We know that many businesses use identity providers like Okta, Rippling and Azure Active Directory to control what their employees have access to. That’s why we built the 1Password SCIM bridge — a way to connect these services with our enterprise password manager. It streamlines common administrator tasks, such as setting up new employees with a 1Password account and granting them access to specific groups.
To sync everything up, all of our customers that want to leverage automated provisioning deploy the SCIM bridge on one of their own servers. But that made us ask the question: what would happen if a SCIM bridge went down? Could we do more to help companies diagnose and fix the problem?
To solve this issue, we decided to build health monitoring, a tool that administrators can use to quickly check on their SCIM bridge and narrow down any technical issues. We had a good idea of how this should work, but we’re in the password management business, not the server monitoring business. Building a service from scratch would have been a poor use of our time, so we partnered with a company that’s an expert in server monitoring: Checkly.
Protecting customer data
The challenge with this partnership was ensuring that we didn’t compromise on our commitment to keeping customer information private. That meant limiting Checkly’s access to the absolute minimum needed to deliver a functional service.
To achieve this balance we started with the following:
- We use a random unique identifier to link accounts to Checkly checks.
- We added a second authentication token to the SCIM bridge that can only be used to hit its health check endpoint.
This means that all Checkly has access to is the domain name where the SCIM bridge resides and an authentication token that is only useful for health checks. Checkly does not even have the ability to notify customers directly about issues. Instead, Checkly notifies our server, which then has the responsibility of notifying the customer.
Our health check endpoint is designed to return information about the different components that make up the SCIM bridge. Administrators can find this analysis by navigating to the domain or IP address where the SCIM bridge was deployed and submitting their bearer token.
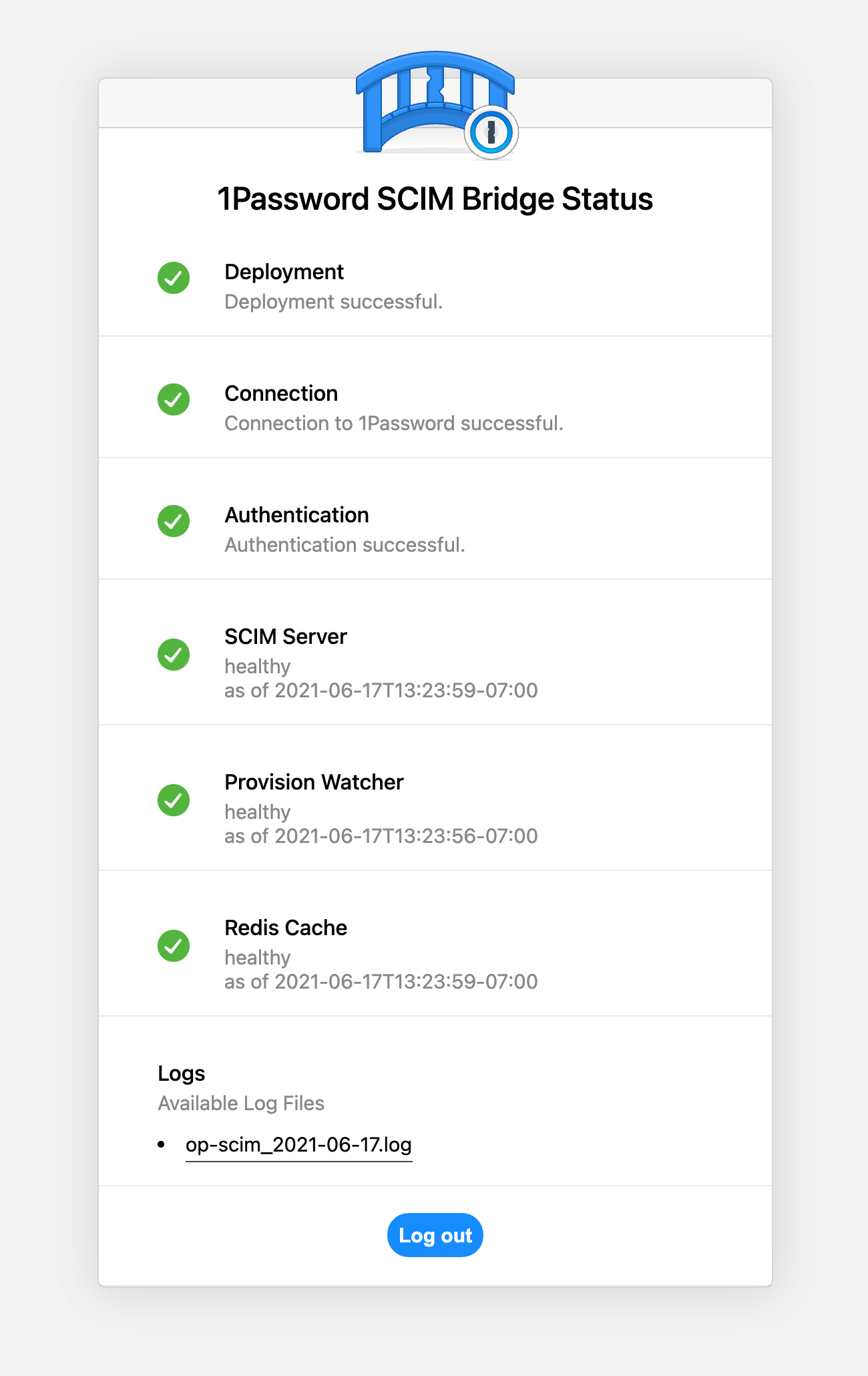
They can also use 1Password in the browser to check on the status of their SCIM bridge deployment.
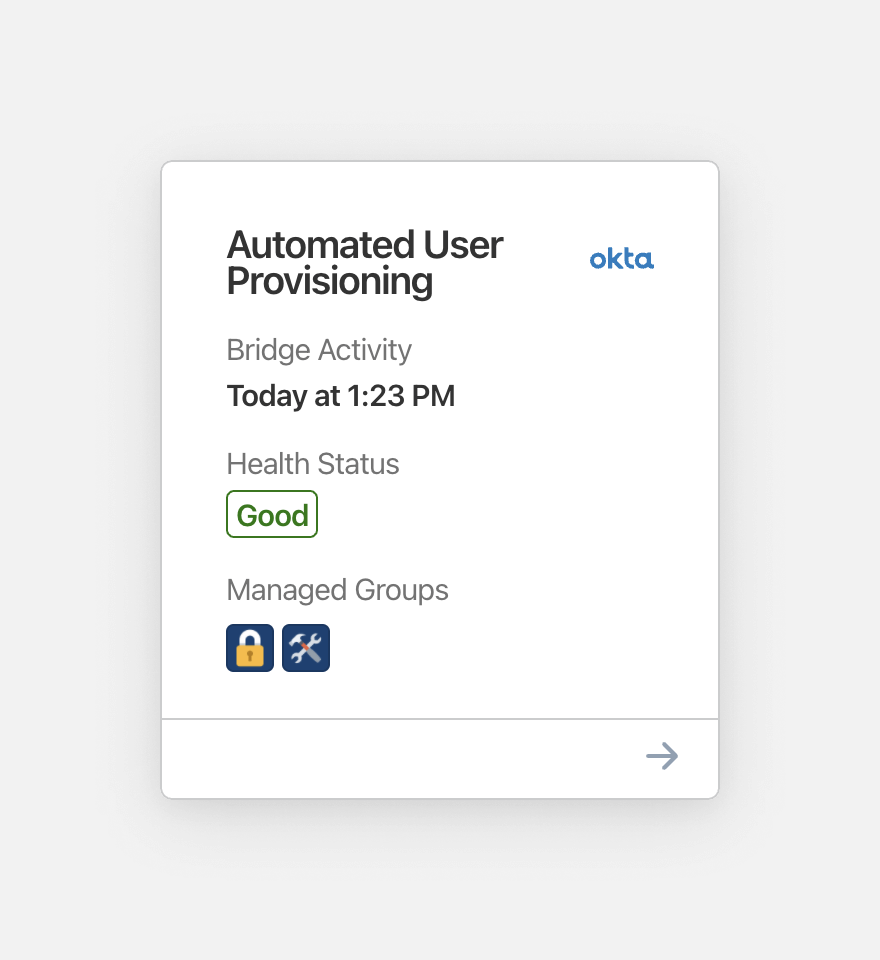
If a health check does not complete successfully, the administrator will get an email about it within minutes. The message will break down every component that encountered an error. In addition, the administrator is notified when Checkly was unable to reach the SCIM bridge and determine its current health status. This is useful when the monitoring domain was entered incorrectly or when there are other factors preventing Checkly from contacting the SCIM bridge. Another email is sent when the problem has been resolved.
The right balance
With Checkly, we’ve developed a solution that helps customers keep their user provisioning workflow running smoothly. But more importantly, we built it in a way that protects and respects our customers’ privacy.
That wasn’t the easy option. But we did it this way because it’s the right thing to do. It’s a perfect example of how we operate as a company — serving you, and improving our product, but never at the expense of privacy or security.

 by De Ville Weppenaar on
by De Ville Weppenaar on


Tweet about this post