In baseball, it’s tempting to think that once you’re on a base, the hard part is over.
But then, just when you think you’re safe (you are literally “safe”) the baseman hits you with the hidden ball trick. Your opponent appears to throw the ball away, but merely hides it and tags you in the moment you’re most vulnerable.
A similar thing is happening to companies with multi-factor authentication (MFA). The goal of MFA, much like baseball, is to safely get users where they need to go (in this case, authenticated into their apps). For years, MFA has been considered the gold standard of enterprise cybersecurity. However, even when you’re doing everything right, you can be lured into a false sense of security that your opponent is happy to take advantage of.

Take Retool, for example. They experienced a data breach in August 2023 because a threat actor bypassed not one but three(!) forms of security – VPN, SSO, and Google Authenticator.
By deploying phishing, vishing, and Man-In-The-Middle (MITM) tactics, the bad actors were able to convince an employee to give them a One-Time Password (OTP). And that’s all they needed; by compromising the MFA factor, they were able to gain access to the Retool employee’s Okta account and access all of the MFA codes on Retool’s Google Authenticator.
In a blog post about the breach, Retool named Google’s authenticator as one of the primary culprits for the breach. They wrote: “Google recently released the Google Authenticator synchronization feature that syncs MFA codes to the cloud. As Hacker News noted, this is highly insecure, since if your Google account is compromised, so now are your MFA codes.” Furthermore, they explained that this feature was turned on by default, without Retool’s knowledge.
This cyberattack shows what can happen when an organization relies too heavily on phishable authentication factors — like passwords and SMS OTPs – in their MFA. Because we can go ahead and preview one of the main themes of this blog: all MFA factors are not created equal.
Even President Obama knew that back in 2016, when he was urging Americans to move past passwords. Yet organizations are still struggling with MFA, and bad actors are thriving because of it.
MFA’s promise was to secure all our logins while providing a relatively frictionless experience to users. But while any MFA is certainly better than nothing, the user experience is about as frictionless as sandpaper, and attackers keep finding new ways to poke holes in it. So let’s talk about what happened to MFA, and how we can help it fulfill its original promise.
MFA’s promise
Before we start analyzing where MFA is falling short, let’s briefly make clear what we’re talking about. As a refresher, MFA is an approach to authentication that relies on multiple factors to prove a user’s identity. Here’s a nonexhaustive list of factors that can be leveraged, courtesy of OWASP:
Something You Know: Passwords, PINs, Security Questions
Something You Have: OTP Tokens, Certificates, Smart Cards, Email, SMS and Phone Calls
Something You Are: Fingerprints, Facial Recognition, Iris Scans
There are also less traditional forms of MFA, which are usually used in addition to factors above, and sometimes when assessing particularly sensitive or unusual logins.
Somewhere You Are: Source IP Address, Geolocation, Geofencing
Something You Do: Behavioral Profiling, Keystroke & Mouse Dynamics
You might notice that passwords are included as a potential “something you know” factor, despite being notoriously insecure–especially if your company (like too many others) doesn’t use a password manager.
Indeed, MFA was supposed to solve many of the problems created by shoddy password practices. When it comes to password-related attacks Microsoft stated in 2019 that MFA would have stopped 99.9% of account compromises. Still, passwords stubbornly remain part of the mix, and that’s particularly dangerous when you pair them with another phishable factor, like an OTP.
MFA risk #1: social engineering
What’s the easiest way to steal a user’s authentication factors? Just ask them nicely. In social engineering MFA attacks, a threat actor tricks an employee into handing over an MFA factor — login credentials, OTPs, MFA codes – by acting as a trusted source.
That’s how Rockstar Games was compromised in September 2022. A bad actor masqueraded as an IT employee at Rockstar and was able to capture credentials from an unsuspecting employee. They were then able to use the compromised account to breach Rockstar’s Slack channel to leak videos of unreleased gameplay.
“Attackers will often use the information they’ve already compromised as part of the social engineering attack to lull users into a false sense of security,” Jordan LaRose, Practice Director for infrastructure security at NCC Group, tells DarkReading. And that information can be trivially easy to find.
This was the case in 2023’s MGM hack, when threat actors called MGM’s help desk, impersonated an employee, were likely provided a password or MFA reset, and gained access to the account of a super administrator with advanced privileges. Allegedly operating on the “honor system," the MGM help desk only required very basic information that can be scraped from social media and sources that only require a quick Google.
Bad actors fooling tech support (and sometimes pretending to be tech support) is emerging as one of the more tried-and-true methods specifically designed to thwart MFA. And that’s why any factor that can be phished should be considered inherently vulnerable.
MFA risk #2: session hijacking
Even when you take away the human element from MFA’s list of weaknesses, you’re still left with things like vulnerable browsers.
Cookies have long been the way the internet has saved our browsing information and preferences; however, they also risk allowing threat actors to steal your credentials after login.
This attack method famously happened in August 2022, when ransomware gang Yanluowang compromised the personal Google account of a Cisco employee who unfortunately synced their Cisco credentials to their browser. This enabled the threat actors to deploy a MFA fatigue attack–which we’ll cover in greater detail later—allowing them to have MFA codes and login credentials in hand before eventually getting access to Cisco’s servers.
Malicious browser extensions provide another variant of this attack. If installed, they can also allow bad actors to take control of a user’s session once past any MFA prompts without any interference from the user.
Companies like Google are trying their hardest to make cookie theft and session hijacking a thing of the past. They’ve recently introduced Device Bound Session Credentials, where Chromium browsers will abandon browser cookies, forcing bad actors to act locally on devices, thus lessening the attack surface.
MFA risk #3: man-in-the-middle (MITM) attacks
In MITM attacks, hackers create a fake network/server/webpage that intercepts user credentials when a user thinks they’re entering them into the legitimate destination.
“This allows the attackers to bypass most available methods of MFA, since the user is providing the site, and the hacker, with both the username and password and additional authentication,” says Drew Trumbull, incident response team lead with the Information Security Office at the University of North Carolina.
In the past, for a MITM attack to be successful, a previous server or network needed to be compromised to gain initial access for the bad actor to then install a keylogger or present a fake login page. Yet that’s no longer the case with the advancement in phishing kits. While these kits have been available for some years, a 2022 report by Proofpoint unveiled just how much they had evolved.
Bad actors have abandoned recreating target websites in lieu of instituting a transparent reverse proxy (or attacker server) method; this actually presents the real websites victims intend to visit. This not only allows the bad actors to capture credentials entered during the login attempt, but the session cookie. This gives them unfettered access to the user’s systems while capturing any credentials or MFA prompts.
And now, to everyone’s dismay, these phishing kits have evolved again.
The expansion of MFA phishing kits
In March 2024, Sekoia published a report highlighting a new variant of MITM attacks (or Adversary-In-The-Middle, as they are increasingly called) with their discovery of a phishing-as-a-service (PhaaS) platform named “Tycoon 2FA.”
With prices starting at $120 for a 10-day subscription, there’s plenty of opportunity for threat actors to make a hearty return on investment when their initial purchase costs less than a nice dinner.
By building upon previously established methods, like the reverse proxy method, threat actors were able to target Microsoft 365 and Gmail accounts and bypass two-factor authentication (2FA) protection. Here’s a visual, courtesy of Sekoia.
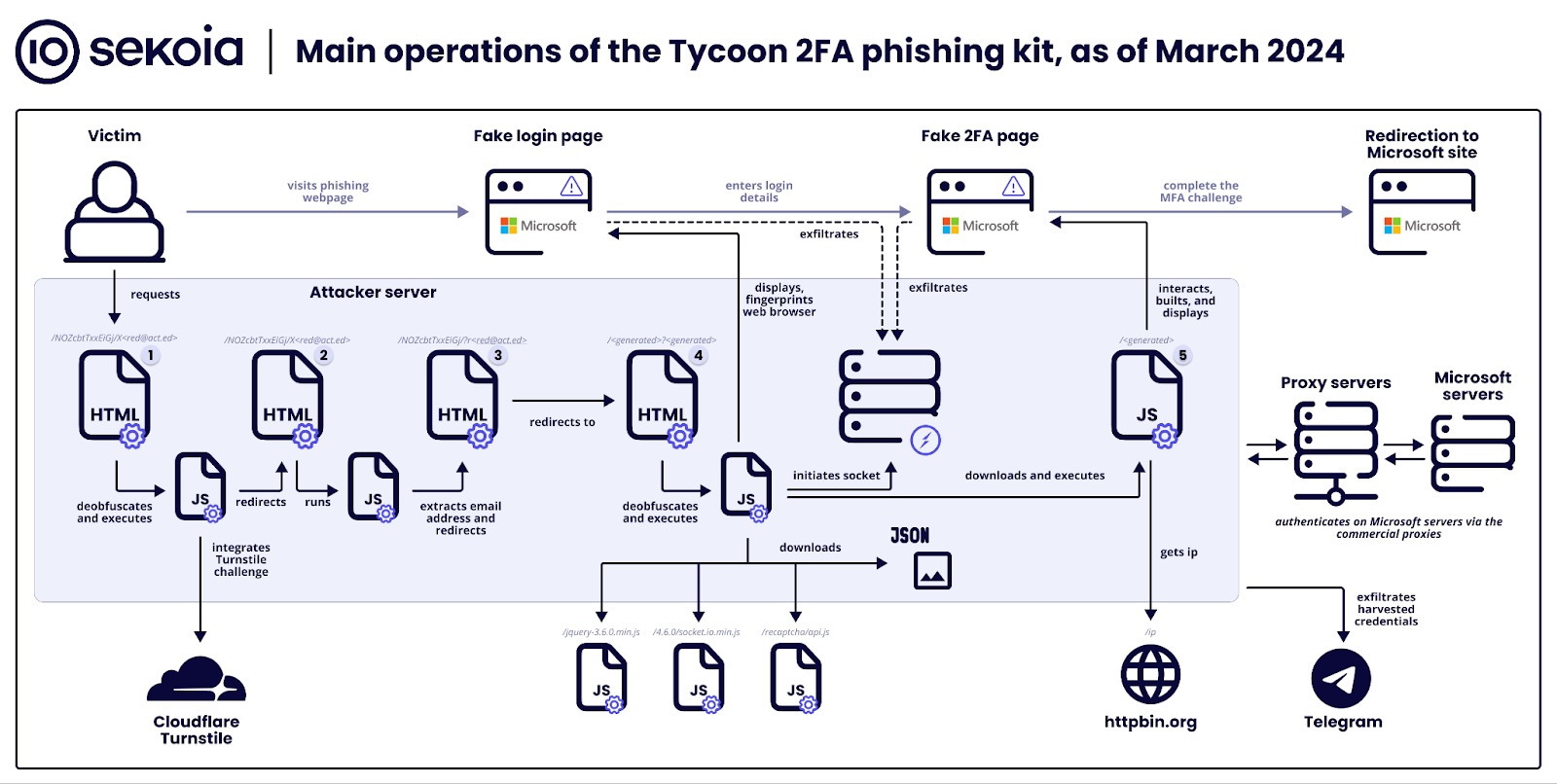
If you find that diagram a bit overwhelming, I don’t blame you. For some help, BleepingComputer gave a simplified description of the phishing kit, which we’ll now quote at length:
Stage 0: Attackers distribute malicious links via emails with embedded URLs or QR codes, tricking victims into accessing phishing pages.
Stage 1: A security challenge (Cloudflare Turnstile) filters out bots, allowing only human interactions to proceed to the deceptive phishing site.
Stage 2: Background scripts extract the victim’s email from the URL to customize the phishing attack.
Stage 3: Users are quietly redirected to another part of the phishing site, moving them closer to the fake login page.
Stage 4: This stage presents a fake Microsoft login page to steal credentials, using WebSockets for data exfiltration.
Stage 5: The kit mimics a 2FA challenge, intercepting the 2FA token or response to bypass security measures.
Stage 6: Finally, victims are directed to a legitimate-looking page, obscuring the phishing attack’s success.
For those keeping count at home, this phishing kit involves session hijacking, plain ‘ol phishing, and MITM tactics. But the really scary part of Tycoon 2FA is how good it is at covering its tracks.
As Sekoia points out,
“…it appears that the phishing kit developer extended the kit’s capabilities to identify and evade more traffic patterns associated with analysis or scan environments. This includes IP addresses hosted in datacenters or associated with the Tor network, as well as specific User-Agent strings of bots and some versions of Linux web browsers.”
MFA risk #4: SIM swapping
Compared to other methods we’ve gone over, SIM swapping attacks require a bit more effort to succeed. Bad actors select a target and conduct an extensive social engineering campaign to collect as much information as they can on their victim, most importantly their phone number.
They then contact the target’s phone carrier and impersonate them to receive a new SIM card. This allows the attacker to insert the SIM card into the mobile device of their choosing and effectively take over the target’s number.
We’ve seen the tactic pay off when it was done to a Microsoft employee in March 2022 in the infamous Lapsus$ attack. Once the bad actor performed the SIM swap, they were able to access any MFA codes coming through SMS texts to the employee and escalated their access throughout Microsoft’s systems.
There’s only so much an end user, or MFA for that matter, can do to prevent a SIM swapping attack. The sage wisdom here is to abandon SMS OTPs in favor of stronger authentication methods. And that still may not be enough because if your mobile account credentials are leaked — we’re looking at you, AT&T — threat actors can now deploy eSIM attacks where little to no social engineering is involved.
As we’re learning, for MFA attack methods to be successful, they increasingly need to be done together.
MFA risk #5: MFA fatigue/bombing/flooding
Whatever you call these attacks – MFA fatigue, MFA bombing, or MFA flooding – they all fittingly convey a sense of despair.
And that’s the feeling you’d experience when your device is hammered with push notifications about password resets that you never triggered. Attackers usually spam you with an onslaught of MFA requests in the middle of the night, when your brain is foggy and you’re most likely to hit “approve” by mistake.

The goal of an MFA bombing attack is to coerce the victim into confirming their identity via notification, which is almost always the second factor.
And that’s key when discussing MFA’s viability. Our first line of defense, most likely a password, has failed, so we have a second factor to save the day. That is if the victim is prepared and trained to handle an onslaught of authentication requests; if not, down goes our second line of defense.
Now, MFA fatigue attacks aren’t new. They’ve been in the news for some years, none more so than the September 2022 Uber hack, which was a textbook MFA fatigue attack.
However, the Uber employee didn’t accept MFA push notification out of annoyance or lack of training; they accepted it because a cybercriminal posed as IT support and convinced them they needed to accept.
No password, no problem
In March 2024, KrebsonSecurity reported on MFA fatigue attacks specifically targeting executives that are Apple users. There’s nothing novel on the surface, but when you look into the details, it’s far more troublesome than previous attacks of this nature. That’s because it’s being pulled off without compromised credentials — just the victim’s phone number.
When a bad actor obtains an Apple user’s phone number, they’re able to continually bombard password reset notifications to the iPhone of the user, no matter if the device or iCloud account is new. If that doesn’t trick the user, then the bad actor has the ability to spoof a call from Apple’s legitimate support phone number.
And if you thought advanced security features like Apple’s recovery key would help, it does little to mitigate the password reset prompts.
KrebsonSecurity posits that bad actors are taking advantage of Apple’s flawed “forgot password” flow. Just like SIM swapping, this is tough to protect against, since our phone numbers aren’t exactly closely-guarded secrets. Until a fix of some sort — perhaps a rate limit — is implemented by Apple, MFA and the “deny” button will have to brace for impact.
The future of MFA
If you’ve read this far, you can agree that MFA has taken quite a beating. And like a prize fighter on the comeback trail, a change in defense is much needed to prevent getting knocked out again. But let’s run back the tape so we can find what to improve on—namely what we pick as second factors.
According to Oort’s “2023 State of Identity Security” report, “the average company has 40.26% of accounts with either no MFA or weak MFA. In contrast, phishing-resistant second factors account for only 1.82% of all logins.” And there you have it, folks.
Less secure methods, almost by default, reign supreme for our most sensitive accounts. But if we want MFA that actually holds off attackers, this is a trend that cannot continue.
If not passwords, then what?
If you take one thing away from this blog, let it be this: we need to get rid of passwords. The security industry has been saying it for years, but it’s been a slow drip for that mindset to turn into action. Luckily, we have the resources now with FIDO2.
FIDO2 (Fast IDentity Online 2 – ignore the tortured acronym) is an open standard for user authentication that strengthens security and protects users by using phishing-resistant and passwordless cryptographic credentials to validate user identities.
Developed by the FIDO Alliance, FIDO2 can be accomplished by two types of FIDO authenticators: roaming authenticators and platform authenticators. Roaming authenticators are portable hardware devices like Yubikeys that are plugged into devices cross-platform. And platform authenticators are embedded into users’ devices that generally require biometrics like Apple’s Touch ID or Face ID.
However, these are traditionally the second factor in a passwordless MFA experience. The first is passkeys. Passkeys in their simplest form are FIDO2 sign-in credentials that generate a pair of private and public passkeys that provide passwordless authentication. That means a bunch of random numbers that aren’t phishable!
Aside from being phish-proof, 1Password describes some of passkeys' benefits:
You don’t have to remember or type out your passkeys.
Your private key is never shared with the website you want to sign into.
Your public key can’t be used to figure out your private key.
Passkeys offer an improved user experience over other forms of authentication.
Passkeys can also be bound to a single device or synced across multiple devices, whatever the user prefers.
Still, it’s one thing for a solution to be available, and a totally different thing for that solution to be leveraged — even when leaders in the space are pleading for organizations to take advantage of it.
“To business leaders: I urge every CEO to ensure that FIDO authentication is on their organization’s MFA implementation roadmap. FIDO is the gold standard. Go for the gold,” said Jen Easterly, Director, CISA in a 2022 bulletin.
Look, passkeys aren’t perfect; they’re still developing, being adopted, and fighting against corporate interests, but there’s hope that won’t be the case for too long. And at the very least, while you make the transition, your company needs to be using an enterprise password manager to ensure that your team is using strong passwords. And tools like 1Password’s Watchtower can even monitor the dark web for stolen credentials, and help you know when passwords have been leaked and need to be updated.
Don’t forget about devices
While we’ve focused on the user identity portion of MFA, an unpatched or compromised device can do just as much damage as a weak password.
1Password Extended Access Management uses device trust. The presence of a device trust tool works as a possession factor; basically, if a device doesn’t have 1Password Extended Access Management installed, it can’t log in. So compromised credentials won’t work, and employees can’t be tricked into giving this factor away to a bad actor. But beyond that, 1Password Extended Access Management looks for compliance issues before letting a user log in, like an out-of-date browser. Making sure devices are in a secure state before they authenticate goes a long way to keeping out bad actors trying to piggyback into your systems.
How to improve your MFA strategy today
Let’s be realistic: the average company doesn’t have the budget or the technological ability to implement truly bulletproof MFA in 2024. You’re not going to buy everyone in your organization Yubikeys, and you can’t force all your vendors to roll out passkey support, much as you’d like to.
But you can still strengthen your MFA strategy today, using tools you already have. In particular, the most underused asset in security: humans.
User education
End users are often referred to as the weakest link in security. But let’s explore an incident where users limited potential damage from a MFA attack.
In January 2023, Reddit experienced a MITM attack when an employee clicked on a malicious link in an email. This phishing incident could have been devastating to Reddit. However, their end user’s security training tingled their spidey senses.
As Reddit CTO Chris Slowe explained, “[s]oon after being phished, the affected employee self-reported, and the Security team responded quickly, removing the infiltrator’s access and commencing an internal investigation.” There’s something to be said for that quick response.
Humans aren’t infallible, but they are capable of righting wrongs. If your organization doesn’t already, invest in making your security awareness program better. Creating a security program that actively engages employees will pay dividends if they’re ever faced with a threat.
Password manager
We’ve already explained that compromised (phished, breached, weak, or reused) passwords are at the root of many MFA attacks. So, at this point, an organization without a password manager is like a car without airbags.
Password managers can secure credentials today, while helping transition to a passwordless future, as most of them support passkeys. And since password managers are relatively inexpensive (especially compared to hardware tokens) you can roll them out to your entire workforce, not just highly-privileged admins.
Device trust
As Megan Barker succinctly explains, “[t]here’s no password manager or other mainstream tool with the ability to guard your secrets on a fully compromised device.”
It’s true. Password managers (even 1Password’s amazing one) can’t do everything. You’ll need help from a different set of tools to protect against unknown and unsecured devices.
As we mentioned earlier, that’s possible with device trust solutions. By making device posture checks part of authentication, you’re able to establish a security baseline for user devices and have an unphishable factor right there on the device itself.
And since 1Password Extended Access Management comes packaged with both Kolide Device Trust and the 1Password Enterprise Password Manager, you’re already monitoring security health at two points of authentication – the password, and the device.
The less you know, the better
MFA is some of the best security we have, but to fulfill its promise of protecting us from bad actors, MFA and passwordless methods of authentication need to become synonymous. Not only will they keep us more secure, they’ll save us from the exhaustion of today’s authentication.
Anything an organization does to phase out passwords is a great first step. Although you’ll need to educate and convince your higher ups on the effort and cost, as well as educating your employees how to use these new methods, it’s worth it.
Because I don’t know about you, but I think the world will be a better place if you don’t need to feel guilty when authenticating a fast food rewards account. That’s the world I want to live in.
Want to learn more about how 1Password Extended Access Management keeps systems safe? Request a demo.

 by Kenny Najarro on
by Kenny Najarro on