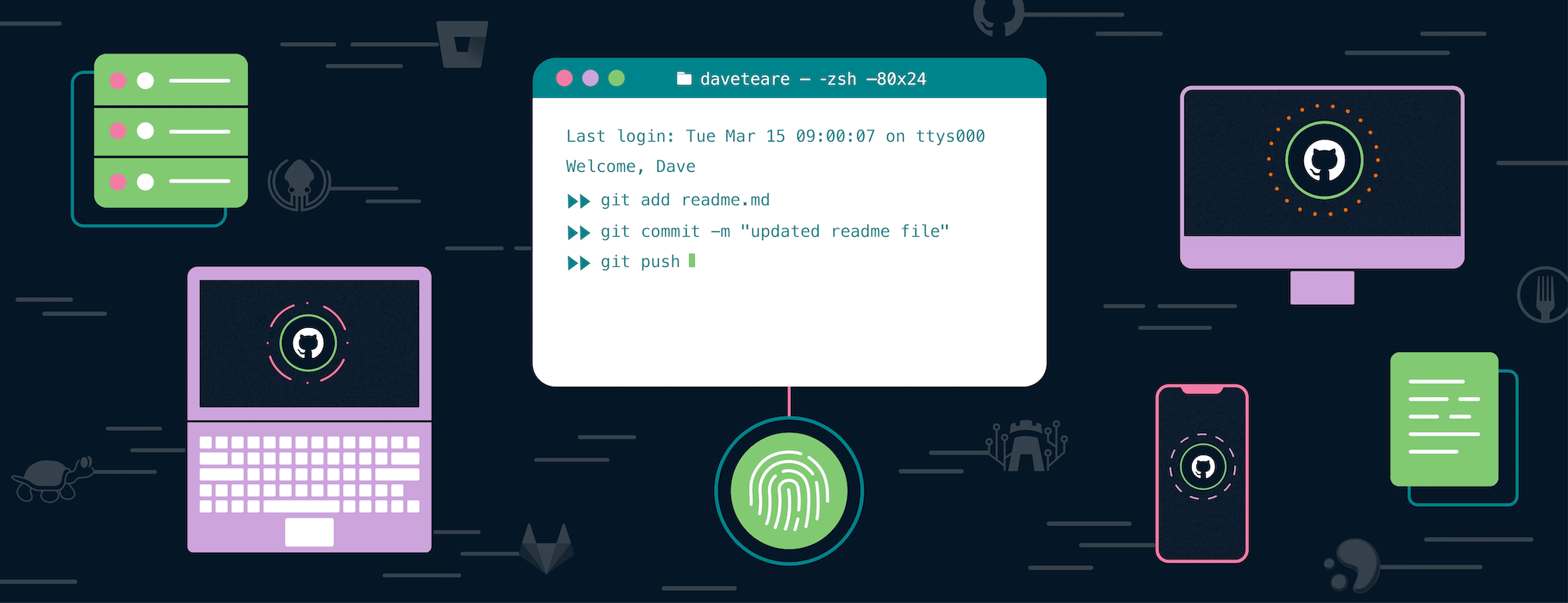
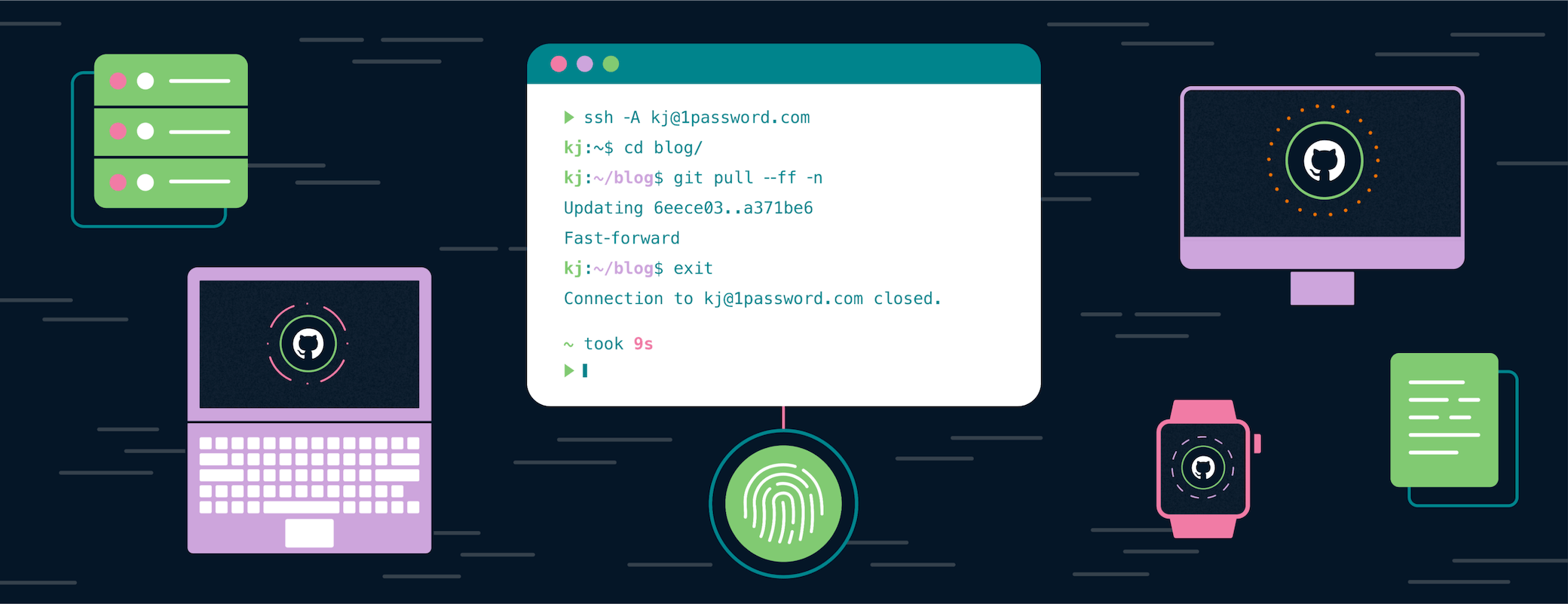
So 1Password CEO Jeff Shiner just committed code to one of my GitHub repositories. That’s strange. While he’s a developer at heart, I don’t think he gets much time to code these days. What’s going on here?
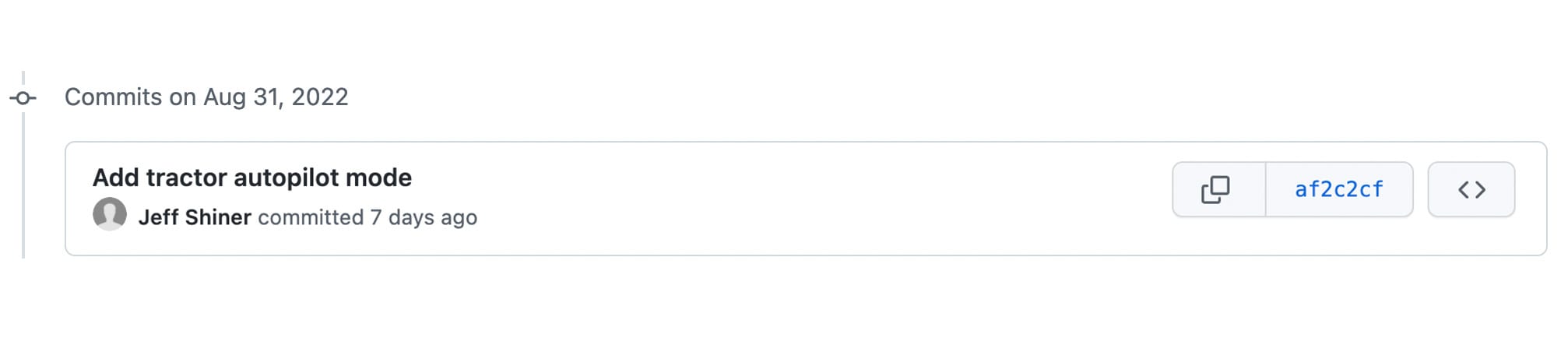
As you might have guessed, this didn’t actually come from Jeff Shiner. In fact, anyone can spoof a Git committer or author name with just a few terminal commands and pretend to be someone else:
$ git config user.email "jeff.shiner@1password.com"
$ git commit -m “Add tractor autopilot mode.”
This can make for a fun prank but is also a security liability. If you don’t know who is pushing code to your repositories, how will you know if your codebase is being hijacked by someone pretending to be a coworker?
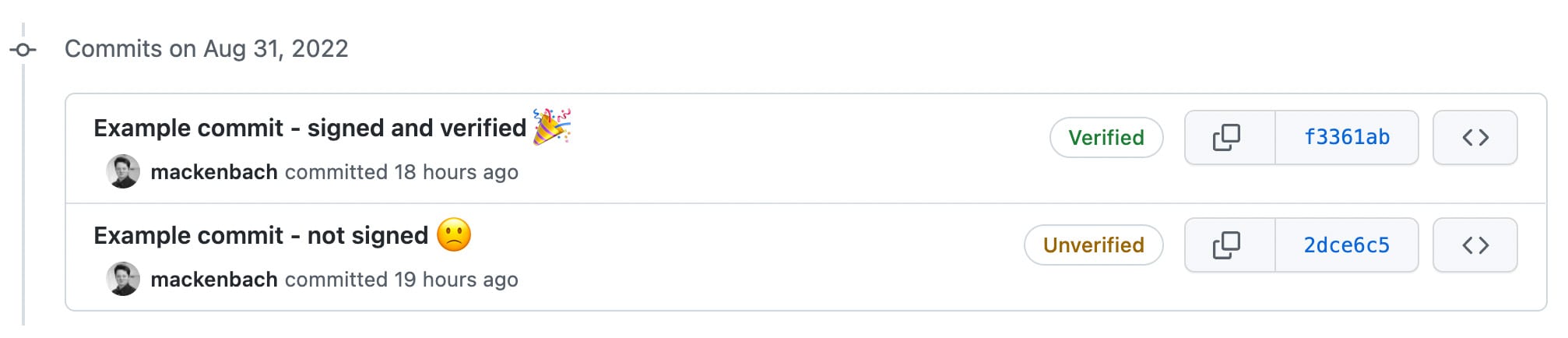
The answer is, you won’t know who is actually committing code unless your team signs their commits. This means using a cryptographic key pair to add a digital signature to each commit that verifies your identity. Once you sign, GitHub adds a handy “verified” badge to each commit. Goodbye fake Jeff.
Before now, signing was mostly done by generating GPG keys and associating them with your Git username and email. But if you’ve ever set this up, you probably remember the dull pain of trying to figure it out. That time could be much better spent actually building something… like an autonomous tractor.
Well, fret no longer because verifying commits just got WAY easier. We’re excited to announce that 1Password now allows you to set up and use SSH keys to sign Git commits. And with GitHub supporting SSH key signing as well, you can get that verified badge next to your username in seconds. No GPG keys required.
Check out this 60-second demo to see it in action:
This should help more teams adopt signature verification into their workflows.
Dealing with GPG can be troublesome at best. While secure when used properly, GPG is an archaic technology that relies on a web of trust for decentralized verification. But this functionality is often not used by developers and therefore adds unnecessary complexity without much security benefit.
On the other hand, loads of developers already use SSH keys to push code to GitHub. Now they can use SSH keys to sign their code as well.
And the best part? 1Password makes creating new keys a breeze whether you’re using 1Password on your desktop, or creating and filling new keys directly into GitHub with 1Password in your browser. It just works.
If you’ve previously used GPG keys to sign your Git Commits, the mechanics of using SSH keys will be the same (you can keep using the -S flag for commits and the -s flag for tags). However, setting things up is different. Here’s a quick preview of the process:
- Start by updating to Git 2.34.0 or later.
- Navigate to https://github.com/settings/keys
- Select “New SSH Key”
- Select “Signing Key”
- Navigate to the “Key” box and select the 1Password logo
- Select “Create SSH Key”, fill in a title and then select “Create and Fill”
- Select “Add SSH Key” and you’re all set!
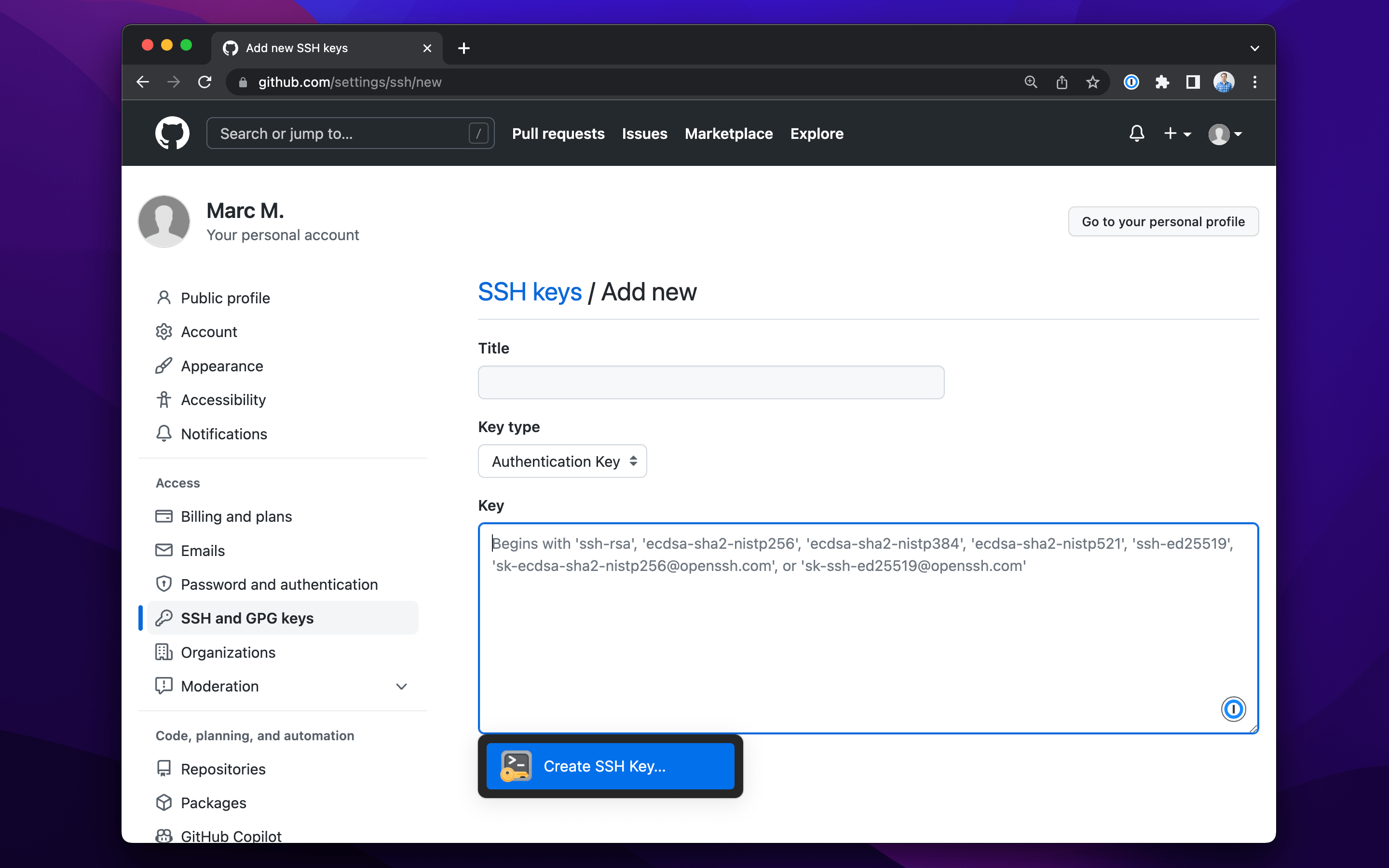
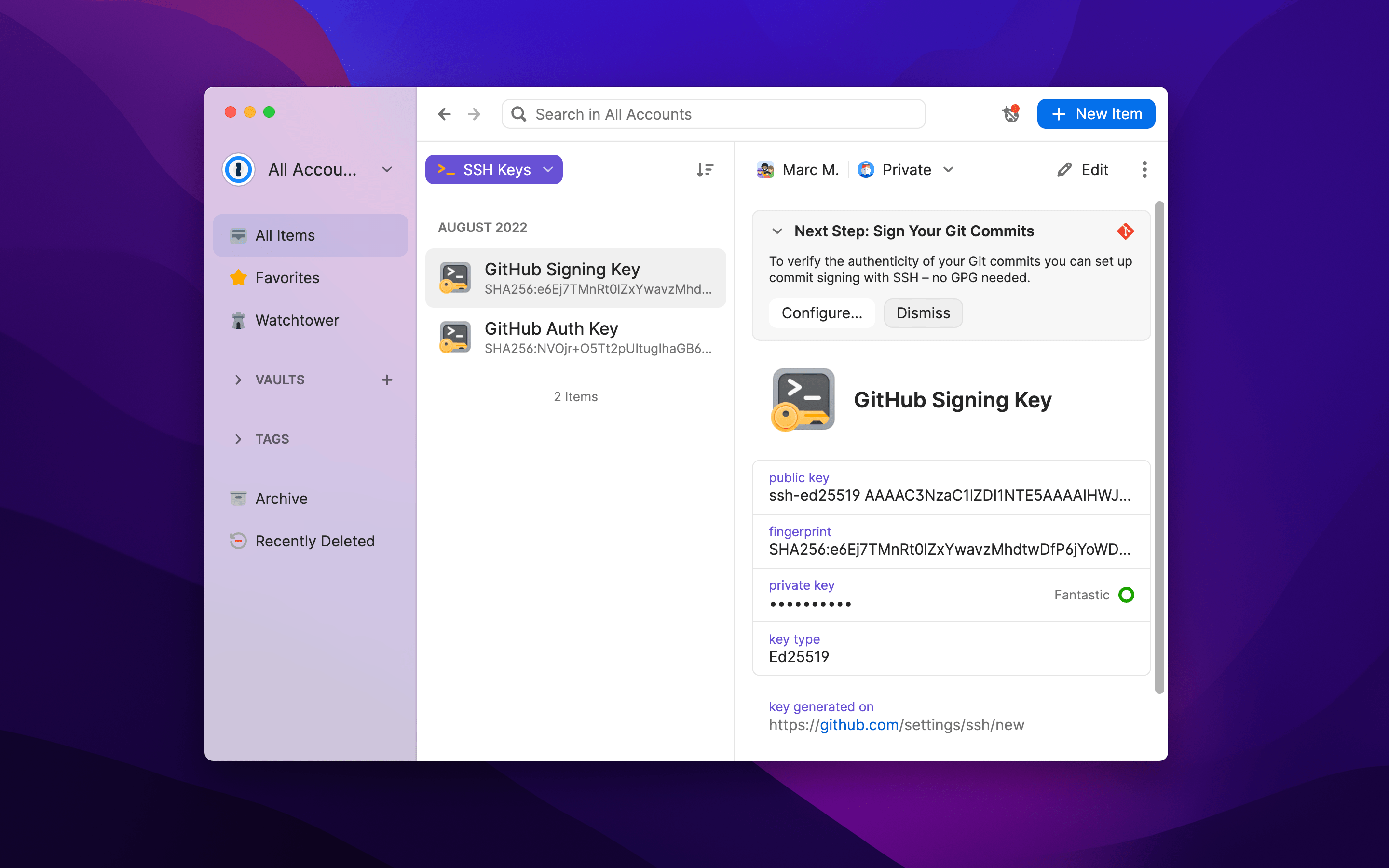
In less than 10 seconds, you have created a new SSH key to be used for signing commits. Now, you can proceed to 1Password on your desktop to configure your .gitconfig file to sign with that new SSH key. Just open the latest version of 1Password 8 for Windows, Mac, or Linux, navigate to the key you just created, and select the “Configure” option in the banner displayed on top.
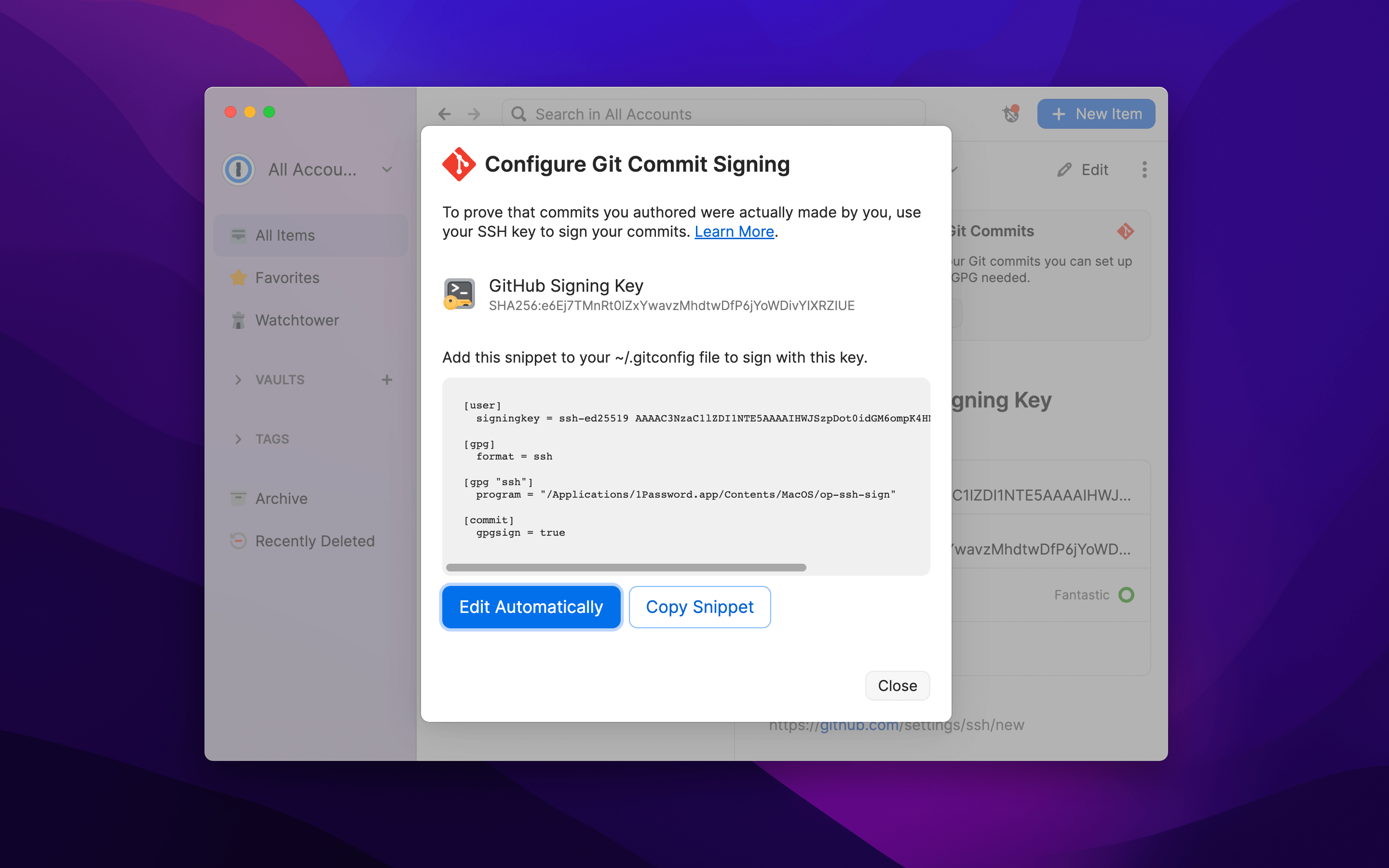
This will open a window with a snippet that you can add to your .gitconfig file. Select “Edit Automatically” and 1Password will update your .gitconfig file for you with a single click. Or, if you need a more advanced configuration, you can copy the snippet and do things manually.
Your key is now ready to sign Git commits.
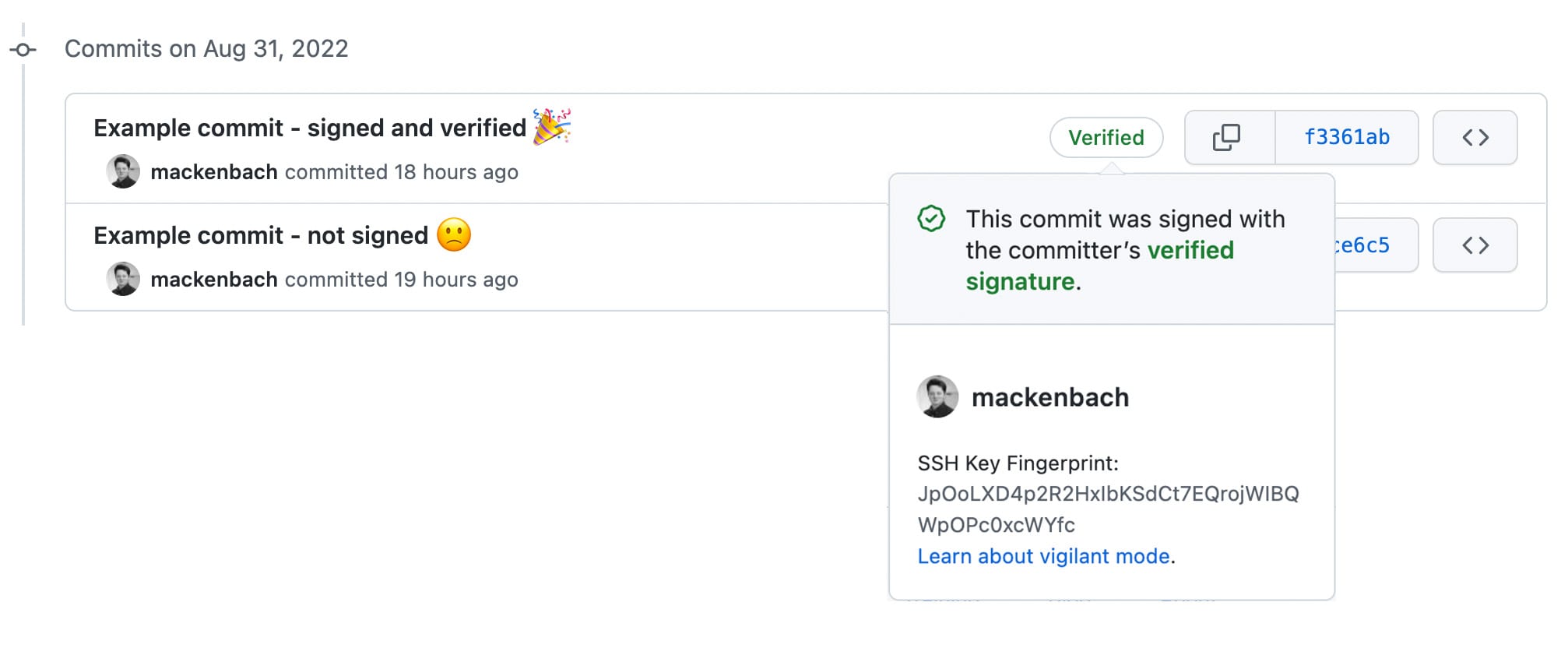
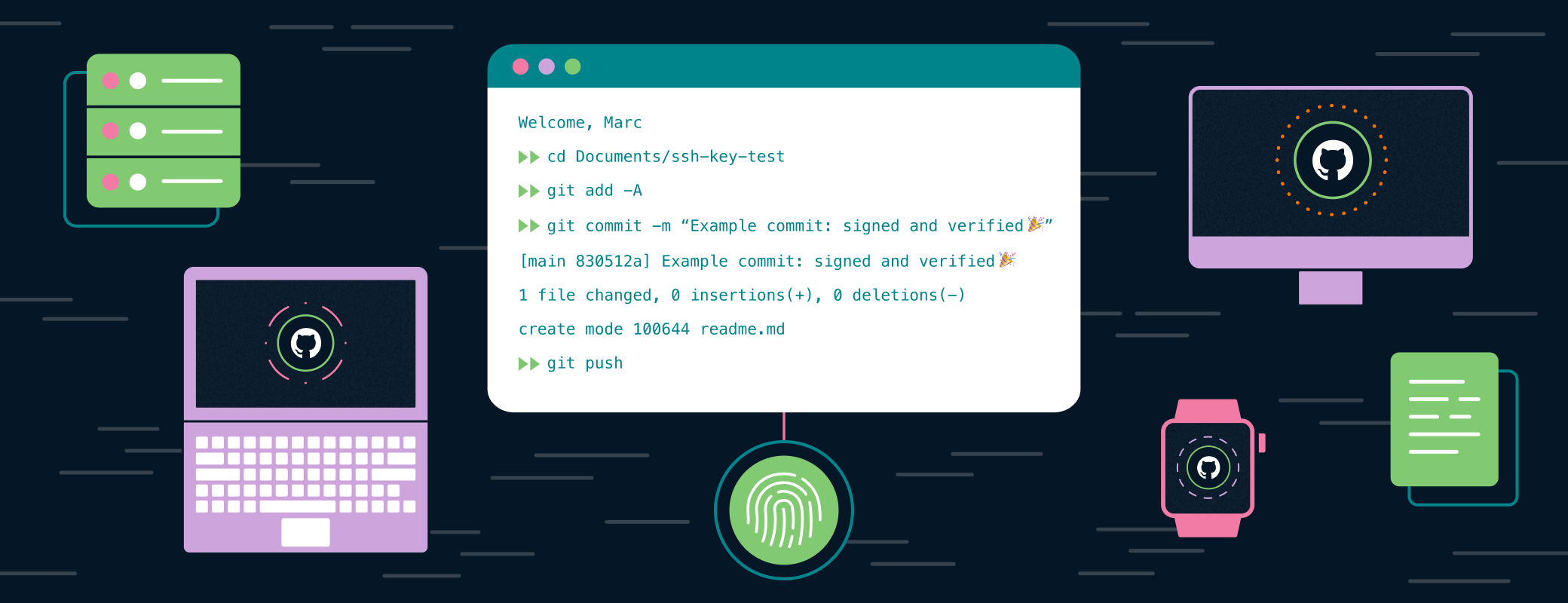
Now when you commit code, 1Password will use your new SSH Key to sign. All you need to do is scan your fingerprint. And once you push to GitHub, you’ll see that beautiful green “verified” badge on the timeline. (There’s something nice about GitHub validating your existence.)
Signing commits adds a layer of protection for your codebase and, ultimately, your customers. This is especially true if your team actively enforces signature verification to prevent unsigned commits from being pushed to your repositories.
Now is the time to make it happen. Follow the steps above, or visit our developer documentation for a detailed guide that can help with more advanced implementations, then sign away!
 by Marc Mackenbach on
by Marc Mackenbach on