Here we provide an overview of the ISO 27001 audit process, so companies can embark on it with a clear idea of what it entails, and how they stand to benefit.
If you’re trying to prove that your organization is serious about security, ISO 27001 is the gold standard, the Black Card, the bumper sticker bragging that you’ve run a full marathon.
ISO 27001 certification has such an elite reputation because it’s so difficult to attain–it sets exacting standards that must be rigorously documented and continually maintained.
Despite the challenges, there are real benefits to achieving ISO 27001 compliance. In a moment where data breaches are rampant, cyber attacks are on the rise, and data privacy laws are being passed around the world, adhering to a strict security standard is your best liability insurance.
Here, we’ll provide an overview of the audit process, so you can embark on it with a clear idea of what it entails and how you stand to benefit.
What is ISO/IEC 27001:2013?
ISO/IEC 27001 is an international standard for data security established by the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC). It provides guidance for creating an information security management system (ISMS) encompassing people, processes, and technology.
It’s the lynchpin of the ISO/IEC 27000 family of standards, which lay out internationally accepted best practices for data security. (The other ISO 27000 standards go into greater detail about specific aspects of information security, but ISO 27001 is the only one for which you can receive certification.)
ISO 27001 specifies how an ISMS should function to satisfy the “C-I-A triad” of information security:
Confidentiality (Restricting data access to authorized users)
Integrity (Data is complete and free from inaccuracies or corruption)
Availability (Users can access the information they need)
The ISO 27001 framework is divided into two sections. The first, “Clauses,” explains the background and theories of data security, such as defining what to consider in a risk assessment.
Meanwhile, Annex A of the standard lays out the recommended controls for ensuring data security. There are 14 sections of the Annex, each of which concerns a different domain, ranging from cryptography to asset management to business continuity management. Within each section are multiple controls touching on various security concerns.
For example, Annex A.7 deals with human resource security and includes controls that start with pre-hire screening and end with secure offboarding.

Who is ISO 27001 certification for?
The principles and best practices of the ISO 27001 standard apply to any organization that wants to formalize its information security and data protection processes.
But while any organization that handles sensitive data should consider getting compliant with ISO 27001, getting certified is a different matter, and a relatively small number of companies choose to go through the process.
According to ISO’s most recent 2022 survey, there are roughly 71,550 currently valid ISO 27001 certifications. That’s obviously not a huge number, but it’s still a significant increase from 2016 when there were 45,500. (It’s also worth noting that these numbers are just best guesses since the survey is voluntary, and there’s no central directory of certified organizations.)
The organizations that have the most to benefit from getting ISO 27001 certified are the ones that deal in highly sensitive information assets. These include information technology companies (e.g., managed services providers,) financial institutions, healthcare providers, telecom companies (e.g., internet services providers,) and government contractors.
The benefits of ISO 27001 certification/compliance
ISO 27001’s elite reputation and global usage mean that certification can confer a competitive advantage. And even compliance without certification offers security benefits.
Guard against data breaches
Complying with the ISO 27001 standard will strengthen your security posture. By identifying and remediating risks, and defining the people and processes responsible for managing risks, you can reduce both your vulnerability to security incidents, and the potential fallout should one occur. This, in turn, offers a meaningful (albeit invisible) ROI, since you’ll avoid the high costs of data recovery, remedial actions, loss of business, and regulatory fines.
Stay compliant with data privacy laws
ISO 27001’s status as a global standard means it has heavily informed multiple international data privacy laws. GDPR refers organizations to it as a set of recognized best practices, and Australia’s Digital Security Policy was deliberately crafted to adhere to 27001.
Broadly speaking, while ISO 27001 certification doesn’t guarantee perfect compliance with every data security regulation, it does represent a big step in the right direction for data privacy compliance goals.
Close more deals
ISO 27001 certification shows partners and customers that your company takes information security seriously. This can put you ahead of the competition, particularly among international customers, enterprise clients, and organizations with strict security requirements.
Improve risk management
The ISO 27001 standard requires organizations to establish accountability for information risk. With the proliferation of information assets, a transparent chain of command helps you clarify roles and processes and maintain appropriate access control. That way, nothing falls through the cracks.
Reduce frequent audits
As data breaches and attacks become more common, more organizations are auditing their vendors' ISMSs to ensure that their supply chain is protected. An ISO 27001 certification can help reduce the number and costs of these audits, both for existing customers and any during the sales cycle.
Key steps in the ISO 2001 certification process
ISO 27001 certification is a multi-step process, requiring a great deal of work before an auditor even gets involved. Here’s a (non-exhaustive) list of what it entails.
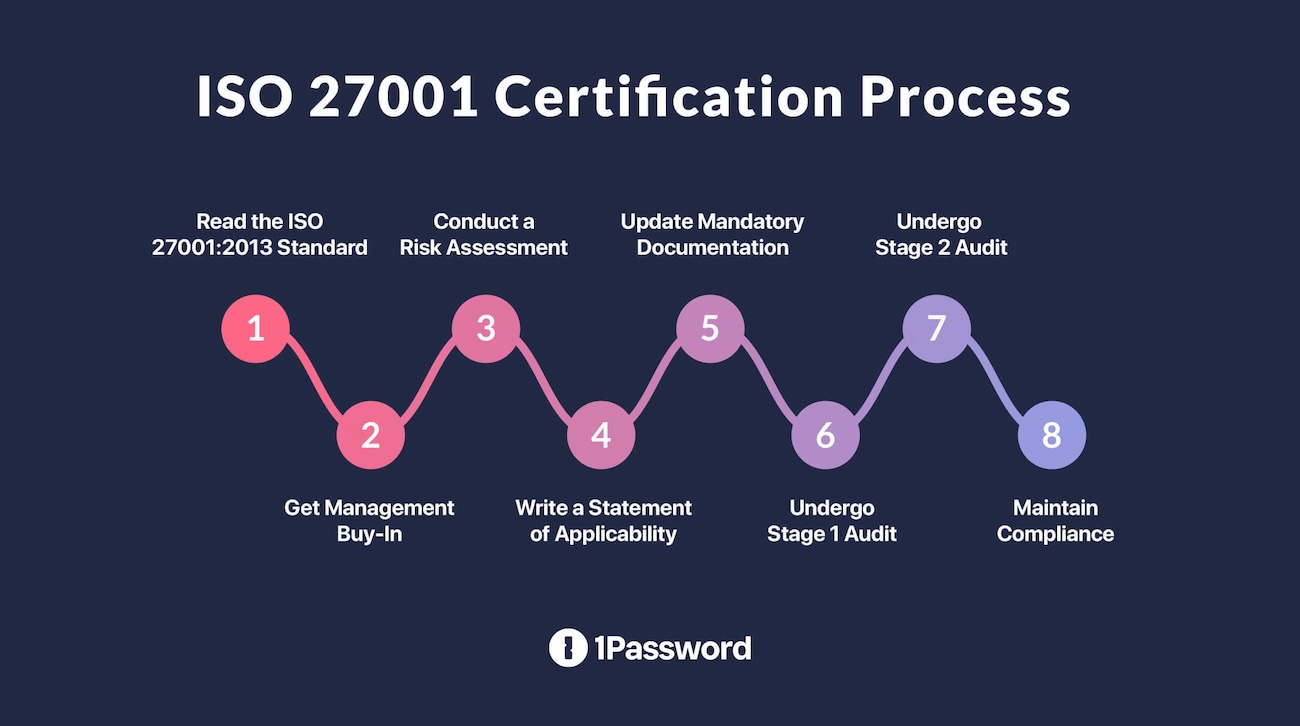
1. Read the ISO 27001:2013 standard
Step one is simply to read the complete ISO 27001:2013 text, which requires purchasing a copy. (At present, it costs roughly $150.) This will help you get a general sense of how labor intensive the certification process will be, based on which requirements you already fulfill.
2. Get management buy-in
ISO 27001 emphasizes the role of leadership in establishing and maintaining an ISMS. Clause 5.1 specifically “identifies specific aspects of the management system where top management are expected to demonstrate both leadership and commitment.”
Auditors will interview leadership and look for evidence of their involvement, so if you don’t have enthusiastic buy-in from the C-Suite, you should hit the brakes before you go any further.
To secure leadership support, you’ll need to build a business case for certification, and the projected ROI can help determine the project’s scope and budget. Organizations typically enlist the help of a third-party consultant, automated compliance products such as Vanta or SecureFrame, or a combination of the two. Those are costs you can budget for at the beginning of the process.
3. Conduct a risk assessment
The first official document you’ll need to produce is a risk assessment. There are various methodologies for determining risk, but the most common is an asset-based approach.
Here, you’ll list all your organization’s information assets – physical devices, intellectual property, software, etc – and assign a risk level to each based on the C-I-A framework we mentioned earlier. Since no two organizations are exactly alike, your approach to risk will vary depending on the specific data assets you maintain, but prioritize anything that could threaten your regulatory or contractual obligations or is business critical.
Next, you’ll assess how likely each threat is, and what the fallout from it would be. For instance, a sinkhole opening directly under your server room would have a massive impact, but is relatively unlikely. By contrast, the impact of someone stealing a developer’s unencrypted laptop could be almost as disastrous, and could happen much more easily.
Once you’ve identified your risks, ISO 27001 lets you choose from four options of risk treatment:
Eliminate: Delete the data in question or stop the risky activity entirely.
Share: This can mean either outsourcing risk to a third party or purchasing insurance to minimize the financial impact of a security event.
Control: Put policies or technology in place to manage the risk. In the developer’s laptop example, this would mean ensuring that all company devices meet your security requirements.
Accept: Choosing to accept a risk means that you believe that it’s so unlikely or its impact would be so small that it doesn’t justify the cost of remediating it.
The next (sub)step is to write a risk treatment plan, which will include:
A description of the risks.
The treatment option for managing each risk.
Who is accountable for the risk itself.
Who is accountable for the risk mitigation activity.
When you plan to complete the mitigation activity.
4. Write a statement of applicability
Once you’ve established which information security risks you plan to treat vs. accept, it’s time to craft your Statement of Applicability. This document outlines how you’ll apply controls to address your identified risks. (If all this documentation seems a little redundant, welcome to the world of ISO standards.)
In the Statement of Applicability, you’ll list which controls apply to your organization, the implementation status of each one, and an explanation for any controls you chose to exclude. You may reject a control that doesn’t apply to you (for instance, a fully remote company can disregard the section on delivery or loading areas) or because the cost of implementation outweighs the risk.
(If you’d like to see an example, Secureframe has a free Statement of Applicability template.)
5. Update mandatory documentation
Documentation is the bedrock of ISO 27001, and you’ll need to provide detailed descriptions of every facet of your ISMS. ISMS documentation describes how an organization meets the standard’s requirements, including the risk mitigation activities identified earlier.
As ISMS.online points out, the ISMS needs to obey the same principles of Confidentiality, Integrity, and Availability as the security policies it describes. Therefore, “it needs to be available when required and adequately protected from loss of confidentiality, unauthorized use or potential integrity compromise.”
6. Undergo stage 1 audit
There are two phases to an ISO 27001 audit. In Stage 1, an external auditor or certification body will conduct a “tabletop” audit focused on your documentation.
At this stage, you can still be in the process of implementing risk mitigation strategies as long as you can show that you do have plans in place. However, according to Varonis, “Lack of key documentation, weak support from management, or poorly identified metrics can all bring an ISO 27001 audit to a screeching halt.”
Assuming there are no giant red flags, auditors will identify any issues they expect you to resolve before the next stage.
7. Undergo stage 2 audit
Stage 2 of the audit is much more intensive. Whereas in the first stage, auditors review the documentation of your processes, in this stage, they review the processes themselves.
Auditors will test your controls and look for proof that when an incident occurs, it triggers the appropriate response from the people responsible.
To pass the certification stage, it’s absolutely essential that employees are aware of the ISMS and their role in it. You can’t create an ISMS “for” the auditors; if it’s not an internally functional document with real stakeholder buy-in, you won’t pass this stage. And since the Stage 1 and Stage 2 audits are usually only a month or two apart, you can’t plan to conduct this training during the gap.
In Stage 2, auditors will note any remaining nonconformities. Major nonconformities can prevent certification entirely, while minor issues can be flagged for further evaluation.
Assuming your ISMS works as promised, Stage 2 concludes with the auditor recommending you for certification.
But that doesn’t mean you’re done.
8. Maintain compliance
It takes a lot of work to achieve ISO 27001 certification and a lot of work to keep it. While you won’t need to get recertified for three years, you will have to continually maintain your ISMS and Annex A controls to pass your recertification audit.
During this time, you’ll also need to stay up to date on:
Mandatory internal and external audits (more on those in the FAQ section).
Regular employee security training.
ISMS policy updates.
Changes to the risk assessment.
ISO 27001 certification FAQs
As we’ve said, no two ISO 27001 experiences are exactly alike. However, you can make some rough estimates about the cost and timeline of the certification process based on where your organization is starting from.
How much does ISO 27001 certification cost?
The cost of the entire process from preparation to certification will depend on your organization’s current security posture, number of employees, and the resources you choose to devote to it.
According to ISO/IEC recommendations, the audit itself should cost between $5,400 (for an organization with under 50 employees) and $27,000 (up to 2,000 employees).
On top of that, you’ll need to account for the costs associated with providing employee training, creating documentation, hiring external assistance, updating technologies, and of course, the certification audit.
How long does the ISO 17001 certification process take?
The certification process can take anywhere from three months to a full year. Factors influencing this include:
Whether you have a documented ISMS or are building one from scratch.
The scope of your audit (a single business unit will be less time-consuming than your entire organization).
Whether you have a dedicated compliance professional, hire outside consultants, or assign a team member to take on compliance in addition to other duties.
The number of risks requiring remediation, and the difficulty of the remediation efforts.
How long is the ISO 27001 certification valid for?
An ISO 27001 certification is valid for three years, but you are required to undergo both internal and external audits during this time. A third-party auditor will conduct “surveillance audits” at six or 12 month intervals, usually focusing on areas of your ISMS that were of particular concern or significance in your original audit. In addition, Annex A.5 requires a review of your information security policies on at least an annual basis.
Take the easiest path to ISO 27001 compliance
“It’s supposed to be hard. If it wasn’t hard, everyone would do it.” Tom Hanks was talking about baseball in that quote, but it also applies to ISO 27001 certification. The difficulty is part of the point.
As a company that recently achieved ISO 27001 certification ourselves, we understand exactly how difficult it can be. But we also learned that, even though meeting this standard is a challenge, there are ways to make it less daunting. Your biggest ally is automation. The fewer manual processes you have, the lower the risk of human error, and the easier it is to maintain documentation.
Most compliance software has some automated security features built in, and you can also integrate standalone solutions, including 1Password’s. Many of our customers use 1Password® Extended Access Management as part of their approach to compliance because it provides real-time, cross-platform (even Linux), data on employee devices while respecting privacy. (ICYMI, those qualities map directly to the C-I-A framework.)
At the end of the day, the most important thing isn’t that you use 1Password Extended Access Management,or even that you go through an ISO 27001 audit at all. There’s enormous value in pursuing compliance with this standard, whether or not you ever pursue certification. Because while certification isn’t for everybody, information security absolutely is.
Reach out for a demo of 1Password Extended Access Management and see how we can help you achieve and maintain ISO 27001 compliance.
 by Elaine Atwell on
by Elaine Atwell on


