Omdia, a global analyst and advisory leader, recently released a report called “How Extended Access Management (XAM) closes the gaps in security.” The report outlines the challenges of managing access for the modern workforce and suggests strategies for addressing those challenges.
Omdia defines the challenge areas of access management as:
- App sprawl: The uncontrolled proliferation of applications within an organization, including unsanctioned shadow IT.
- Device sprawl: The explosion of devices accessing corporate resources, including unmanaged BYOD and contractor devices.
- Identity sprawl: The uncontrolled growth of user identities within an organization, including employees, AI agents, contractors, and third-party vendors, each requiring access to various systems.
This confluence of unmanaged access points – spanning users, devices, and applications – has created a critical security blind spot that organizations can no longer afford to ignore. It’s what 1Password defines as the Access-Trust Gap: the security risks posed by unfederated identities, unmanaged devices, applications, and AI-powered tools accessing company data without proper governance controls.
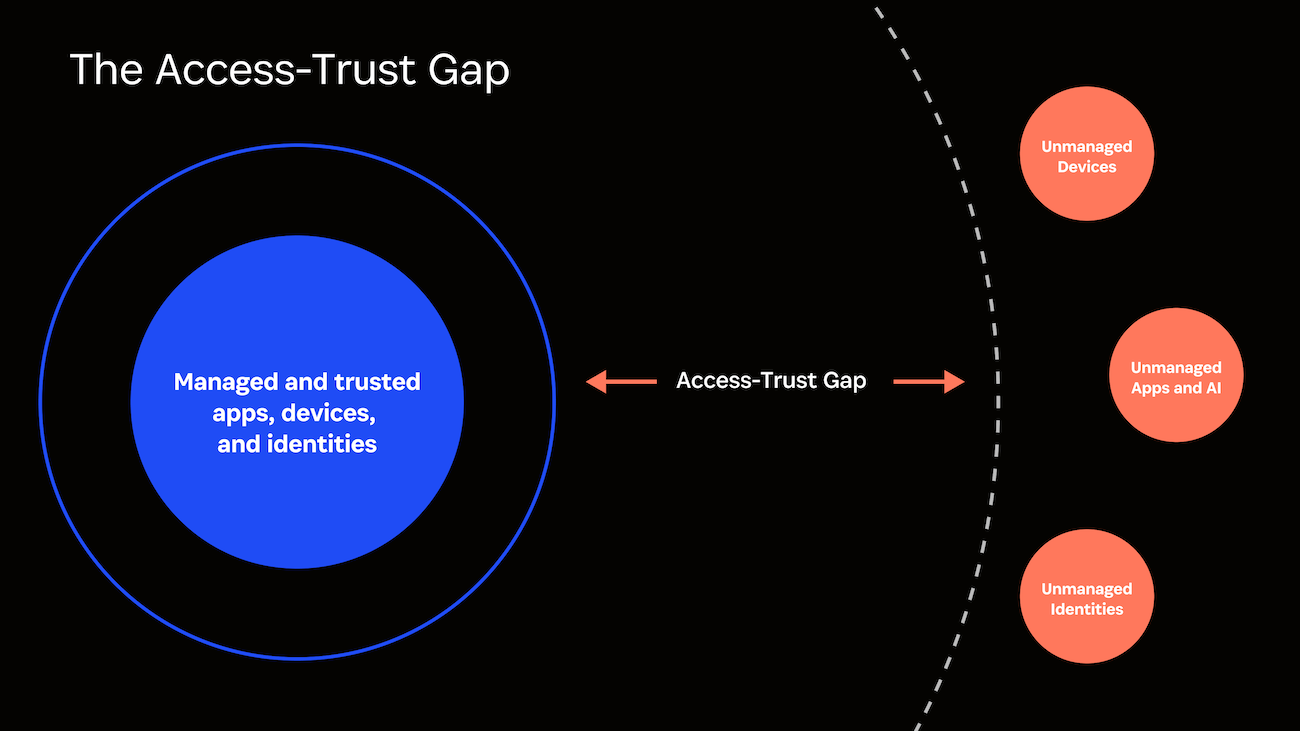
In 2024, 1Password launched Extended Access Management (XAM), a new security category designed to close the Access-Trust Gap. Our platform, 1Password® Extended Access Management, helps organizations secure every sign-in, to every app, from every device.
Omdia’s report highlights five security goals that XAM aims to address, to help organizations respond to today’s and tomorrow’s security risks.
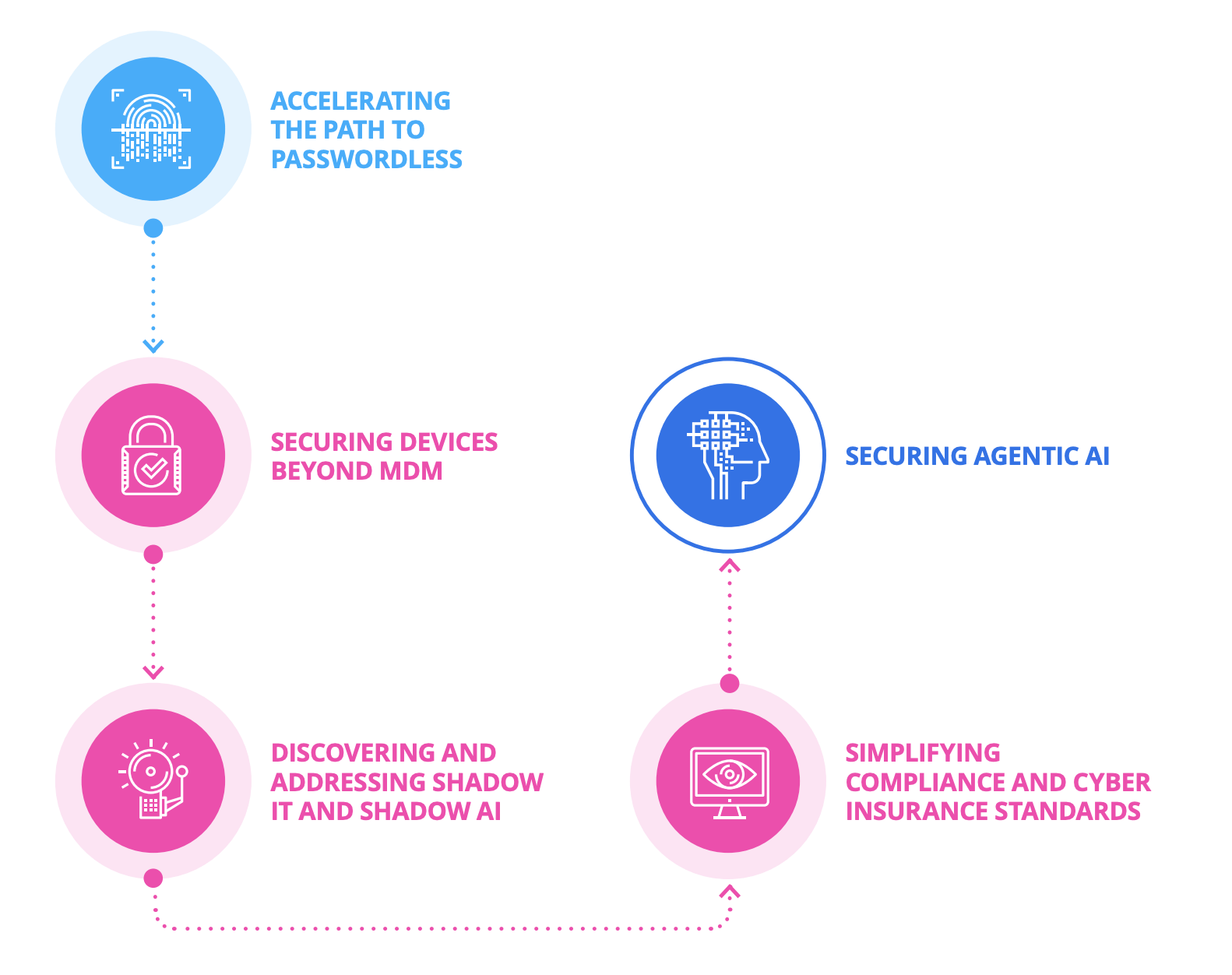
This blog post is the first in a series that will explore each of these strategies in greater detail, starting with Strategy 1: Accelerate the path to passwordless.
Why passwordless is a priority
As Omdia’s report points out, “A truly passwordless environment has long been the dream of security leaders.” It’s not hard to understand why this is such a major priority; passwords are a weak and risky form of authentication. Verizon’s 2025 Data Breach Investigations Report found that credentials remain the number one way hackers gain access to systems, even after years of trying to secure them.
Passwordless authentication reduces risks like phishing, brute-force attacks, and credential stuffing by ensuring users never have to interact directly with passwords. Credentials such as passkeys are device-specific, encrypted, and resistant to being stolen or reused in cyberattacks.
Yet Omdia also notes that “fully eliminating passwords is a years-long undertaking, and authentication must be as secure as possible at every step along the way.” That’s an important point because it highlights the fact that “passwordless” isn’t a binary; it’s a process.
Organizations must prioritize passwordless authentication for their most sensitive resources, but technical and budgetary considerations may make it impossible to achieve fully passwordless authentication overnight. Instead, the path to passwordless involves adopting the most secure authentication that is feasible and available for each resource. In some cases, this may mean hanging onto passwords but ensuring they are strong, unique, and secure.
Every organization’s journey to passwordless authentication will be different, but the first step on this path is visibility.
“Eliminating password risk requires taking a methodical approach to discovering passwords everywhere they are used – even in previously unknown shadow IT apps – and replacing them with stronger credentials and passwordless authentication.”
How 1Password Extended Access Management accelerates the journey to passwordless
Omdia’s report outlines several of the ways 1Password Extended Access Management can help organizations achieve their passwordless goals:
- Giving administrators visibility and risk oversight into what applications are in use, what devices they’re accessed from, and by whom – therefore ensuring appropriate authentication security is in place
- Identifying every compromised or weak credential and every sign-in that does not use available multi-factor authentication or passkeys
- Enforcing security policies to ensure employees replace every at-risk sign-in with a stronger credential before accessing the application
- Evaluating application risks across the company and identifying high-use unmanaged apps that are likely to hold sensitive data so they can prioritize SSO integration or migrate users to managed apps
For a closer look at how our platform can help you start or accelerate your journey to passwordless, check out our video:

 by Elaine Atwell on
by Elaine Atwell on