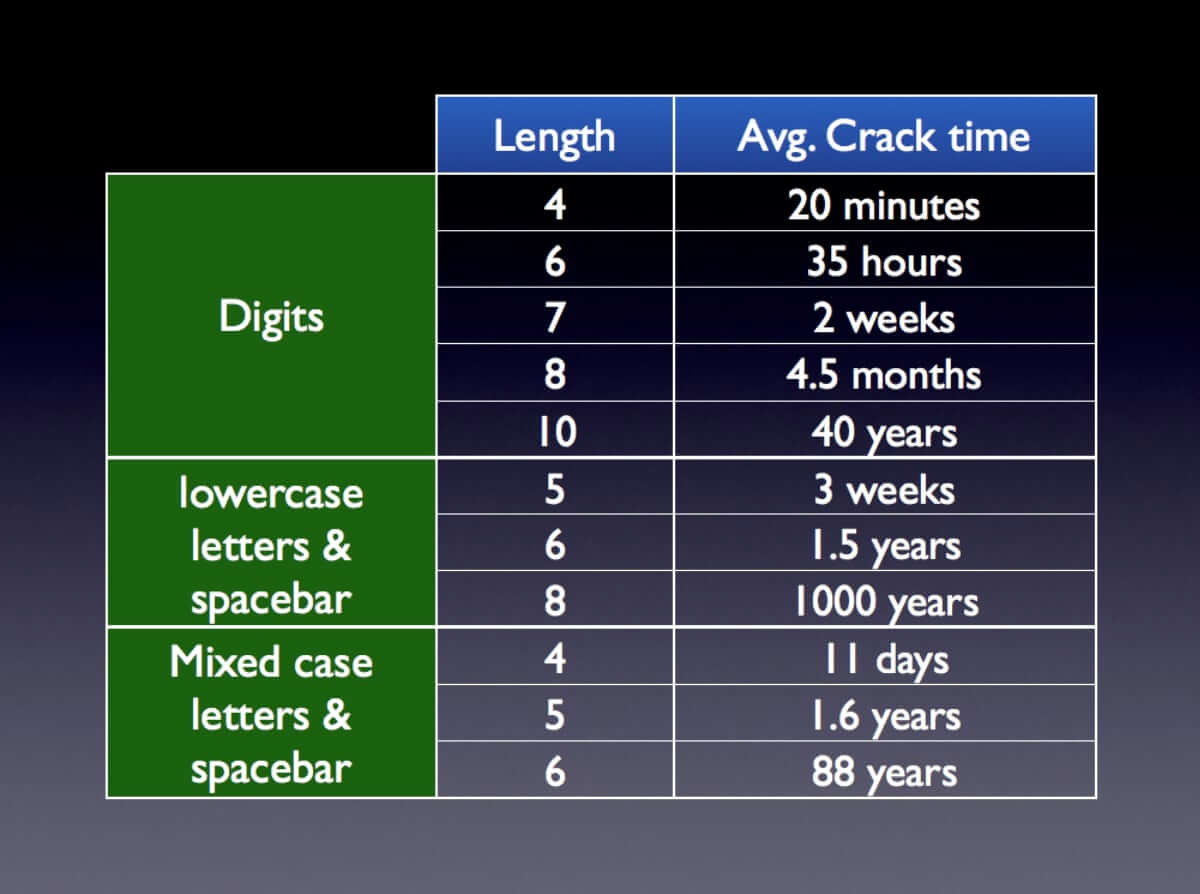
Let’s suppose that you wanted to use a six digit passcode. It would take almost three days to attempt all one million possible six digit passcodes. The average crack time would be half that, at about 35 hours. All the while, the phone needs to be attached to the attacker’s computer. For an eight digit passcode, it would take on average about four and a half months to crack. Each additional digit multiplies the attack time by ten.
If you want to use just lowercase letters and the space key, then with a five letter passcode it would take about three weeks to guess, and for six lowercase letters it would take about a year and a half on average. Each additional letter (or space) multiplies the crack time by 27.
The table below gives some sample average crack times. Assuming that your passcode is random, I count 27 possible lowercase “letters” (26 letters, plus the spacebar) and 53 mixed case “letters” (52 letters, plus the space bar). Although we don’t know how XRY guesses, Elcomsoft has previously advertised that when confronted with a non-simple passcode, their system will try some commonly used non-simple passwords first.
So what kind of passcode is right for me?
When trying to figure out what the best kind of passcode works for you, there are a couple of things to keep in mind. The first one is that for someone to launch this attack they need to be in full possession of your phone during the whole time. The attacker can’t just grab your phone briefly and then do the rest of the attack later. So you need to think realistically about how much time and effort someone would put into getting at your data.
Also remember that this is just to get at your device’s passcode. It is not about your 1Password data which is protected separately in a number of ways, including your Master Password.
You must consider how easy the passcode is for you to enter. One very convenient feature of iOS is that if your passcode is digits only, you will be presented with a numeric keypad, making it much easier and quicker to enter. Likewise, if you keep your passphrase to lowercase letters only, you don’t have to shift keyboards. The passcode that I’ve personally been using falls into the ‘months to crack’ category. Your choice may be different.
What about 1Password data?
Your 1Password data is protected by several layers, the device passcode is only one of them. iOS prevents one application from seeing the data belonging to another application on the device. This can also be a layer of defense, but it is not one which will withstand most jailbreaks.
So finally we come to your 1Password Master Password for the data on your device. This is the final layer of protection. Note that if you use a 4-digit 1Password unlock code, it is just a convenience feature to allow you to do some things within 1Password without having to enter your full Master Password; it is not intended to be a meaningful layer of security.
Put simply: you should use the longest master password on your device that you are comfortable typing regularly. If it is a real chore to type, you won’t use 1Password enough to get its security benefits. Because typing on a desktop system, an iPhone, and an iPad are very different experiences, we have set things up so that you can have a different Master Password for each. The Master Password that I use on Mac and Windows is complex enough to be entirely unusable on an iPhone. This means, however, that my Master Password on my iPhone and iPad are substantially weaker than what I use on the desktops, which brings us back to why I am concerned with overall security of iOS devices.
As we’ve often said before, security is a process, not a product. So look for further security enhancements in 1Password for iOS in the not too distant future. As usual, I don’t want to say anything more specific until this is delivered.
Other claims in reports about XRY
One the the most frightening paragraphs from the Forbes article on the XRY demo reads:
As the video shows, […] XRY can quickly crack an iOS or Android phone’s passcode, dump its data to a PC, decrypt it, and display information like the user’s GPS location, files, call logs, contacts, messages, even a log of its keystrokes.
While it is true that the demonstration video suggests that XRY can do most of that, I am far from convinced that it actually exhibits those capabilities, at least not as stated in those words.
I have no hands-on experience with XRY or any information that isn’t publicly listed on the Micro Systemation website, so my comments here are necessarily speculative.
“Quickly crack passcodes”
As discussed above, there is absolutely no indication from the video that XRY can do much better than four guesses per second when cracking passcodes. It would be a truly major break(through) if they either found a way to defeat PBKDF2 (in which case it wouldn’t just be phones that they could go after) or discovered a way to perform these passcode trials off-line. Such breakthroughs would be widely trumpeted, and they would have been able to perform a very different demonstration. The fact that their target passcode was “0000” only reinforces my view that there is no breakthrough.
Note that they might be able to get a slightly better crack rate on an iPhone 4, running iOS 4. But iOS 5 contains mechanisms to set the PBKDF2 iterations appropriately for the hardware it is running on. It’s worth noting that they used iOS 4 on an iPhone 4 in their demonstration.
Display user’s GPS location”
In the video we are told that they found some “google maps data”. Whether or not this is a place that the phone has been is left entirely unclear. Because there were only a couple of such data items listed, I am skeptical that it does represent actual phone locations. There also was a bit of a kerfuffle about a year ago when it was believed that Apple tracks an iPhone’s location. As it turned out, that wasn’t quite what was going on. It doesn’t appear from the video that the location data they are getting is anything like what is in the location cache database.
“dump files”
The video shows the inspection of a file called “keychain-2.db”, which seems scary enough, but there is no reason to believe that data within that file can be decrypted. However, with a sufficiently jailbroken device with the passcode in hand, it is plausible that the information in there can be decrypted. They then go on to “the log file” and show that the device passcode is in it. What may not be immediately clear is that this is log file is created from their own password cracking process.
The log file that is being read there was actually created by XRY itself. There will, of course, be sensitive data (such as contact information) available to them after a cracking the passcode, but the demonstration does not illustrate those examples.
“logs of its keystrokes”
I am not certain where the impression of a keystroke logger comes from. I saw no implication of that from the video. Perhaps it is the discovery of a swipe pattern on the Android 2.3.3 (Gingerbread) system that was shown. Note that there have been two major releases of Android (Honeycomb and Ice Cream Sandwich) since the version used in the demonstration.
A large grain of salt
I am not in any way disputing that tools like XRY and the Elcomsoft toolkit can be useful for law enforcement. And I am certainly not suggesting that these shouldn’t be worrying to anyone concerned about their data and privacy. My point is simply that sensational claims about security issues need to be examined carefully. The more we examine some of the claims about XRY, the less frightening they become.
In sum
This was a long article, so I’d like to highlight a few main points
- Press reports based on marketing videos are not the most reliable way to to understand security threats.
- XRY, in particular, illustrates no threat that we haven’t addressed before. In particular, your 1Password data on your phone is encrypted and protected by your 1Password master password even if your phone becomes entirely compromised.
- It is probably time to move beyond simple 4-digit pass codes for your iOS device. If you use a longer sequences of digits, it will still be quick and easy to enter. For advice on what to do if your iThingy gets stolen, please see an earlier post that includes such advice.
- By adopting reasonable security practices, such as using 1Password and moving beyond a 4-digit device passcode, we can enjoy on the benefits of our mobile devices without having to live in fear of what happens to our data if someone gets a hold of the device.
Update: Micro Systemation have removed their demonstration video from YouTube. Also someone more familiar with the jailbreaking technology has reported on this and points out that the tools at XRY uses do not work with the iPhone 4S, the iPad 2, or the new iPad. It also confirms my view of the password cracking time.

 by Jeffrey Goldberg on
by Jeffrey Goldberg on
