For years, global regulations and compliance standards have been a primary driver of Mobile Device Management’s (MDM) adoption in the workplace. This is thanks to its ability to force managed devices, en-masse, into meeting basic levels of compliance.
However, MDMs have never been a complete solution for endpoint security or compliance. They’ve only fallen further behind in recent years, which have seen many regulatory standards evolve and require more robust protections for employee endpoints. As such, many security leaders have embraced alternative or complementary solutions to help meet their compliance obligations. Among the most prominent is a category of solutions called device trust.
Device trust solutions ensure that devices are both known and in a secure state before they can authenticate to company resources like SaaS apps. While MDM and device trust have significant differences – for example, MDM has no relationship to authentication – they both monitor and enforce device security. As such, they both have a role to play in compliance.
This article will compare the abilities of MDM and device trust to help meet the requirements of various regulatory standards.
Compliance for managed devices
MDM is necessary to enforce certain compliance requirements, and is widely regarded as a “table stakes” security tool for companies once they reach a certain size. Devices enrolled in MDM are commonly referred to as “managed,” which reflects the tendency of companies to consider a device functionally secure as long as it has MDM installed.
But MDM alone cannot ensure device compliance with the complex and varied landscape of global cybersecurity and data privacy regulations and standards.
MDM is a compliance necessity
MDMs can enforce certain baseline device policies, including:
- Requiring that a device be password-protected
- Requiring that screenlock be turned on
- App management, such as forcing app updates or allowlisting or blocklisting apps
- Requiring that firewall be enabled
- Pushing out OS updates
- Enforcing disk encryption
Many of these capabilities are helpful to meet compliance obligations. But perhaps the single most crucial capability for compliance purposes is MDM’s ability to remotely lock or wipe devices.
NIST’s guidelines for enterprise mobile device security strongly recommend that IT and security admins have the ability to remotely wipe employee devices, since this greatly reduces the risk of sensitive data being taken from stolen or lost devices, and is a major asset when securely offboarding employees. Remote wipe is also explicitly necessary to pass many compliance audits. Examples include:
- PCI DSS requires that compliant companies have various protections related to lost or stolen devices. This includes the requirement that, “If a device is presumed to be lost or stolen, the merchant should immediately disable and securely wipe the device remotely.”
- ISO 27001:2022 requires the installation of remote wipe capabilities.
- HIPAA requires the enablement of remote wipe.
- SOC 2 compliance requires that “Policies and procedures are in place to automatically or manually erase or otherwise destroy confidential information that has been identified for destruction.”
Even so, MDM alone is far from enough to achieve total compliance with any one of these standards.
Device trust helps achieve compliance on managed devices
Device trust solutions can achieve the same baseline device policies as MDM, but are also capable of much more granular policy enforcement. (For a closer look at those capabilities, check out the full ebook or the first blog in this series, on the technical limitations of MDM vs device trust.)
The capabilities of device trust make it particularly well-suited to supplement MDM in enforcing compliance on managed devices.
- PCI DSS requires that companies “Identify users and authenticate access to system components.” It also states that processes or mechanisms must be in place to guard against phishing attacks.
- ISO 27001:2022 requires that companies “Take proactive measures to prevent data from being leaked,” such as “…adequate authorisation techniques.” It also requires systems to delete downloaded data according to specified timeline retention policies.
- HIPAA requires oversight and mapping of data flows across devices, as well as adequate authentication protections.
- SOC 2 has confidentiality requirements dictating that companies “Have procedures to identify confidential information when it is created or received and “Ensure secure destruction of confidential data after retention periods expire.”
- GDPR and CPRA/CCPA require that companies take steps to ensure that employees do not process protected data “…except on instructions from the controller…”
Device trust solutions cannot remotely wipe and lock devices. What they do is make the device identity part of authentication. This means that users or bad actors cannot authenticate with phished credentials alone – they can only authenticate from devices that are previously trusted by an organization. As such, device trust solutions can help teams meet various requirements according to authentication and phishing protections. And depending on their individual capabilities, different solutions may have additional uses to put toward meeting compliance goals.
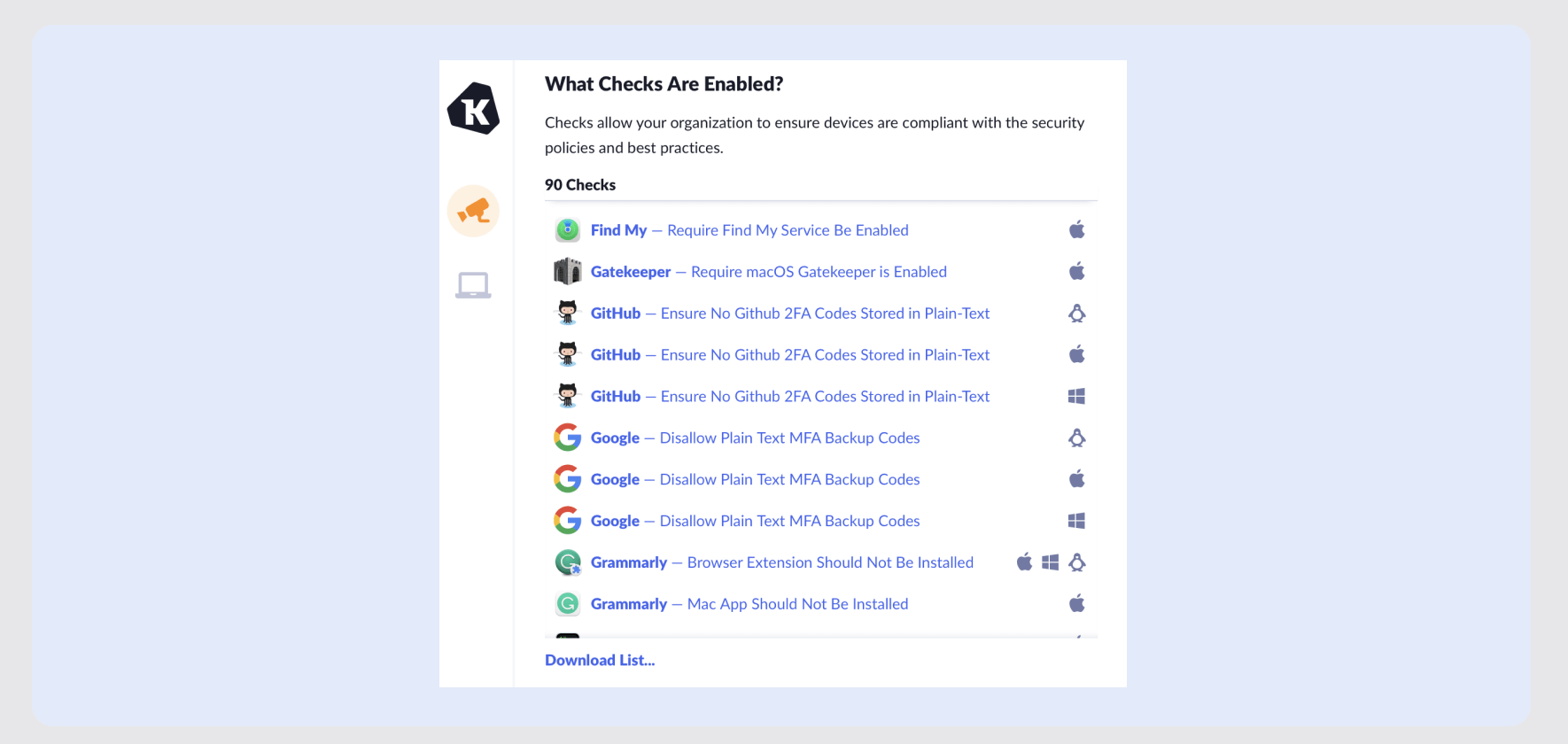
For instance, each of the previously listed compliance guidelines requires that any sensitive data is deleted once it’s been retained for a certain amount of time. 1Password Device Trust allows teams to run Checks that help monitor devices for files associated with sensitive data storage – for instance, those downloaded from locations like GitHub and Salesforce. These Checks can then ensure that these files are deleted from devices in a timely manner.
This is just one example. Through Checks, teams can also monitor and enforce various other security and device health properties that are beyond MDM’s scope. These can help meet the needs of further compliance with regulatory standards.
Compliance for unmanaged devices
Employees’ personal devices are often considered “out of scope” for compliance audits, but this is beginning to change. Many compliance standards have explicit requirements related to the security of bring-your-own-device (BYOD) policies.
For one example, PCI DSS mandates that if a personal device has access to corporate environments, it must have firewall enabled. Similarly, many compliance standards mandate that companies ensure a level of compliance for any contractor or partner devices that access their systems.
As such, teams need security solutions that can ensure a level of compliance on those unmanaged devices that are not enrolled in MDM.
MDM can’t secure BYOD
On company-owned devices, a company has a right (and even an obligation) to aggressively enforce compliance. But laws like GDPR and CCPA have strict requirements related to how personal data is processed, and that includes data belonging to employees. For example, a Spanish bank was fined 120,000 euros under GDPR after they accidentally remote-wiped a former employee’s personal data.
In many ways, MDM’s data wipe capabilities can be as much a compliance problem as a solution. NIST is quite clear that, “Wiping data not owned by the enterprise can cause legal issues.” Overall, remote-wipe leaves MDM unsuited for enforcing compliance on devices where employees’ personal data could be at undue risk.
For similar reasons, MDM is also not suited for managing contractor or partner devices. In fact, it may even be impossible – a device cannot be enrolled in more than one MDM at a time, and contractor and partner devices are likely to have another MDM installed.
Finally, MDMs that can cover Linux devices are few and far between, and will often only be able to manage certain Linux distributions. Even then, Linux MDMs often have limited controls over those devices – for instance, some cannot support remote wipe for Linux.
To meet their compliance obligations, teams need ways to ensure compliance on devices that fall outside the scope of their MDM solution.
Device trust helps get unmanaged devices compliant
Because most device trust solutions lack the ability to remotely lock or wipe devices, they can often offer a less invasive form of management that is suitable for securing personal, contractor, and Linux devices.
For instance, while MDM can prevent users from disabling their firewall, 1Password Device Trust can require that a device’s firewall is turned on in order to authenticate–the same outcome achieved with a lighter touch.
As popular as BYOD is, it won’t suit many organizations’ compliance needs. For instance, BYOD is not advised for healthcare settings, where it can add even deeper complications to the already complex task of complying with HIPAA guidelines. In cases like these, device trust enables teams to ban personal devices outright. Admins can refuse registration from devices that aren’t company-owned or enrolled in MDM, and block authentication from any device that isn’t registered to a user.
In addition, 1Password Device Trust is built on the principles of honest security. This is why we include a privacy dashboard for each employee that shows what data our agent collects, and its potential impact on user privacy. This can help companies prove their commitment to meeting GDPR and CCPA requirements related to transparency and data minimization.
Compliance requires flexible solutions
This article is a far from exhaustive overview of endpoint security compliance, but we’ve established that no single security solution can ensure device compliance with the complex and varied landscape of global regulations and standards.
To recap: on managed devices, device trust is a strong complement to MDM, helping to enforce more fine-tuned policies and block authentication on the basis of compliance. On unmanaged devices, device trust is a necessary substitute for MDM to ensure that sensitive data is only being accessed by compliant devices.
Cybersecurity compliance is complex. But it can be made simpler by finding solutions that are flexible enough to secure a wide variety of users and devices. With complementary solutions like MDM and device trust, IT and security teams can gain the oversight they need to meet their company’s compliance goals.
Want to learn even more about the relative abilities and limitations of MDM and device trust solutions? Read 1Password’s complete ebook, “Why MDM isn’t enough for device security.”
 by Rachel Sudbeck on
by Rachel Sudbeck on