Just the place for a Snark! I have said it twice: That alone should encourage the crew. Just the place for a Snark! I have said it thrice: What I tell you three times is true.
— Lewis Carroll “The Hunting of the Snark”
In Part 1 of this series I discussed how your 1Password data may (or may not) be threatened if your computer gets infected with some kind of malware, particularly Flashback. Of course, it is better for your computer to not be infected in the first place, so in this article I focus on a few tips to help keep your computer safe from malware. Part 3 will outline a way of thinking about the differences and similarities in the threats from malware on Mac and Windows. Before I get into the list of tips that you can do to help keep your computer malware free, I’d like to say a few words about a few words. I hate the word “malware”; it’s awkward and ugly. Unfortunately that is the word we have. Words like “virus”, “worm”, “trojan”, “drive-by” and so on refer to how the particular piece of malicious software spreads. It tells us nothing about what they do. I will use the term “infected” to refer to a computer system that has some malware installed and functional on it.
As I said twice before in Part 1 (and, really, as we’ve always said), the most important thing you can do to specifically protect your 1Password data is to use a good Master Password. The proof is complete if only I’ve stated it thrice.
1. Keep your software up to date
The single most important thing you can do to protect against malware is to keep your software up to date.

The large majority of system compromises are through vulnerabilities that the software vender has already released a fix for. Flashback was unusual is that the Java vulnerability that was exploited had not already been patched (although it had been public for a while).
Let me introduce a few terms. A “vulnerability” is a flaw in a system (either a bug or a design error) that allows something to breach security. A “patched vulnerability” is a vulnerability that has been fixed by the supplier and the fixed version is available to users. An “unpatched vulnerability” is one for which there is no fix from the vendor yet. This distinction is important because research shows that when computers are compromised through these sorts of vulnerabilities, the large majority of them are through patched vulnerabilities. That is, if the user had kept their software up to date, they would not have become a victim.
Some people use these terms a bit differently. You will sometimes hear “zero day” to refer to what I am calling an unpatched vulnerability. But I reserve that term to refer to vulnerabilities that the software provider isn’t even aware of.
Flashback did not exploit a vulnerability that Apple didn’t know about. The particular bug in Java had been done for months before Flashback started to exploit it. Instead, Flashback exploited a vulnerability that Apple was well aware of, but had not yet fixed. Flashback, then, is an exception to my claim that keeping your software up to date will keep your computer malware free. I’ll come back to this in the third article in the series.
So if Flashback actually goes against my point, why do I insist that keeping systems and software up-to-date is the most important thing you can do to prevent infection? I’m basing my claim on a great deal of research on this question, but I will draw most of my examples from Microsoft Security Intelligence Report volume 11 (PDF). It contains the clearest arguments and data.
The Microsoft report offers the example of the number of new infected Windows systems through a particular vulnerability in Adobe’s Flash Player and Adobe Reader. The red part of the graph covers the time between when the malware was exploiting the vulnerability and the time that Adobe first issued a fix for it. As you see, there is a decline in infection rates shortly after Adobe issued updates for Flash on April 15, 2011 and for Reader on April 21 a week later.
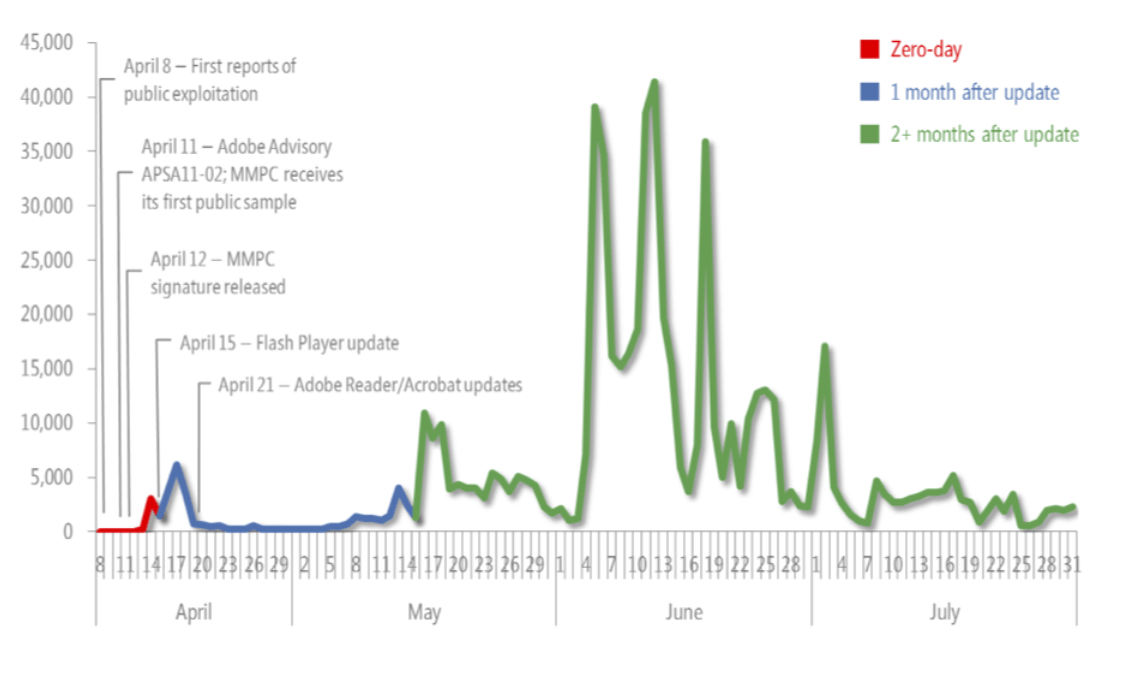
But as you look at what happened two months after Adobe fixed the vulnerability (the green part of the graph), there is an enormous resurgence of the malware. The number of systems infected before Adobe fixed the vulnerability is tiny compared the infections that happened much later. This particular example illustrates the general pattern. Most system compromises through vulnerabilities could have easily been avoided if people kept their software up to date.
That particular infection is just one example to illustrate what is a very common infection pattern. Indeed, what may be the most widely spread malware on Windows—Conficker—is still infecting Windows systems more than five years after the vulnerabilities that it exploits have been fixed by Microsoft. Keep in mind that, once it gets onto a corporate network in the first place, much of Conficker’s ability to spread is to just find users on the network with weak passwords. Still, it does help illustrate the problem of people not keeping their software up to date, as the password guessing tactic only works after Conficker makes it onto the local network by some other means.
How to keep things up to date
On the Mac, Leopard and Tiger are no longer being updated. If you are using one of those systems, please move to Snow Leopard or Lion quickly. And if history is much of a guide, Snow Leopard will lose support within a few months after the release of Mountain Lion, which Apple has scheduled for summer 2012. As of this week, Mozilla has discontinued support for Firefox 3.6. In short: don’t use unsupported operating systems or web browsers. Just don’t.
On Windows, Microsoft still provides security updates for Windows XP (Server Pack 2), but they do so only reluctantly. They had wanted to end support in 2010, but are now continuing it through April 2014. If you are using Windows XP, you shouldn’t wait until 2014. The security changes between XP (released over a decade ago) and Vista are enormous, not to mention Windows 7 came out in 2009, and Windows 8 is almost upon us.
The operating systems are probably the easiest thing to keep up to date because they are typically configured to periodically check for available updates. But the software you install later can, traditionally, come from many different places, so it is usually harder to maintain. An increasing amount of software will automatically update itself, though, and Google Chrome is one notable example, with more browsers following suit. Some software will periodically check whether it needs to be updated and alert you, but new software delivery services like Apple’s App Store and Microsoft’s upcoming Windows Store can do all that heavy lifting for you.
For your most important software, it is vital to have some sort of easy or automatic way of checking for and install updates. In terms of security, here is an ordered list of what I think are the most important things to keep up to date:
- Operating Systems. You need to schedule Software Update (on the Mac) or Windows Update (on Windows) to check for updates automatically.
- Web browsers. In each web browser, you will be able to configure its updating habits in its preferences.
- Web browser plug-ins. These are the programs – such as Adobe Flash Player, Adobe Reader (on Windows), Java, and Silverlight – that are used to open certain kinds “in the browser” that the browser itself can’t handle natively.
- Email software. If you are using the email software that comes with your operating system (Mail.app or Outlook), then they will be updated with the operating system. But if you use a third party mail program, then you need to make sure that that is kept up to date.
- Anything that opens files that you did not create yourself. Whatever software you use to look at pictures, read word processor documents, work with spreadsheets, or listen to music files must be kept up to date.
- 1Password. Well, really any software that has to do with your security. 1Password automatically checks for updates after it is launched and will only check periodically in case you are like me and never relaunch it because you never close it. You can configure 1Password’s updating behavior in Preferences > Updates. You should also keep the 1Password browser extensions up to date, which is typically done automatically right within the browser.
That’s a lot of work to keep up with, but fortunately an increasing number of application developers are making updates easier and automatic. Tools like the Mac App Store make it even easier for people to see what needs to be updated. There will be some more discussion of that in Part 3.
2. Back up your data
Backing up your data won’t actually do anything to prevent infection, but it will put you in a much better position to recover from one. Most malware tries to remain undetected so it won’t deliberately crash or destroy your system, but it can still introduce instabilities. Furthermore, there is a form of malware, known as ransomware, which encrypts your data and requires that you pay to get the decryption key.
Most importantly, good backups are a vital part of data security overall. As the saying goes, there are two kinds of computer users: those who have experienced a catastrophic disk failure, and those who will.
3. Pay attention to where your software comes from.
Even if the software and operating system you are using has no technical vulnerabilities that allow an attacker to get malicious software running on your computer, there is still a very simple way that they can get their software installed and running. They can ask you to install and launch it for them.
Of course they don’t say, “Hey, here is some malicious software. Please download, install, and run it.” Instead, they say, “Hey, here’s a free horse riding game! No strings attached!” You can download and install it. Perhaps you enter your administrator password during the installation process. The download may even include a more or less working copy of the horse software.
Lurking inside the harmless game you brought in through your defenses could be enemies. They break out at night, kill your guards, and open the gates so their whole army can rush in.
The horse, standing high on the ramparts, pours out warriors, and Sinon the conqueror exultantly stirs the flames. Others are at the wide-open gates, as many thousands as ever came from great Mycenae: more have blocked the narrow streets with hostile weapons: a line of standing steel with naked flickering blades is ready for the slaughter.
It should not come as a surprise that malware of this sort is called a “Trojan horse,” or just “Trojan.”

I am not for a moment suggesting that you shun all geeks bearing gifts. After all, making great things for people is what we geeks love to do. But along with not keeping software up to date, this a leading way that malicious software can be installed and run on your system.
This is one of the reasons why I’m excited by Gatekeeper, coming in OS X 10.8 Mountain Lion. It won’t be an entire solution to the problem of Trojans, but it may play a substantial part. In short, Gatekeeper will give you control over what apps run on your computer depending on who or where they come from.
4. Virus Scanning?
I’ve left anti-virus scanning for last on my list because I think it plays a distant third to keeping software and systems up to date and paying attention to where you get your software from. As one security researcher quipped, “anti-virus vendors have solved the malware problem so well on Windows that they are now bringing the same magic to the Mac.” On the other hand, it is useful to occasionally (or even regularly) run a scan of files on the system.
There are two ways that anti-virus software can operate. In one mode, they will search through most of the files on your system looking for malware, either periodically or at a time you specify. In the more active mode, they inspect (almost) every file as it gets opened, but this mode can often slow down a system substantially or even make it less stable. (“Less stable” is a euphemism for crashing more.) Opinions about these vary widely (and heatedly). In both modes, the database that the anti-virus software uses needs to be kept very much up-to-date.
One thing to keep in mind is that, although Mac users should probably be more concerned about malware than they are used to (more on that below), they should be wary of reacting to the most alarming headlines, particularly when they are produced by by anti-virus vendors. While some vendors have kept a level head in their discussions, others have engaged in egregious fear mongering based on extremely misleading numbers. It is unfortunate that the least useful information with the most alarming headline is the one that gets the attention.
In any case, with Flashback, everyone should run one of the many free detection and removal tools that have been issued by reputable anti-virus vendors. One of the first was developed by Intego. Even if you have updated your software to fix the vulnerability that Flashback has been exploiting, once your computer is infected it will remain infected until the malware is explicitly removed.
Other tips?
There are load of other things you can do to improve system security. For example, I am a big advocate of not having your main user account be an administrator account. More steps to consider include adjusting firewall settings and using various blockers in web browsers. But the large majority of problems will be avoided simply by keeping software up to date and paying attention to where you get software from. We get diminishing gains in security from the more advanced techniques, particularly in comparison to the gains we get from the basic things that everyone should do.
In Part 3 of this series, I will offer some thoughts on the developing malware situation on the Mac, with a look at what might keep Macs relatively safe or not.

 by Jeffrey Goldberg on
by Jeffrey Goldberg on


Tweet about this post