1Password® Extended Access Management includes (among other things) a device trust agent.
This agent serves as part of a user’s authentication process with their company’s SSO – for instance, Okta.
What that means is that, with 1Password Extended Access Management, when devices are out of compliance, users can’t log into their Okta-protected cloud apps until they’ve resolved the issue.
This change has several implications for IT admins and end users:
End users can no longer ignore device security problems – they have to fix them in order to do their jobs.
IT teams can ensure that your entire fleet gets compliant with no interventions from them, which is particularly important for urgent security issues like browser and OS patching.
1Password Extended Access Management can help your team with its Zero Trust/device trust initiative since we now restrict access to sensitive resources based on device health.
For now, 1Password Extended Access Management is compatible with Okta and Microsoft Entra, with more IdP integrations coming soon. We’re going to spend the rest of this blog post digging into how our Okta integration works, and how the integration fits into the 1Password Extended Access Management product as a whole.
What is Okta?
Okta is an Identity-as-a-Service (IDaaS) platform, which in turn is a subset of the Identity and Access Management (IAM) field. Okta provides organizations with a suite of powerful identity management features for their workforce.
Why we integrated with Okta
For a device trust product to be effective, there have to be consequences for devices that are out of compliance. (Jason Meller wrote more about this idea in Honest Security). Eventually, we realized that the best and least invasive way to ensure compliance is to make device security part of authentication. That, in turn, required us to work with SSO providers.
We chose to start with Okta because we truly value how much they have invested in their platform, as well as their impact in the SSO community. Okta has an intentionally narrow focus and is easier to use compared to similar solutions, and many of our existing customers were already Okta users.
How our device trust agent integrates with Okta
1Password Extended Access Management integrates with the newest version of Okta Identity Engine. What makes Okta Identity Engine different from traditional SSO providers is its ability to utilize custom authentication hooks at each step of the authentication and authorization process. Thus, it drives user behavior more effectively than traditional SSO methods.
In Okta’s authentication flow, 1Password Extended Access Management’s agent functions as a possession factor. That is, the presence of the agent on a device is a precondition for authentication, so only devices that have the agent and pass our compliance checks can log into their Okta-protected apps.
1Password Extended Access Management also ensures that only the registered device owner can authenticate. This means that phished credentials become a problem of the past. Without the physical work computer present, credentials alone won’t satisfy authentication. And even if credentials are compromised, the device trust solution comes integrated with our powerful Enterprise Password Manager, which can alert users to stolen credentials, keep passwords safe, and even provide passwordless authentication.
A quick guide to Okta products
Okta has several applications and iterations, which can get a bit confusing. Here’s a brief list of some other terms you may encounter.
Okta Identity Engine: Okta Identity Engine consists of a sequence of steps to authenticate and authorize users. Identity Engine is the updated version of Okta Classic and is supported by 1Password Extended Access Management.
Okta Classic: Okta Classic is the first iteration of Okta SSO and the predecessor to Okta Identity Engine. 1Password Extended Access Management does not integrate with this version.
Okta Verify: Okta Verify is an MFA (multi-factor authentication) mobile app that is compatible with both version of Okta, although with significant improvements in Okta Identity Engine.
Okta FastPass: Okta FastPass allows users to sign into Okta without using a password, and essentially adds FIDO2 auth to Okta Verify. With FastPass, users are generally authenticated through their device’s biometrics. FastPass cannot be used without Okta Verify.
- For those using Okta Fastpass, Okta offers some basic device based conditional access abilities, but it’s primarily concerned with verifying user identity. 1Password Extended Access Management’s role is to complement it by running a robust series of checks on every device.
1Password Extended Access Management and Okta factor sequencing options
There are several authentication methods available with Okta and 1Password Extended Access Management today, all of which employ our agent as a possession factor:
Classic 2FA - Okta Password + 1Password Extended Access Management
Passwordless - FIDO2 + 1Password Extended Access Management
3FA - Okta Password + 1Password Extended Access Management + Biometric/Posession Factor (Multiple options, including Okta Verify and YubiKey)
For a more detailed guide to factor sequencing, check out our documentation page.
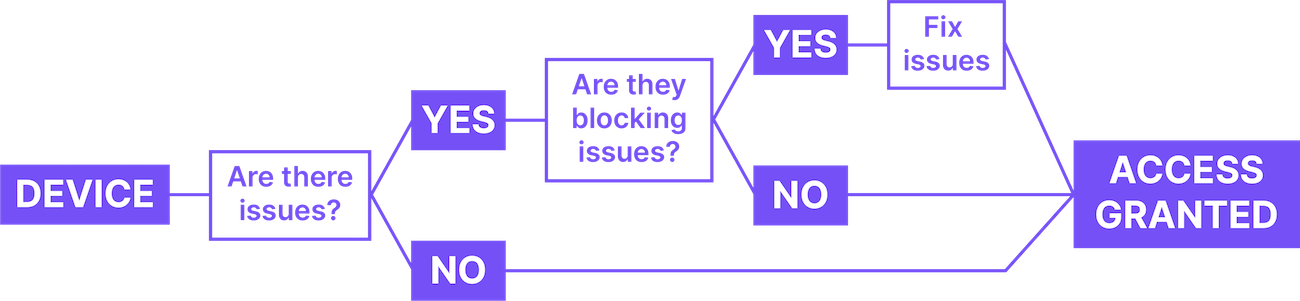
Regardless of the authentication methods used for Device Trust, the overall process flow works similarly.
When a user initiates the authentication process after signing into Okta, a signed SAML request is sent from Okta to the agent.
After this request is sent, 1Password Extended Access Management validates it and checks in with the agent installed on the device.
1Password Extended Access Management then runs its checks against the user’s device to determine if there are currently any blocking issues.
If blocking issues exist, the user is required to fix them before finishing the authentication process.
After this process is complete, a signed SAML response is sent back to Okta from 1Password Extended Access Management. Okta then validates the response and authenticates the user.
How this works for end users
It’s important to understand that while our SSO integration is central to our product, it’s not the only way users interact with us. After all, we wanted to make 1Password Extended Access Management part of authentication and block non-compliant devices, but we didn’t want to create any needless friction (or unpleasant surprises) for users.
To that end, not all issues trigger an immediate block. IT can determine how long the grace period should be before users are blocked, depending on an issue’s level of urgency.
So, hand-in-hand with our Okta integration, we created an app that alerts users to blocking issues as soon as we detect them. That way, a user never learns that their device has an issue when they’re trying to log in for an important meeting.
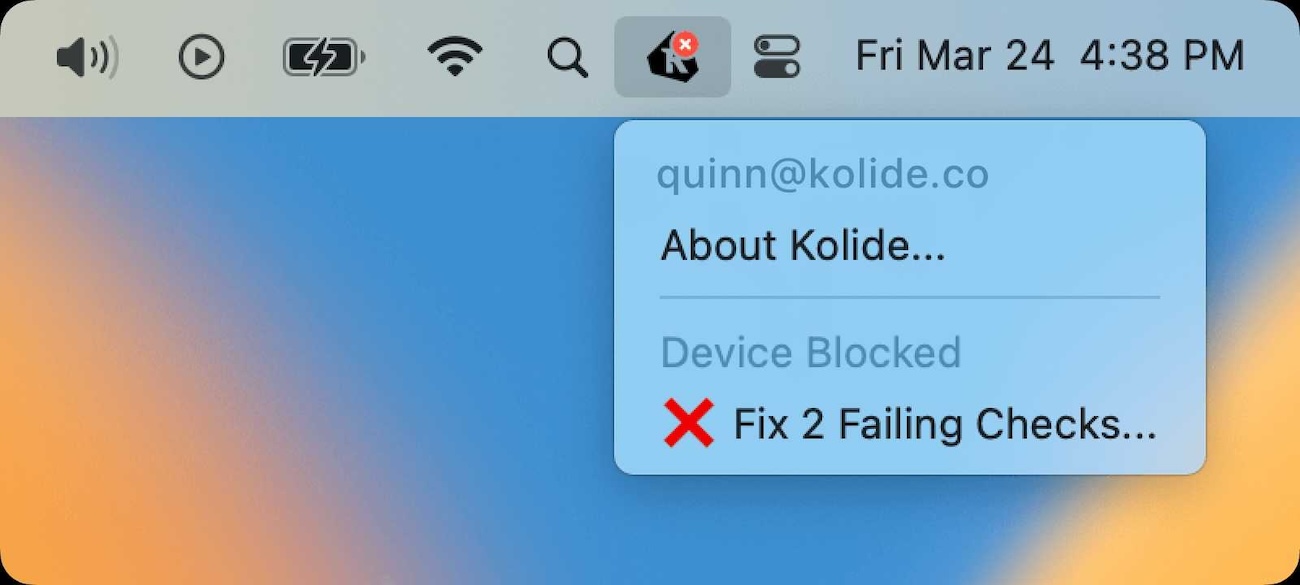
The menubar application directly integrates with the desktop agent. When there’s an issue with a device, the menubar app gives users an alert, telling them:
What the problem is.
How long they have to remediate it before their device will be blocked from authenticating.
From there, it lets users navigate to remediation instructions with just one click.
We chose this method because it saves time and energy for IT admins and end users alike. For instance, browser updates need to get done, but it’s typically fine if users get them done within a week or so, and pushing a forced update through an MDM might interrupt workflows. It also requires needless busywork from IT, since most users have the knowhow needed to update Chrome.
With our menubar app and Okta integration, users are told that if they fail to fix the problem within a certain amount of time, they’ll be blocked from authenticating through Okta. But until then, they have the flexibility to remediate issues, on their own, according to their needs.
What’s next?
If you have Okta and are interested in 1Password Extended Access Management, reach out for a demo!
 by Caitlin Cabrera on
by Caitlin Cabrera on