
A number of iOS apps, including 1Password, have a security problem in how they handle OAuth tokens. 1Password 3.6.5, which was submitted to Apple several days ago, fixes this. This will be a free update for all owners of 1Password for iPhone, 1Password for iPad, and 1Password Pro (for iPhone and iPad). We can’t predict how long Apple’s approval process will take, but the update should be available soon, if it isn’t already by the time you read this.
Because of this bug, someone who gains physical access to your device may be able to copy authentication tokens off of it, then install those tokens on their own device to access your Dropbox data. It is not entirely clear at the moment under what circumstances an attacker will also need the device passcode. It appears that if the device has previously been synced with the computer the passcode isn’t required. In any case it is important to protect your iPhone, iPad, or iPod Touch protected with a good passcode.
We have been extremely careful in how we store your Dropbox username and password for automatic syncing, but like many others, we didn’t take the appropriate precautions when it came to OAuth tokens. These tokens allow quick connection to Dropbox (Facebook and other services also use OAuth). Of course, any 1Password data that an attacker fetches from your Dropbox account is still encrypted by 1Password.
In 1Password 3.6.5, which we submitted to Apple at the beginning of the week, we store OAuth tokens securely in the iOS keychain, where they are properly encrypted and cannot be copied to other devices. However, if other apps that use Dropbox have the same problem (and it looks pretty common), then OAuth tokens can be copied from those apps as well.
The OAuth problem

The problem of how OAuth tokens are stored was first discussed Tuesday (April 3) by Gareth Wright reporting on the Facebook iOS app. Since then, it became clear that the Dropbox app itself has the same problem. Presumably there are many other apps that connect to services like Facebook or Dropbox that are unfortunately in the same boat.
Dropbox have told The Next Web that:
[Our] Android app is not impacted because it stores access tokens in a protected location. We are currently updating our iOS app to do the same.
Facebook’s initial statements have been less clear, but no doubt they will be submitting a fix soon.
For one of the best discussions of this whole thing, please see the report and analysis by The Next Web.
What this means for you and your 1Password data
This design problem, both in versions of 1Password prior to 3.6.5 and in other apps, means that it is easier for an attacker to get hold of and manipulate your 1Password data stored on Dropbox than we had anticipated. I used to say that it was far more likely that someone could get hold of your 1Password data by stealing your Desktop computer than by getting it off of Dropbox. I certainly have to revise that assessment.
The good news is that your usernames and passwords (along with notes and attachments) are well encrypted. Even if someone gains full control of your Dropbox account they will not be able to get at the secrets encrypted in your 1Password data. We have also been busily working on an updated version of our data format that is even better suited for life in the cloud.
You can also manage which devices are allowed to connect to Dropbox. That is, you can instruct Dropbox to reject certain OAuth tokens and also view the the last few times each authorized device has connected.
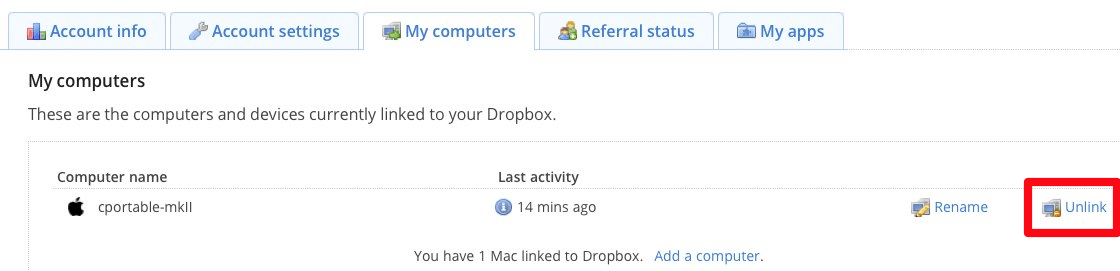
To manage your Dropbox devices, log in to your Dropbox account with a web browser, and under your account name, go to Settings and then “My Computers”. If you suspect that an OAuth token has been stolen, you can unlink the computer or device. After that you will need to relink the computer or device to your Dropbox account using your Dropbox username and password.
Alternatives to Dropbox
Every time there is a security issue with Dropbox, people rightfully suggest that we offer alternative syncing mechanisms. At this point, there is nothing that I’m in a position to say beyond what we’ve said earlier in “Dropbox Terms“. There are developments, but nothing I am even willing to hint at just yet.
More security changes to come in 3.6.5
The changes coming in 3.6.5 are all about security and bug fixes. Please see “1Password 3.6.5 for iOS is out with PBKDF2 goodness!” for details.
Appendix: When is a passcode required for this attack?
When an iOS device is connected to a computer that it hasn’t connected to previously, the user will be prompted to enter the passcode on the iOS device. After that first connection, the computer will store some keys that will allow it to unlock the iOS device for future connections.
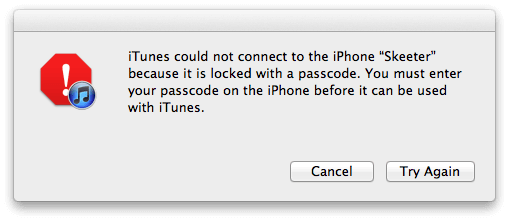
So once you have unlocked your iPhone for a particular computer, when you plug it in later, you do not need to unlock it for the file system on the device to bevisible to tools like iExporer. This is presumably why initial reports of this issue claimed that no device passcode was necessary to extract the files containing the OAuth tokens.
There is, unfortunately, one further complication. iTunes will automatically unlock the device for any user account on the same computer that the device has previously been unlocked on. That is, if Alice and Bob both have user accounts on the same Mac, and Alice has at one point entered the her passcode on her iPad to allow syncing, then Bob will be able to gain access to most of Alice’s iPad simply by using iTunes in his account on the Mac. What is worse is that Bob’s account on the computer can also be a guest account, and he will still have access.
All of the testing I have done has been with iTunes 10.6.1 on Mac OS X 10.7.3 (Lion). I have not tested this with iTunes on Microsoft operating systems.
What is worrisome here is that exactly the same people (co-workers, family members) who have the easiest access to your iOS devices are very likely to have some account on the same computer that you have used.
Still, passcodes do matter so please remember that a good device passcode is a good idea.
Data protection classes
As of 1Password 3.6.5 we put the OAuth information into the iOS keychain using the “ThisDeviceOnly” data protection class that will not allow the OAuth token to be copied from the device unencrypted. There is a bit of terminological muddle in that “ThisDeviceOnly” and “ProtectionComplete” mean the same thing except that the former is used with keychain items and the latter used with files. I prefer the term “non-migratable” to cover both.
The application property lists files, plists, contain app preference settings, and this plists do not have the non-migratable restriction on them; they are fully accessible once the device has been unlocked. Note that data with the non-migratable restriction cannot be restored from an iTunes or iCloud backup to a different device. So if you replace your iPhone or iPad, you will need to re-enter your Dropbox credentials to reestablish automatic syncing.
Please join the discussion of this on our forums.

 by Jeffrey Goldberg on
by Jeffrey Goldberg on
