With 1Password Extended Access Management, customers can now require users to secure unencrypted SSH keys on their devices by importing them into 1Password before they can access sensitive company data.
Like many, you might assume that software developers have an advantage over non-technical end users when securing their devices. After all, they understand how computers work at a deep level, and reasoning about security is a significant part of software engineering.
Not exactly. Software engineers have access to organizations' most sensitive systems and intellectual property, but they are also the most likely group to successfully advocate to be an exception to the security and IT team’s normal practices. Additionally, they regularly encounter, handle, and even generate sensitive credentials, making them a prime target for bad actors. In fact, in Verizon’s 2024 Data Breach Investigations Report, the top “initial action” taken by attackers in the breaches analyzed was “stolen credentials.”
The credentials developers encounter are everywhere. They live in the code they write, the terminal, and they are even the way most developers sign into remote servers. Once you have one of these credentials, that’s often all it takes to access the system or service it’s associated with because, more often than not, it’s running right on the public Internet.
Developer secrets leaks are a pervasive problem, but have been especially acute for the financial services industry recently. Among the top 200 financial services apps in the United States, United Kingdom, France, and Germany, 92% of financial services apps contained easy-to-extract secrets that could be used in scripts to steal data (Mobile App Security Report, Approov, 2023).
Existing approaches like privileged access management (PAM) only secure the systems and credentials you manage. What happens to credentials stored on local devices or unmanaged devices? 1Password Extended Access Management goes further by identifying and protecting systems outside your control, including BYOD devices your employees use for work.
For example, with 1Password Extended Access Management, admins can check for insecure SSH keys on any devices their employees use for work before those employees sign in to sensitive apps. If unencrypted SSH keys are found, users are prompted to secure them by importing the keys into their 1Password vault. If they ignore the prompts, access to sensitive apps can be automatically blocked end-users have complied with the request.
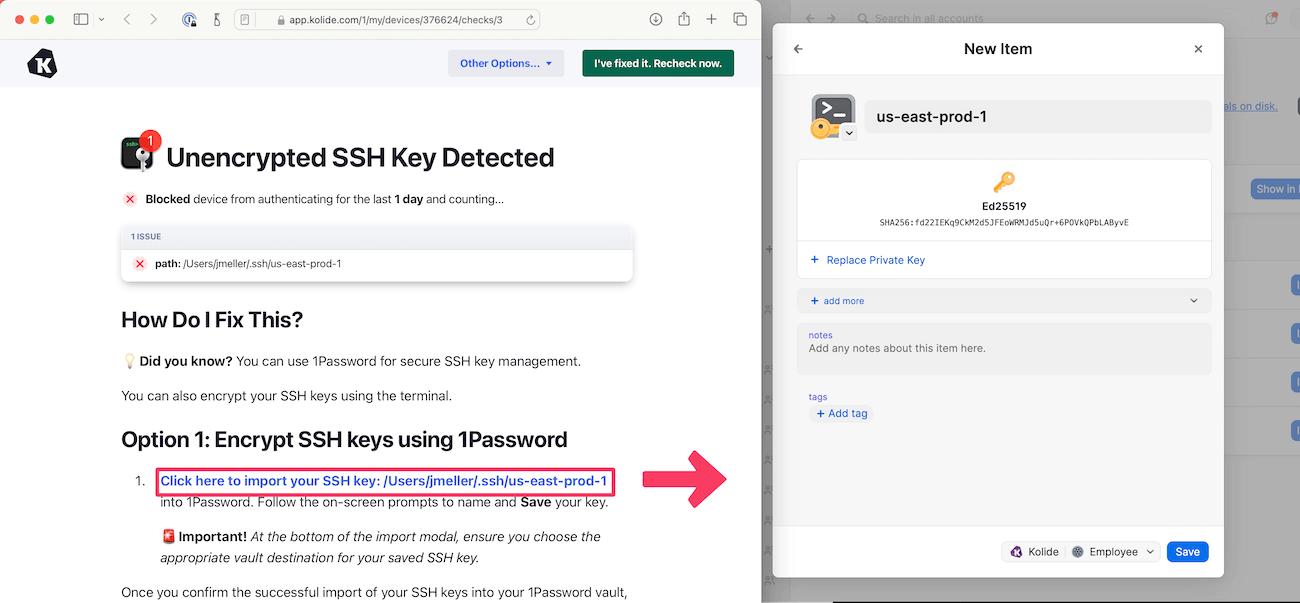
This combination of detection, providing the end-user with tools to fix the problem, and finally, proportional consequences if they don’t take care of the problem, is a potent approach that results in a miracle: your developers meaningfully participated in your company’s remediation story, with near-perfect efficacy.
Out of sight, out of mind
SSH keys, or Secure Shell keys, are used by IT and engineering teams to securely authenticate and establish encrypted connections to remote servers and systems. Compromised keys can lead to unauthorized access, security incidents, and potential loss of sensitive information.
SSH keys stored on devices can pose significant security risks when they are unencrypted or use outdated encryption formats. Unencrypted SSH keys are vulnerable to unauthorized access, as they can be easily exploited by attackers who gain access to a device. Similarly, SSH keys that use outdated encryption formats are susceptible to modern cryptographic attacks.
Unfortunately, both security teams and developers usually lack visibility into the health of SSH keys on devices. Once developers create an SSH key, it gets added to the ~/.ssh directory on their device. They may use it daily, but will likely never check the encryption algorithm again.
Better security, better productivity
In January, we announced that 1Password Watchtower now provides SSH key security insights for individual users. And now administrators can configure SSH security checks for every device in their fleet.
When 1Password Extended Access Management performs a check, it will alert users to any unencrypted SSH keys on their devices. They will be prompted to import their unencrypted keys into their 1Password vault for safekeeping.
Once saved in 1Password, SSH keys are end-to-end encrypted in vaults and available for use in developer’s day-to-day workflows via the built-in SSH agent. They can authenticate SSH connections and sign Git commits with biometrics, reducing friction and improving security.
Getting started
Admins can easily configure a pre-built contextual access policy for unencrypted SSH keys by visiting the “Checks” tab within the Device Trust component of 1Password Extended Access Management. From there, they can choose whether to warn users for a certain period when an unencrypted key is found or begin blocking access immediately.
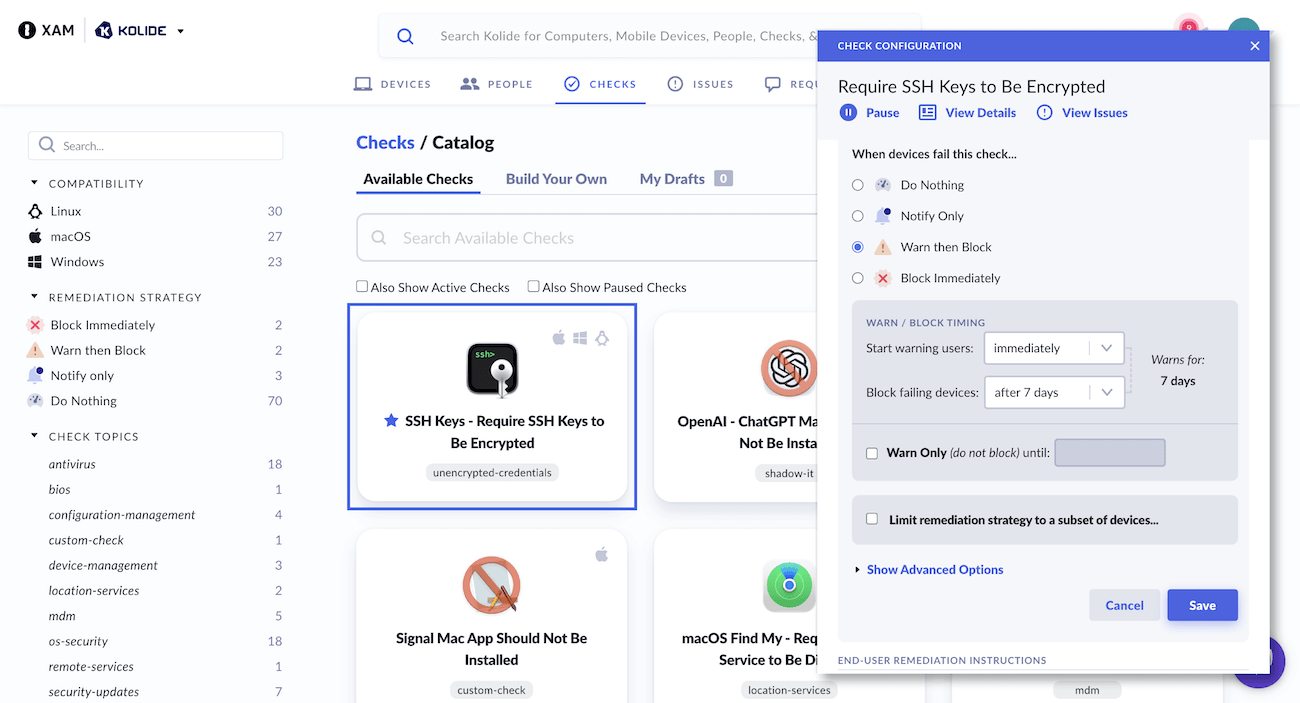
If devices fail this check when attempting to sign in, users will be provided with step-by-step instructions on how to move their unencrypted keys into 1Password. As soon as the problem is resolved, they will be able to recheck the device and continue signing in without any intervention from IT.
Secure developer devices, code, and infrastructure
1Password Extended Access Management ensures the security of your devices, and works with 1Password Enterprise Password Manager to extend that protection to your code and infrastructure.
With 1Password you can:
- Secure developer devices: Protect your systems by identifying and fixing security risks from unencrypted SSH keys stored on employee and BYOD devices.
- Keep secrets out of code: Help developers identify exposed secrets in code, import them into 1Password, and replace secrets with references.
- Reduce secrets sprawl: Centralize and manage secrets across cloud environments in 1Password, and use CI/CD and infrastructure integrations to securely deploy your applications.
Developer security tools are included in all 1Password plans. You can explore the documentation to learn more, and schedule a demo to see 1Password Extended Access Management in action.
 by Jason Meller on
by Jason Meller on


