1Password Shell Plugins brings the security and ease of use of biometrics to every tool in your terminal.
I love Touch ID. When I use it to log in to a site or authorize a purchase, authentication just kind of happens. It doesn’t feel futuristic anymore, but it does feel like the present. It’s the modern computing experience.
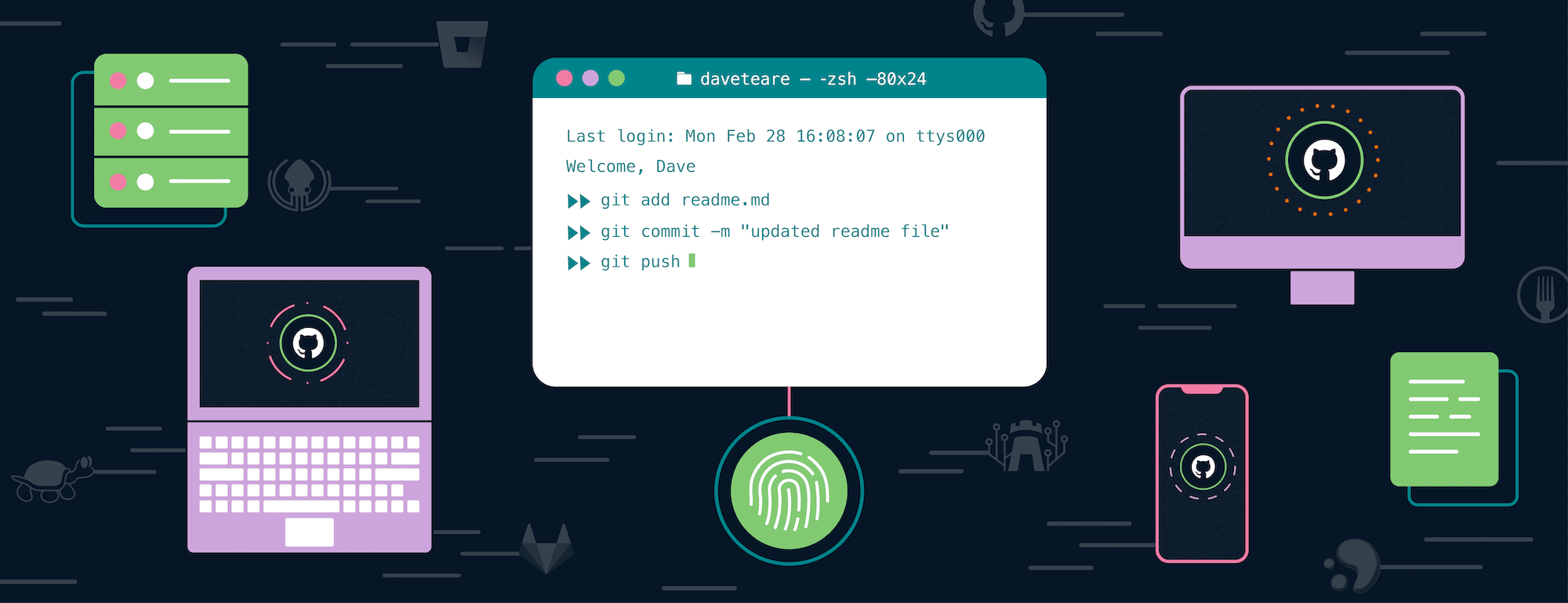
Then I open my terminal, and I’m transported right back to the past. Why can’t devs have that modern experience?
I know I’m not alone. When we introduced Touch ID support for 1Password CLI 2.0, one of the most frequent pieces of feedback we heard was: Can we have touch ID for all CLIs?
So, about that.
Introducing 1Password Shell Plugins
We use CLIs to perform quick actions from the comfort of our terminals and automate recurring tasks. You might use the GitLab CLI to submit your code in a merge request, so the team can review it and include it in the next release, for example. Many other developer platforms like AWS, Stripe, Sentry, and CircleCI offer CLIs as well.
Connecting a CLI to your online account often involves generating API access keys in a browser, then pasting those values into the terminal. Those credentials are usually saved in a plaintext config file that gives the CLI persistent access to your account, even after reboots. But if an attacker or process gains access to your system, they have the same level of access to your account that you do.
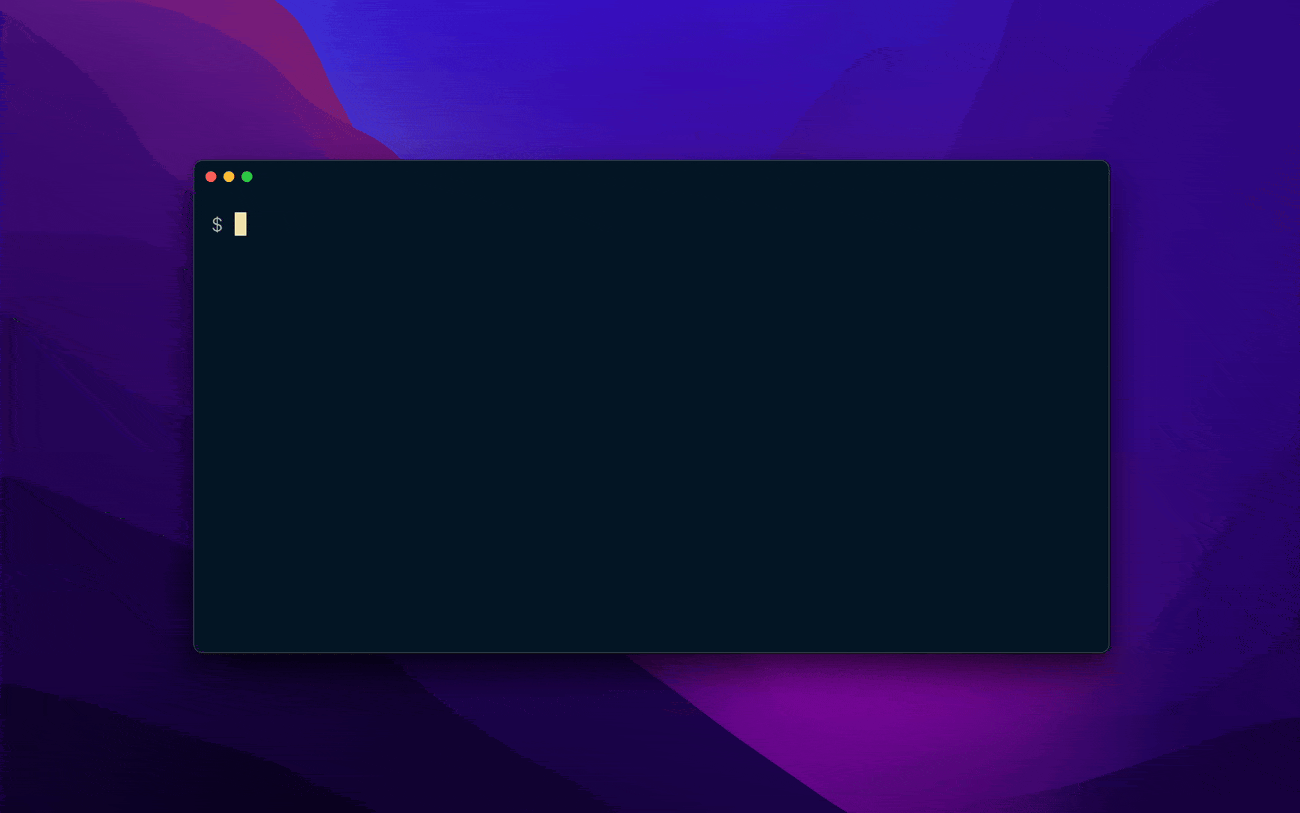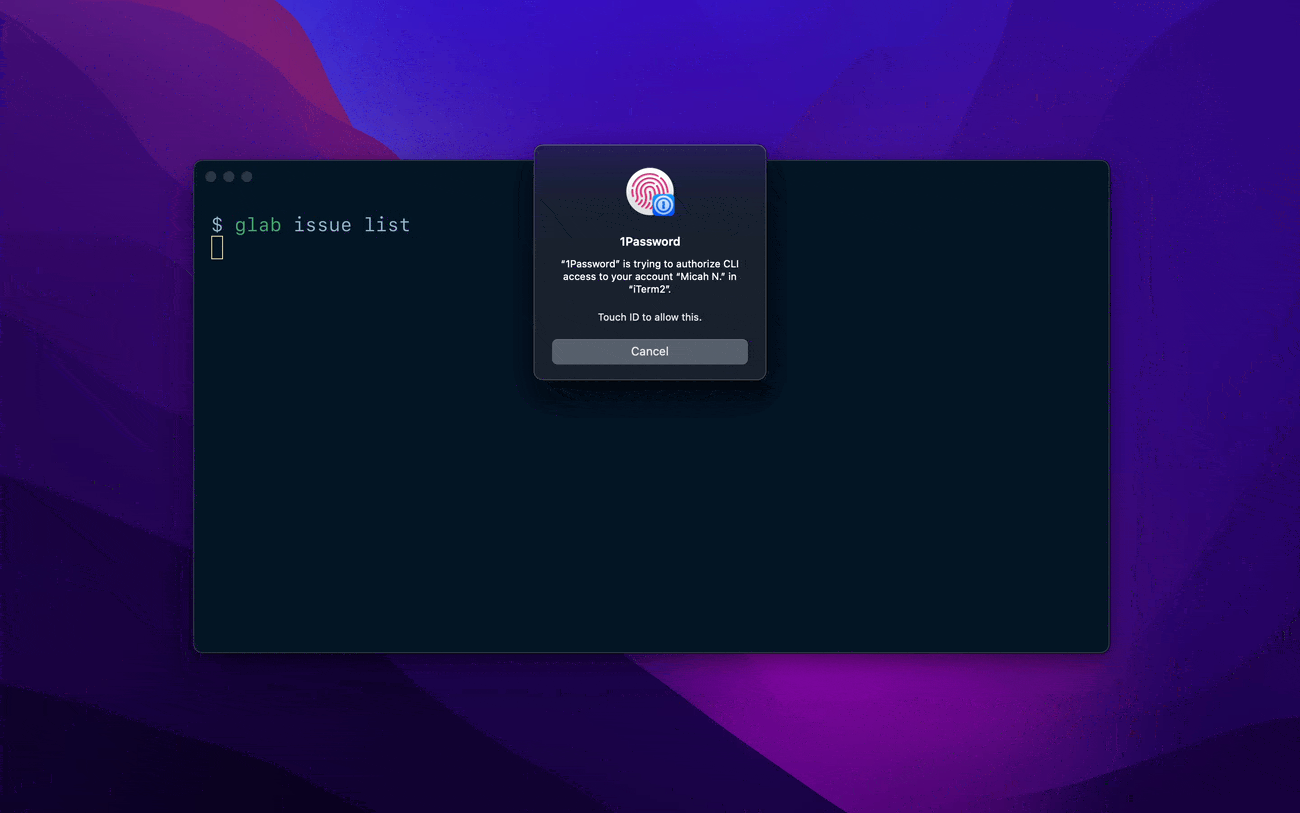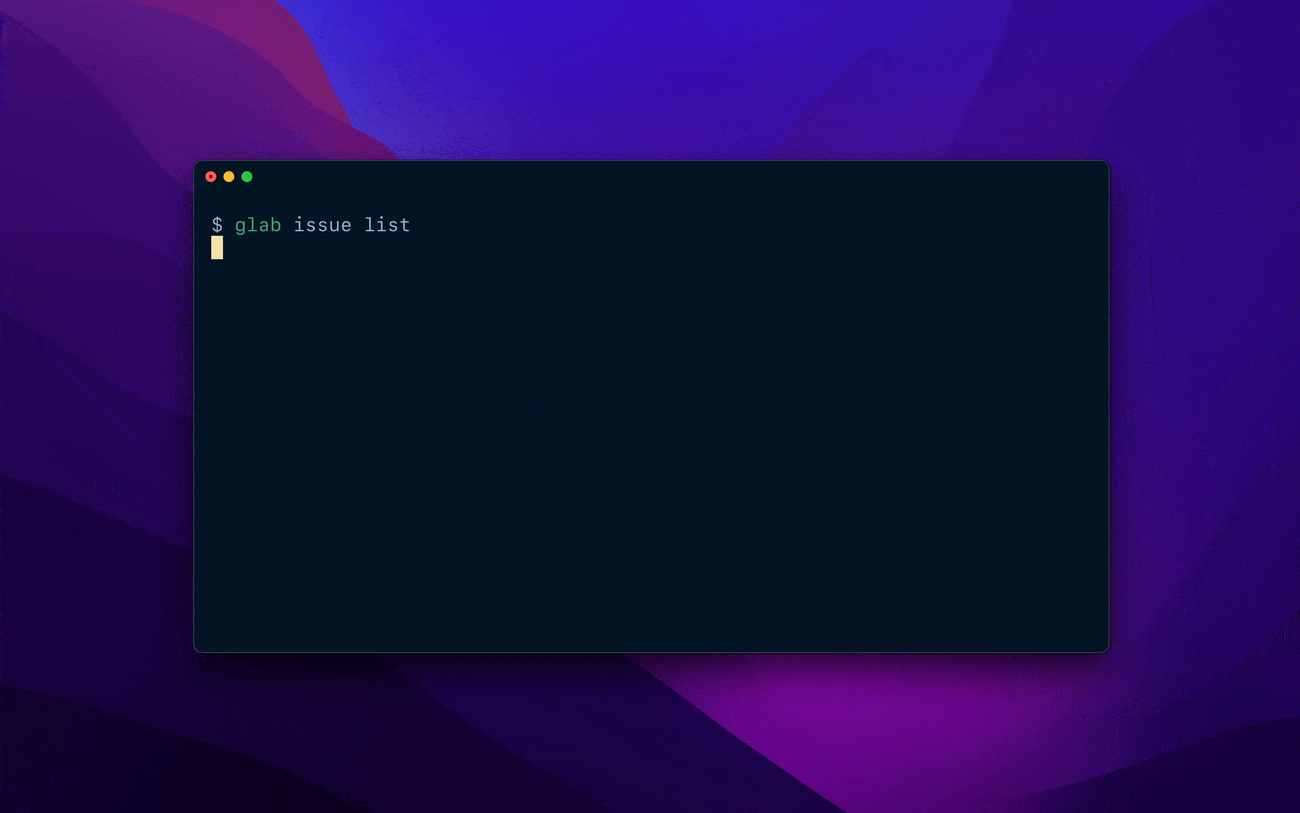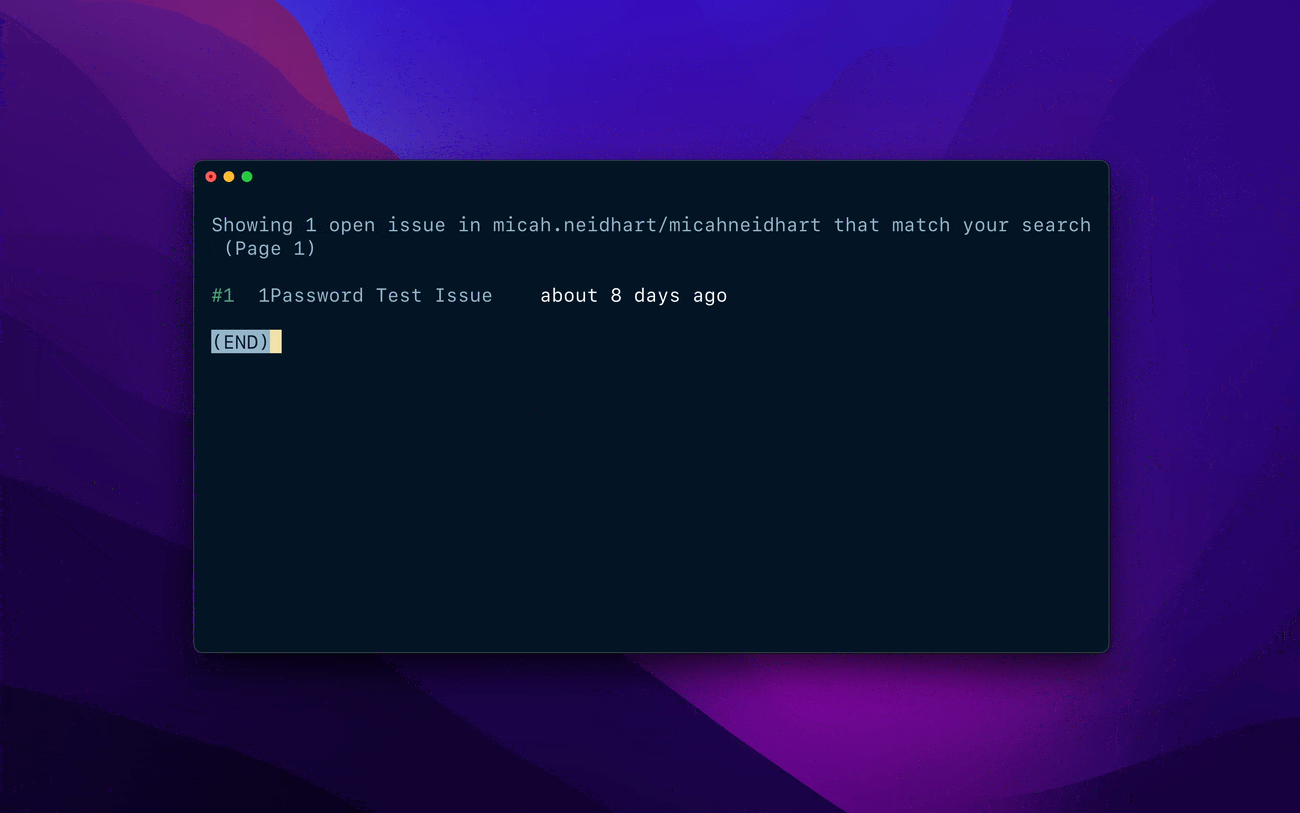
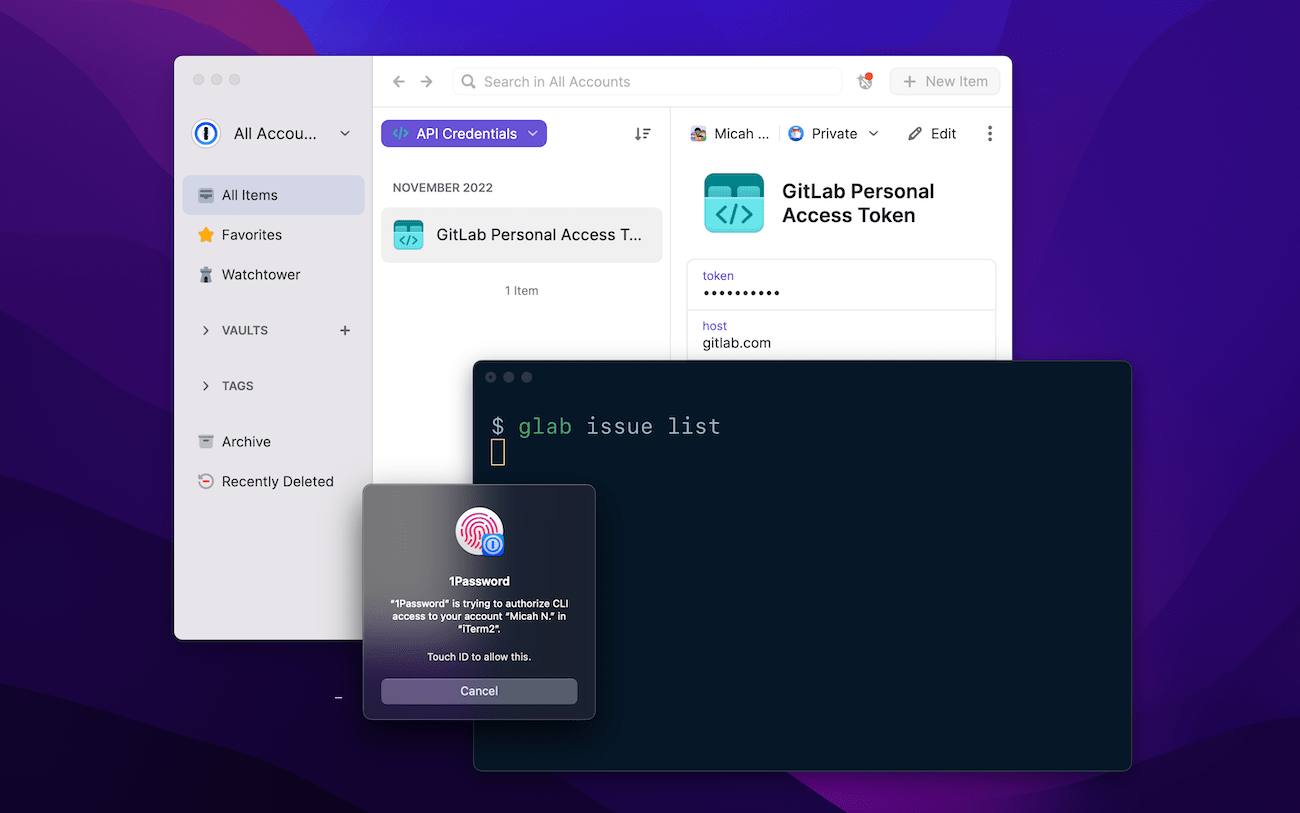
We built 1Password Shell Plugins so you can securely store all of your access keys in encrypted 1Password vaults, rather than on disk. When you use a Shell Plugin for a particular service, access to the associated API keys is restricted to your specific terminal session.
Because they’re saved in 1Password, you can securely sign in to any CLI with your fingerprint or another form of biometrics. If the service supports it, MFA codes can be filled automatically – so there’s no need to pull out your phone multiple times every day.
In fact, there’s no need to type anything. No plaintext, no typing passwords, no hassle – you can stay in the zone and focus on the task at hand.
Extensibility built in
We’ve already built Shell Plugins for many popular CLIs, including:
- GitLab
- CircleCI
- Amazon Web Services
- Sentry (Get $240 in Sentry credits with code “1Password”)
- Stripe
- Twilio
- GitHub
There are many more pre-built integrations, but you’re not limited to the ones we built. You can build your own, for any CLI.
Shell Plugins are fully extensible and aren’t restricted to specific services. If you don’t see an integration you need, you can join the open source project (currently in beta) and contribute your own.
Want to add MFA support to an existing Shell Plugin? You can do that too.
Many of our users rely on GitLab to shorten code review cycles, increase their developer productivity and strengthen overall security at every step. 1Password’s latest rollout is an important development in that last bucket. Launching Shell Plugins will help ensure developers can access our tools in their terminals as quickly and securely as possible. – Kai Armstrong, senior product manager, GitLab
Your keys, but portable
Storing your keys in 1Password means you can use them everywhere. If you switch to a different machine, system, or environment, the process is exactly the same.
Just install and configure Shell Plugins on your machine, then use biometrics to grant access to your key in 1Password. If the plugin supports MFA, you can use 1Password to autofill the codes.
This all makes setup, developer onboarding, and collaboration simpler. If new teammates are in the relevant group in 1Password, they already have the permissions they need to access the shared credentials and contribute immediately. All they have to do is install the 1Password CLI and the appropriate Shell Plugins.
How Shell Plugins work
Once you’ve set up 1Password CLI, you can install a supported Shell Plugin with a single command. For example, to install the plugin for GitLab, you would run:
op plugin init glab
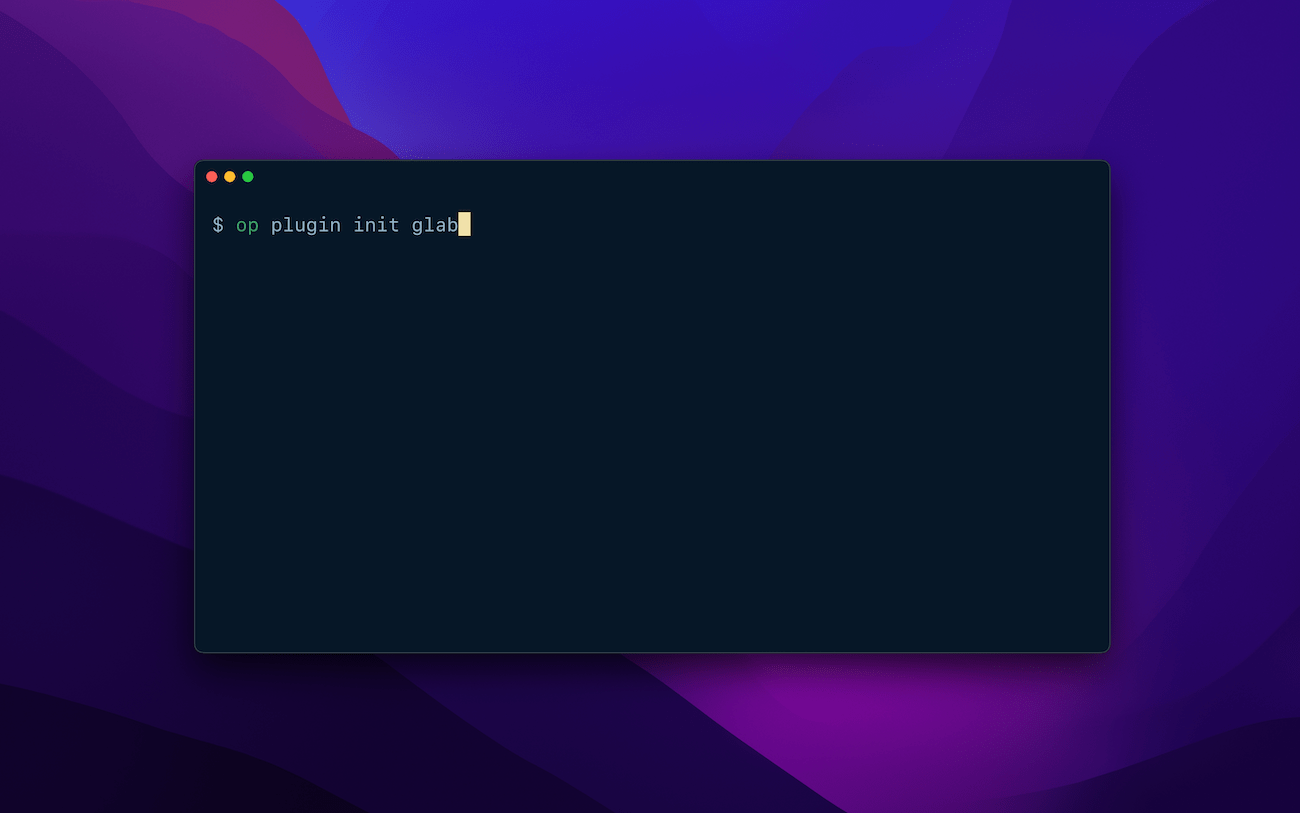
During the configuration process, you can import existing credentials from your config file or create new credentials in 1Password.
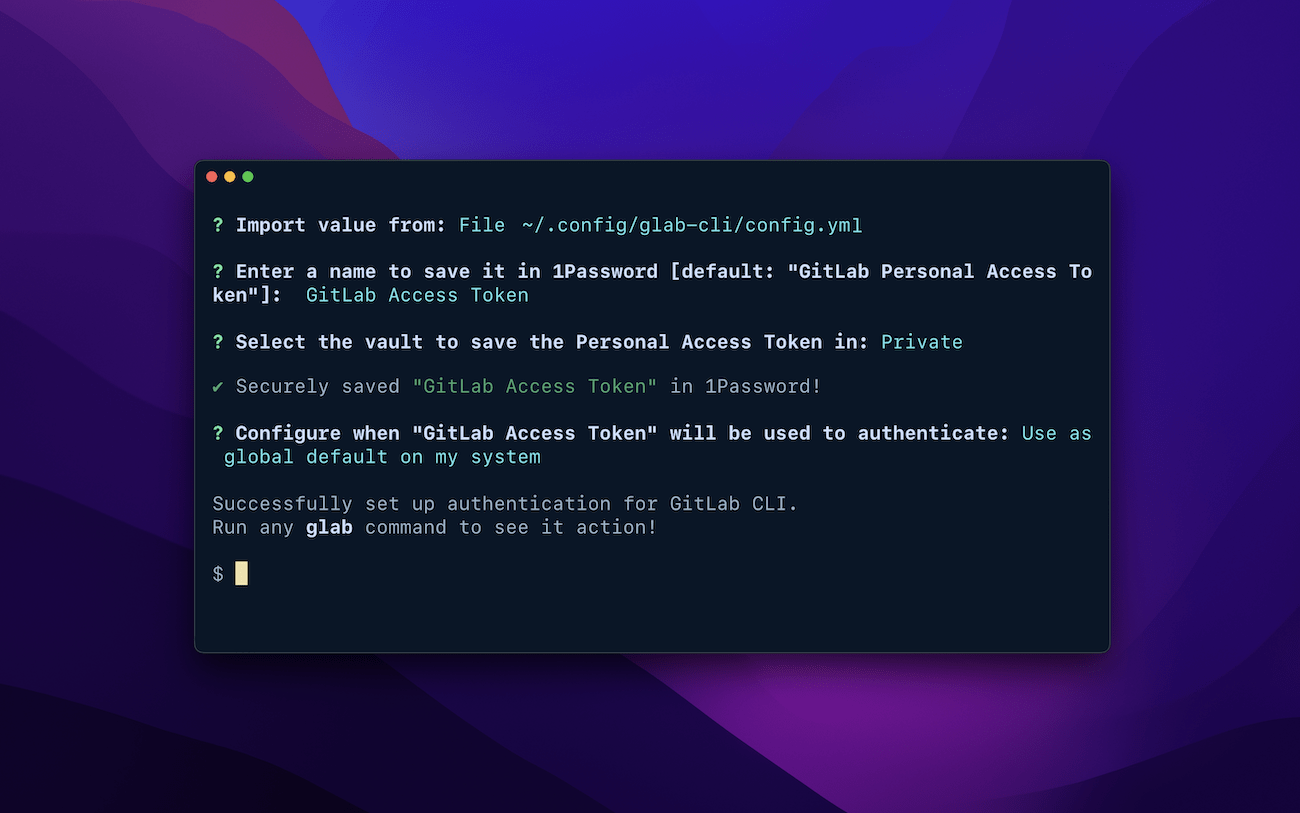
At this point, your credentials are safely stored in 1Password, so you can remove them from your disk.
Check out the developer docs to learn more about Shell Plugins.
Introducing CI/CD integrations
One more thing. When you’re setting up a CI/CD workflow, you often need to manually enter secrets by visiting the settings page of the tool you’re using. But now you can store those secrets in 1Password, too.
You can access them directly within your CI/CD tools – and reference their location in 1Password directly within the job that requires them – via new integrations for:
Again, feel free to jump into the documentation to get started.
Securing the software development life cycle
Our goal is to bring this same level of security and ease of use to the entire software development life cycle. My colleague, Marc Mackenbach, has written about how far the developer user experience has to go before it catches up with the consumer experience in terms of both security and UX.
We’re working on that. Check out 1Password.com/developers for a quick overview of everything we’re building to secure developer workflows. In the meantime, feel free to start exploring the Shell Plugins documentation.
And maybe keep your phone in your pocket. You won’t need it nearly as often anymore. 😉
 by Simon Barendse on
by Simon Barendse on


Tweet about this post