Balancing security and productivity is hard. On one hand, IT and Security have an obligation to protect the company. On the other hand, employees are most productive when they can work with the tools they know and love.
Between hybrid work, BYOD, and shadow IT, one thing is clear: the way we work has changed; and the way we protect that work should too. Existing access management tools were built for a bygone age when every employee was on-premises; SSO was the way into every application used in the business and every device was managed by IT; and all access happened over corporate networks. But things have rapidly changed since the start of 2020, and these days:
- Hybrid and remote work have become standard.
- Employees frequently use unsanctioned applications that they bring in to boost their productivity.
- Employees and contractors increasingly use their personal devices for work purposes.
The tools we use today for identity and access management (IAM) are great at securing access to managed applications, but they’re unable to secure access to unsanctioned applications – and in reality do not even have visibility into those applications that live in the shadows beyond ITs ability to manage them. With the popularity of SaaS applications and the freedom that hybrid work arrangements provide, the number of unsanctioned applications businesses have has more than doubled over the last four years on average. Security teams have almost no way to prevent company confidential or customer sensitive data from flowing into unmanaged applications, or to ensure that departed employees don’t still have access to the data held in those applications that lack access management control.
Similarly, the mobile device management (MDM) tools offered today do a strong job securing company-managed devices, but employees or contractors rarely allow company MDM tools to be installed onto their personal laptops or mobile devices that they now frequently use for both business and personal purposes. Security teams have almost no way to stop wounded or compromised devices from logging in through their SSO provider into critical business applications.
We’re all living with the problems created by this disconnect between the tools we have and the reality of how we work – data breaches are more common and devastating than ever. Clearly, a new approach to secure access management is needed. And today, a new approach has arrived.
Introducing Extended Access Management (XAM)
Extended Access Management is a new category of security software that fills critical gaps in the identity and access management landscape. It is focused on extending the capabilities offered by IAM and MDM to the unmanaged applications and devices that today’s tools cannot secure. Extended Access Management secures access to all the places data goes, by giving companies the ability for the first time to manage:
- Unsanctioned and unmanaged apps and websites (shadow IT) that are not secured behind SSO.
- Unmanaged devices, that are either poorly managed by MDM or outside its scope altogether.
In companies today, too many sign-ins are untrusted – either because the sign-in is to an unsanctioned application or from an unhealthy device. This is what we call the Access Trust Gap, and it represents the percentage of sign-ins in a business that aren’t trusted – whether that’s due to unmanaged applications or from untrusted devices. The Access Trust Gap is increasing for most businesses because employees continue to bring in new SaaS applications and more frequently use personal equipment.

Every Business with IAM Needs Extended Access Management
Extended Access Management plugs the access management holes created as a result of IAM being unable to see or secure unmanaged applications. Every company of every size, from SMBs through the enterprise, needs to extend their access management strategy to cover all applications and devices. Today’s approach of securing only managed apps and devices is what has led to the rapid growth in the Access Trust Gap in most businesses.
Requirements of Extended Access Management
Extended Access Management goes beyond traditional IAM to support how we work today. For example, supporting a remote or hybrid workforce comes with fundamentally different challenges than simply plugging in your device to a corporate network.
| Requirement | Use-Case | Existing Workforce Identity Solutions | Extended Access Management (XAM) |
|---|---|---|---|
| User Identity | Manage the entire lifecycle of end-user identity - provision user access from onboarding to offboarding. | ✅ | ✅ |
| Universal Sign-on | Offer SSO to all managed and unmanaged applications, and websites, from a single pane of glass. | 🆇 SSO only for managed applications | ✅ |
| Device Trust | Monitor device health and security in real-time to mitigate security risks by addressing device compliance before access occurs. | 🆇 No ability to ensure device health | ✅ |
| Contextual Access Management | Dynamic policies that take context – such as time, location, device health, and credential health – into consideration before allowing access. | 🆇 No ability to block SSO access to applications from unhealthy or compromised devices | ✅ |
| Application Visibility | Generate an automatic inventory of managed and unmanaged apps across platforms to track usage, SSO eligibility, and more. | 🆇 No visibility of or capability to manage the inventory of unsanctioned applications used for business | ✅ |
| Enterprise Password Management | Securely manage access to sensitive information. | 🆇 No ability secure access to unmanaged applications | ✅ |
Introducing: 1PasswordⓇ Extended Access Management
Extended Access Management is a vendor-neutral concept, like Zero Trust or RBAC. We believe that Extended Access Management is a new category of security software that solves the access management challenges and closes the Access Trust Gap created by today’s hybrid way of work where BYO applications and devices are the new norm. 1Password Extended Access Management is the first product to be offered in this new category.
1Password Extended Access Management addresses security across your workforce, devices, applications, and credentials. As a result, access to every application from every device is secure.
1Password Extended Access Management goes beyond traditional identity and access management to secure all applications (including managed, shadow IT, and legacy apps) and access from all corporate and personal devices.
1Password Extended Access Management secures organizations on four fronts:
- User identity secures your workforce.
- Device trust secures your devices.
- App Insights secures all applications.
- Enterprise password management secures your credentials.
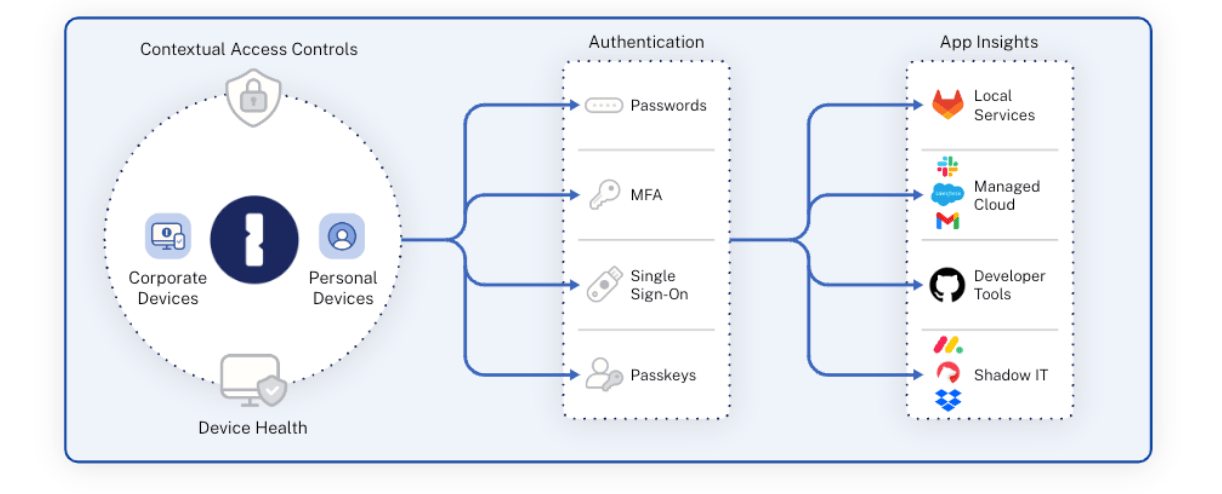
Taken together, 1Password Extended Access Management delivers the industry’s first solution that closes the Access Trust Gap that lies between identity and access management (IAM), privileged access management (PAM), mobile device management (MDM), and extended detection and response (XDR).
1Password Extended Access Management makes it possible for businesses to balance security and productivity. Universal Sign-on (USO) improves security while making it easier than ever for employees to access the tools they need to best do their jobs. And Device Trust makes it safer for companies to allow employees to use the equipment that maximizes their performance.
Here are a few links to learn more:
With that, let me be the first to welcome you to the era of Extended Access Management.

 by 1Password on
by 1Password on


Tweet about this post