Pulumi customers can secure and simplify their secrets management workflows with a new integration built for 1Password.
Pulumi is an infrastructure as code (IaC) platform that enables developers to manage and deploy cloud infrastructure using familiar programming languages like Typescript, Python, Go, C#, Java, and Yaml.
Pulumi recently announced the general availability of Pulumi Environments, Secrets and Configuration (Pulumi ESC), their secrets management and orchestration solution. Pulumi ESC helps organizations control the sprawl of secrets that occurs when companies grow by enabling them to centralize their secrets management across all of their applications and development teams. Developers can easily access, share, and manage secrets securely on any cloud, using their favorite programming languages.
Pulumi built the new Pulumi ESC integration for 1Password using the 1Password Go SDK. Pulumi reached out earlier this year about building the integration in response to customer requests and was one of the first technology partners to participate in the 1Password SDKs beta. Of course, being fans of Pulumi ourselves, we were happy to work with them on the integration.
To see it in action, join us for a live workshop on September 25, 2024. 1Password Developer Relations Manager Phil Johnston and Pulumi Solutions Architect Diana Esteves will cover how to work with Pulumi ESC and 1Password to make secrets available to approved team members and deployments, securely.
How it works
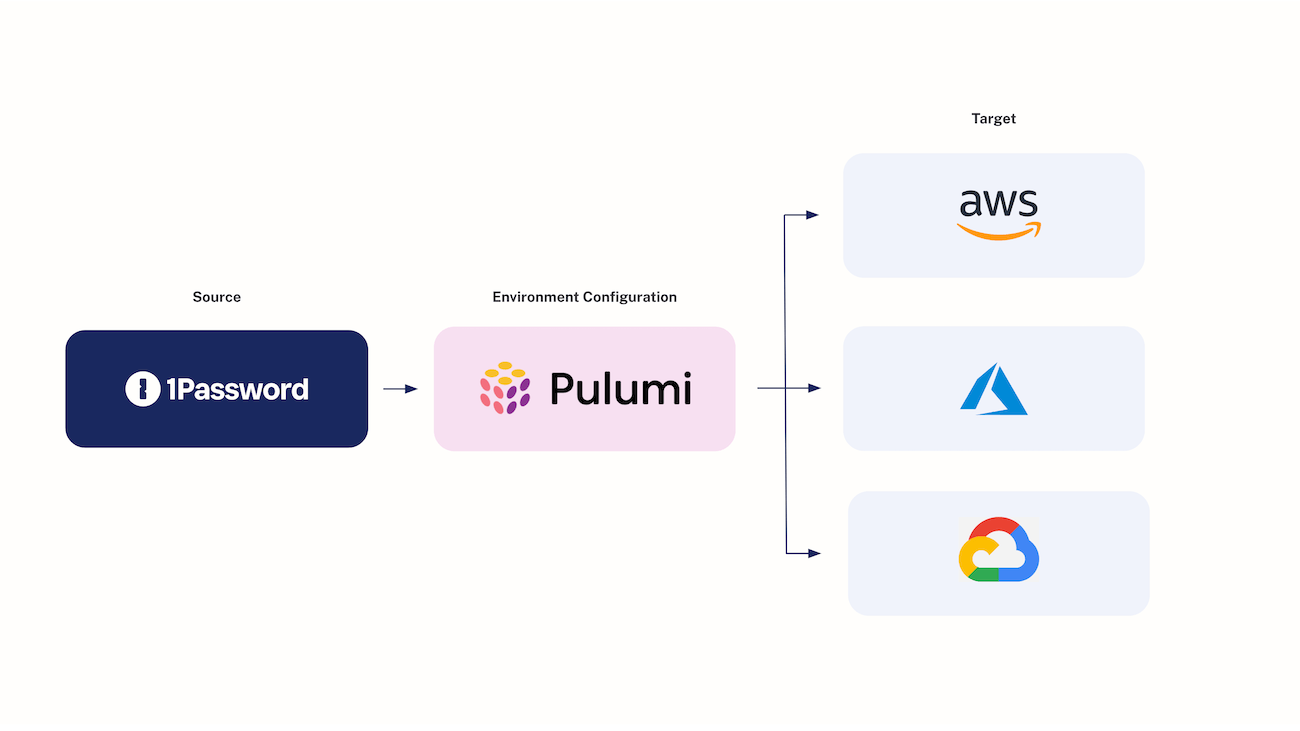
With Pulumi ESC, platform engineering teams can use 1Password as a central store for API keys, database credentials, and other secrets used in their applications and infrastructure while leveraging cloud platform infrastructure (e.g., AWS Secrets Manager, Azure Key Vault, etc.) as the execution environment.
It takes a little scripting for Pulumi ESC to orchestrate secrets across multiple cloud environments while maintaining 1Password as the source of truth for every team.
The following is an example of an ESC script in YAML with 1Password as the source and AWS as the destination:
values:
1password:
secrets:
fn::open::1password-secrets:
login:
serviceAccountToken:
fn::secret: ops_eyJzaWduSW5B..[Redacted]
get:
aws-access-key:
ref: op://Engineering/aws-cli-creds/access-key
aws-secret-access-key:
ref: op://Engineering/aws-cli-creds/secret-access-key
environmentVariables:
AWS_ACCESS_KEY_ID: ${1password.secrets.aws-access-key}
AWS_SECRET_ACCESS_KEY: ${1password.secrets.aws-secret-access-key}
Pulumi ESC also offers a UI-driven method to set up the configuration required to pull sensitive information from 1Password. Check out the Pulumi ESC docs and the Pulumi ESC launch blog post for more information.
Easy and secure secrets management
Today’s cloud environments require many configurations – including secrets like API keys, database credentials, etc. Every team stores configuration settings like these in different locations, from secret managers to plaintext configuration files. This secret sprawl results in operational bottlenecks, misconfigurations, and security breaches.
With 1Password and Pulumi ESC, platform engineering teams can:
- Stop secret sprawl: Use Pulumi ESC to access, share, and manage secrets in 1Password and consume in any application, tool, or CI/CD platform.
- Trust (and prove) your secrets are secure: With Pulumi ESC, every environment can be locked down with role-based access controls (RBAC) and versioned with all changes fully logged for auditing.
- Ditch
.envfiles: No more storing secrets in plaintext on local disks. Developers can easily access secrets stored in 1Password via Pulumi ESC’s CLI, API, Typescript, Python, and Go SDKs, and the Pulumi Cloud UI.
Expanded support for infrastructure as code (IaC) practices
Infrastructure as Code (IaC) tools enable the automation and management of cloud infrastructure, allowing for consistent, repeatable, and scalable deployments. They are a critical component of modern infrastructure and engineering practices.
At 1Password, we’re excited to partner with Pulumi to expand our developer integrations and better support modern infrastructure teams and workflows. The new integration with Pulumi ESC makes it easier to adopt 1Password as the source of truth while integrating with existing tools and systems across different cloud environments.
Getting started
Learn how to start managing developer secrets with Pulumi ESC and 1Password, or explore the Pulumi ESC documentation for more information.
For a hands-on demonstration, sign up for the live workshop on September 25, 2024.

 by Andrew Stiefel on
by Andrew Stiefel on


