Watchtower tells you when a site has been compromised without telling us which sites you have in your 1Password vault.

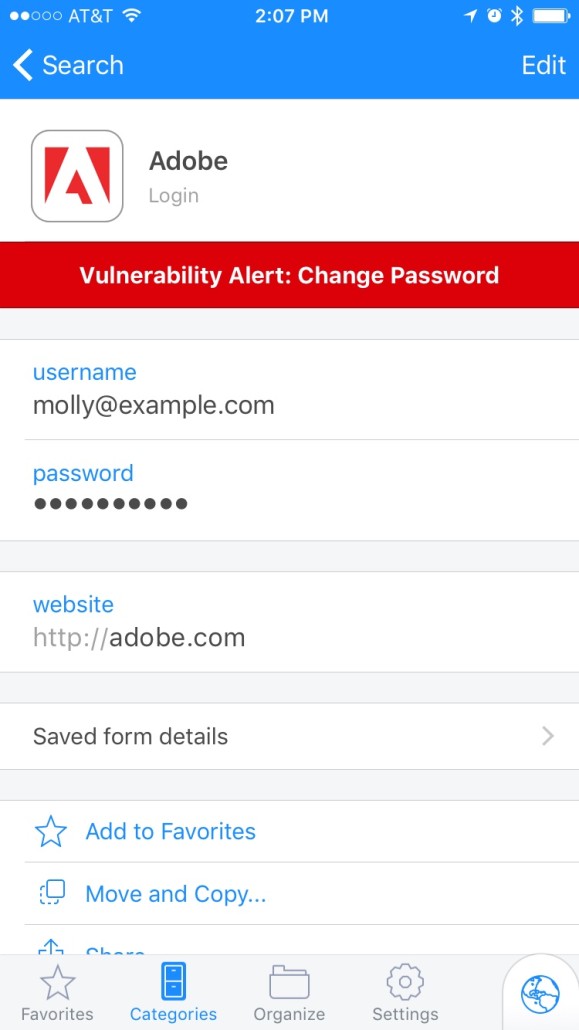
There are some great new features in the 1Password for iOS update that hit the App Store last week. One of them is that we’ve added Watchtower (a feature that has been available on Mac and Windows for some time now) to 1Password for iOS. Watchtower warns you if a site or service has been compromised in a way that would make it a good idea for you to change your password for that site. Watchtower in 1Password looks at the most recent time a password change was recommended for a site and it looks at the time that your password for an item was last modified. If, like Molly (one of my dogs), you haven’t updated your Adobe password since the 2014 breach, you might see something like this:
Preserving your privacy
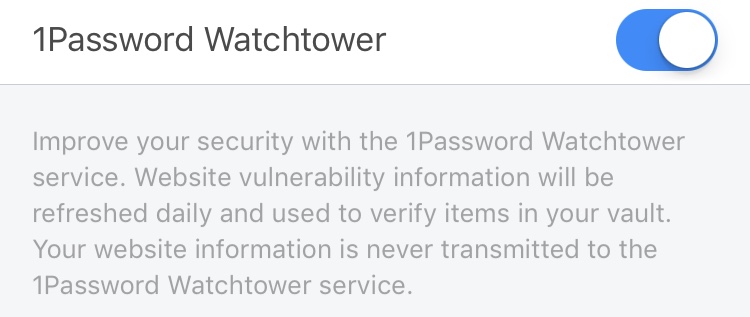
I want to talk about a far less visible feature of Watchtower: We’ve added Watchtower support in a way that still preserves your privacy. We don’t want to know what sites and services you have in your 1Password vaults, so when 1Password checks to see if one of your Logins is listed in Watchtower, it does not make a query to our servers asking about it.
Querying Watchtower without querying you
Our Watchtower people are continually watching reports of site breaches and updating our database of such sites regularly. This is how 1Password knows that a password change is recommended for some site. The “obvious” way for 1Password on your computer (and now iOS device) to alert you, would be to go through your 1Password items and ask our database on some server about the status of those items. The problem with this “obvious” way of doing things is that it means that any server your copy of 1Password queries would then be able to know your IP address and what sites you have in your 1Password data. If 1Password on some device were to ask our server, “Do you have Watchtower information about ISecretlyHateStarWars.org?” then our server will know that someone at your Internet address may have a very nasty secret. You certainly wouldn’t like us to know such things about you, and we don’t want to know such things either.
The road less travelled
So we don’t do things the obvious way. Instead, we send the same stripped down version of our Watchtower database to everyone who turns on the feature. You have a local copy of the Watchtower data on your device, and 1Password just checks against that copy of the local data. All we can know (if we chose to log such information) is which IP addresses have enabled Watchtower. We are never in a position to know what sites you have in your 1Password data.
Baked-in privacy
It may take a bit of extra work from us to design Watchtower in a way that preserves your privacy, but we think it is worth it. Your privacy must be protected by more than mere policy (a set of rules we make on how we behave with respect to data about you); instead, we aim to bake privacy protection into the very structure of what we build. We design 1Password in a way that would make it hard for us to violate your privacy. You can read more about this approach to privacy in our support article, Private by Design.

 by Jeffrey Goldberg on
by Jeffrey Goldberg on


Tweet about this post