Tl;dr: This blog discusses IDC’s 2024 study, “The Future of Access Management: Identity Security Requirements for a Modern Application Access Approach.” The study identifies the biggest challenges facing security leaders today, especially those exacerbated by hybrid work. Below are IDC’s findings as well as downloadable checklists that security practitioners can use to address the security gaps in their organizations.
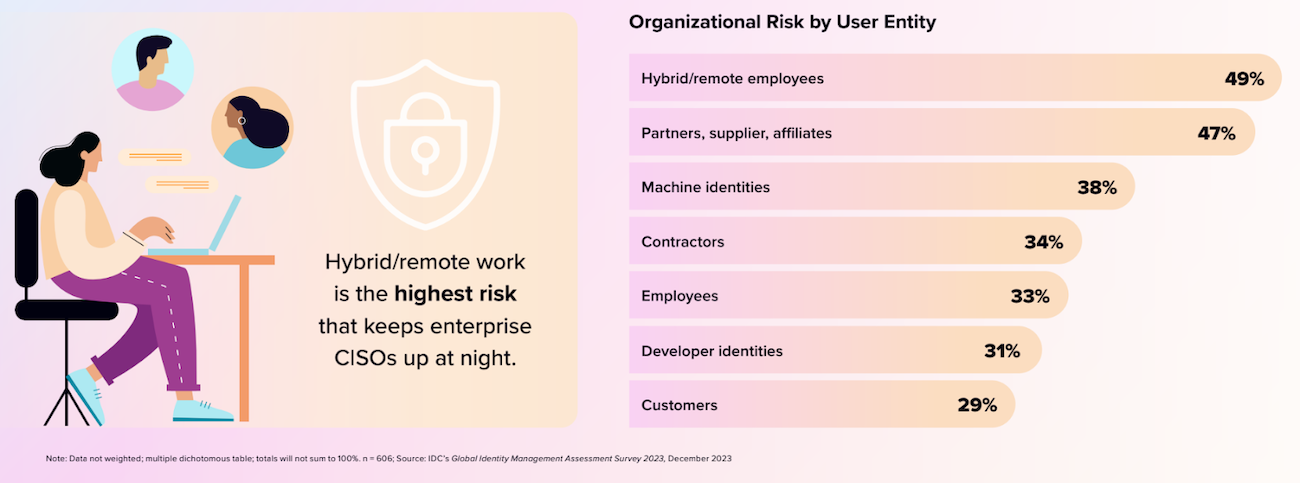
IDC ran a recent survey of over 600 international enterprises about the key issues they face in identity and access management (IAM), including a ranking of “organizational risk by user entity.” The top four riskiest groups they named were: hybrid/remote employees; partners, suppliers, and affiliates; machine identities; contractors.
There is a shared challenge across all four groups: they are underserved by traditional security tools, and their risk has been exacerbated by the rise in remote work.
In a nutshell, it’s more difficult to confidently ascertain a user’s (or device’s) identity and ensure that they are behaving safely when that person/device doesn’t fit neatly into an office building, corporate network, identity provider, or company-owned and managed fleet.
As avenues for remote access increase, any CISO (indeed, any security or IT professional) knows that there’s a problem. The study states:
“Access is critical to workplace productivity, but it often leads to overly permissive sign-ins from unregistered and untrusted devices and/or invisible sign-ins into undiscovered and unmanaged applications.”
Still, it’s only recently that this problem has gotten a name: the access-trust gap. What it means is that sensitive data is being accessed by more than just the users, applications, and devices that a business trusts to access it – because these untrusted forms of access aren’t protected by traditional security tools. This gap has proven difficult to solve for a myriad of reasons. For one, in trying to secure hybrid BYOD environments, CISOs face the eternal tension between security and productivity. Every entrypoint brings risk, but every additional point of friction translates to frustration and lost productivity.
Recently, IDC released a security study about the challenges facing CISOs. In its study, IDC provides practical guidance for CISOs on how they can close the access-trust gap without upsetting the delicate balance between security and productivity.
IDC’s study describes the nature of today’s security challenges and offers concrete solutions to them based on a zero trust access (ZTA) framework and the principle of least privilege. While the ideas in the study are universal and product-agnostic, in this blog post, we’ll use 1Password® Extended Access Management to illustrate these tactics in action.
Securing user identities and authentication
Stolen credentials have factored into almost one third of all breaches this decade. If teams want to reduce the risk of credential-based attacks, they need to secure sign-in processes. There are several ways to do that today, though you’ll most likely need to implement a combination of them instead of relying on just one.
Single sign-on (SSO)
SSO helps ensure that only trusted users are company resources by reducing the number of passwords and allowing for centralized access provisioning. Unfortunately, many vendors charge an exorbitant “SSO tax,” making this critical security feature prohibitively expensive to implement across all apps.
The study advises CISOs to “secure high-use/high-risk apps through SSO federation” but also to “extend security beyond traditional SSO … to a universal approach that enables sign-on across all legacy, SaaS, and web applications.”
Passwordless authentication
According to the IDC study “almost one-third of all ransomware attacks originate from a phishing email.” And the target of many such attacks is employee credentials, which attackers use to escalate their permissions.
Phishing attacks are a stubborn and serious threat, so teams should use phishing-resistant authentication factors. That means taking every opportunity to ditch passwords, SMS, and other insecure methods. Instead, roll out passwordless factors like passkeys.
Enterprise password manager (EPM)
Of course, it’s no easy task to completely do away with passwords, especially when working with legacy applications. That’s why an enterprise password manager is, frankly, table-stakes security.
Admittedly, we’re biased since we make an industry-leading EPM solution. But, we’ll note that CISA agrees with us on this point.
Securing devices and applications
IDC’s study stresses the importance of getting visibility and control over untrusted devices and apps.
“A future-looking access management solution should extend the strengths of identity access management (IAM) and mobile device management (MDM) to unmanaged apps and devices, ensuring all access attempts are trusted and secure."
This requires a device trust solution that can offer more granular security than MDM and work on devices not eligible for MDM enrollment (such as BYOD, Linux, and contractor devices). It also requires the ability to identify the presence of shadow IT applications so that they can be eliminated or brought under management.
Device trust authentication
Device trust ensures that users can’t authenticate to company resources unless they’re logging in from a device that is already known, trusted, and associated with their identity.
Device posture checks
Device trust ensures that each device is in a secure state before it authenticates. That means continuously checking that devices are compliant with all of your security policies, such as having an updated OS and browser, firewall turned on, EDR present, etc.
Manage applications
According to The State of Security Enterprise Report, 1Password, 2024, more than one third of the apps employees use aren’t sanctioned by their workplace.
It’s likely that CISOs and IT admins alike are already familiar with the threat of shadow IT, which has only been growing with the increasing sprawl of remote access. For instance, The IDC study also shows that 59% of companies added more than 20 SaaS apps in the last 18 months.
Getting a handle on shadow IT requires centralized visibility over the entire access process from identities, devices, and applications. Anything that touches company data needs proper oversight so that IT can see a full inventory of their ecosystem and provision access accordingly. From there, IT can block unsafe apps, properly manage approved ones and even eliminate unused licenses and redundant applications, potentially saving tens of thousands of dollars.
Enable employee productivity
Every CISO has to find the right balance between security and productivity. IDC’s advice for managing this dilemma focuses on avoiding forced restarts and allowing for end user remediation.
End user remediation
The IDC study advises that teams “offer users the ability to self-remediate for faster action and lower IT burden.”
For example, when a device fails a posture check, 1Password’s Device Trust solution alerts the user of the problem and gives them detailed instructions on how to fix it. It also gives them a deadline, and if they don’t remediate the issue before the time is up, they’ll be blocked from authenticating. This grace period lets users solve their own issues with minimal disruption to workflows.
It’s also worth mentioning that with end user remediation, IT teams can expect to see fewer IT tickets due to blocked users.
Security meets productivity
Notably, IDC’s study illustrates that Extended Access Management is fundamentally about enabling users to work in the way that’s easiest and most productive for them.
IDC avoids advising rigid tactics like banning mobile devices, prohibiting SaaS app downloads, or just going back to the office. Rather, the firm encourages flexible solutions to secure a more flexible workplace.
CISOs don’t want to impede the employee experience, and they don’t have to. With thoughtful solutions, they can keep systems secure and enable employees to succeed as we all transition to a new workplace paradigm.

 by Rachel Sudbeck on
by Rachel Sudbeck on