The Access-Trust Gap refers to the security risks posed by unfederated identities, unmanaged devices, applications, and AI-powered tools accessing company data without proper governance controls. This blog defines the gap, explains why it exists and why it poses a threat to security, and outlines various approaches security and IT leaders can take to close it.
In life, we’ve all encountered the gaps between the idealized world and the world as it is.
You’d love your favorite sports team to have a perfect season, but you’re prepared for them to lose a few games.
Retailers want to sell their entire inventory, but they plan for a certain percentage of their goods to be damaged or stolen.
IT and security professionals try to maintain complete control and visibility over who has access to company resources, but acknowledge that this is difficult to realize in practice.
These gaps are acceptable, until they are not.
When your favorite team’s defense can’t stop a single opponent from running up points, it might be time for a new coach (or to stop being a Browns fan). If a store’s clerks can’t stop merchandise from being shoplifted, they need a security guard. And if a company’s security stack can’t keep untrusted users, apps, and devices from accessing sensitive data then it might not be up for the job.
This blog explores that third example, which we call “The Access-Trust Gap.”
What is the Access-Trust Gap?
The Access-Trust Gap refers to the security risks posed by unfederated identities, unmanaged devices, applications, and AI-powered tools accessing company data without proper governance controls. You can think about it as the difference between the users, applications, and devices that a business trusts to access sensitive data, and those that can access it in practice.
Put another way: every company agrees that access to its resources should be restricted to the people who need it, and that even those people need to treat it carefully. These are the most basic tenets of security, and you can see them every day in the physical world; no bank will let some random person waltz into the vault, nor will they let a bank teller take a duffel bag full of cash to the nearest bar.
In cybersecurity, however, determining trust and restricting access is much more complex, leading to unsanctioned access to sensitive data.
In the inner circle of the Access-Trust graphic, you can see the types of access that are generally considered trustworthy because they are managed by a company’s IT team.
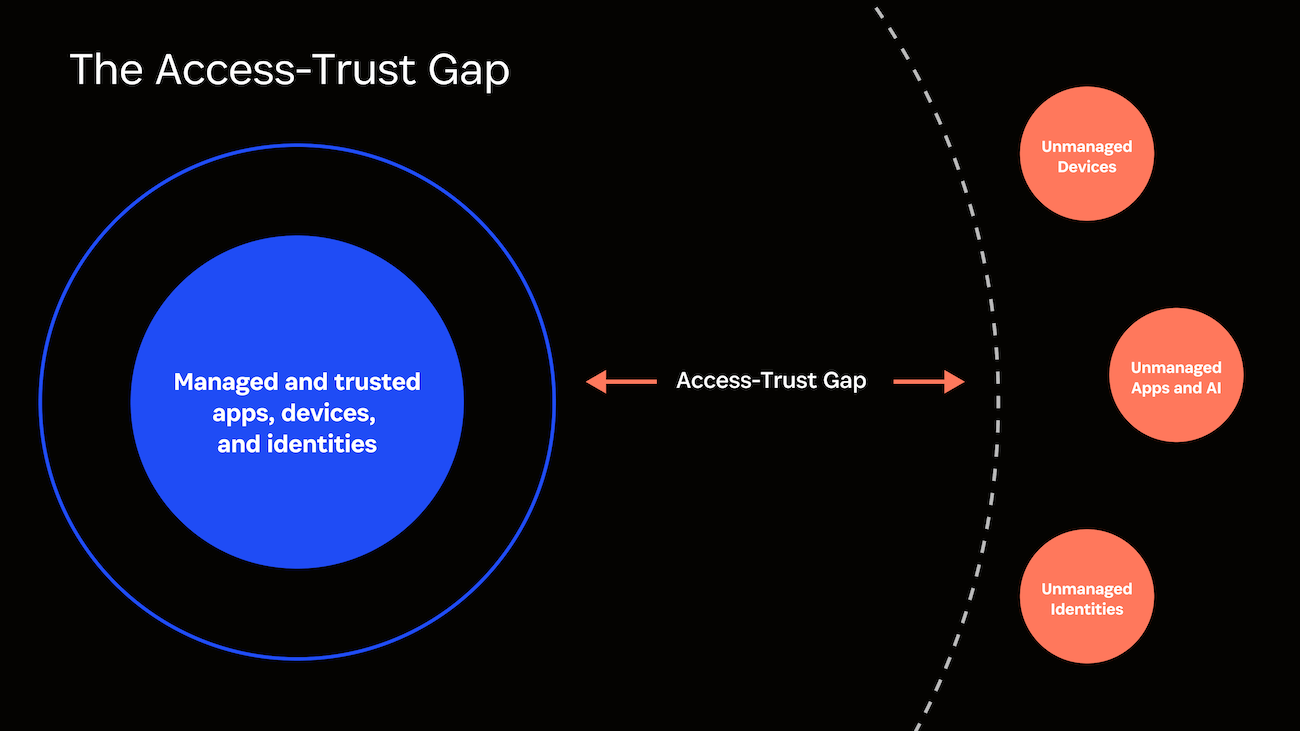
- The devices in the “trusted” circle are company-owned computers and phones that are usually managed via MDM, which can enforce certain security settings and remotely lock and wipe devices if needed.
- When it comes to users, “trusted” means employees whose access is centrally managed via an identity provider such as Okta, Microsoft, or Google.
- Trusted applications are those that are approved of and managed by the IT team, who can provision and deprovision users as needed.
Unfortunately for security professionals, today a lot of work takes place on applications and devices outside this trusted inner circle. Users often work on their personal, unmanaged devices. Teams increasingly rely on “shadow IT” applications that IT doesn’t even know about. And not all end users are employees at all – some are guests and contractors, and some are AI agents with needs, behaviors, and risks unaccounted for by traditional security tools.
To understand how this plays out in real life, imagine a chain of events in which:
- A third party contractor
- Uses their personal device to log into
- An unapproved file-sharing application used by your employees without IT being aware
Every element of this path presents risk. The contractor isn’t enrolled in Okta, so they can’t take advantage of its multi-factor authentication (MFA) for secure sign-in. The contractor’s device doesn’t have EDR installed, so it could be infected with malware. The file sharing application is known to be prone to breaches, so the sensitive data stored there isn’t really secure. Each issue compounds the next, creating a cascading escalation of risk that can quickly overwhelm conventional security measures.”
How big is the access-trust gap?
Research indicates that “untrusted” access is rampant in businesses of every size and in every industry. 1Password’s State of Enterprise Security report found that over a third of workers use unapproved applications or tools for work, with tech workers leading the pack.
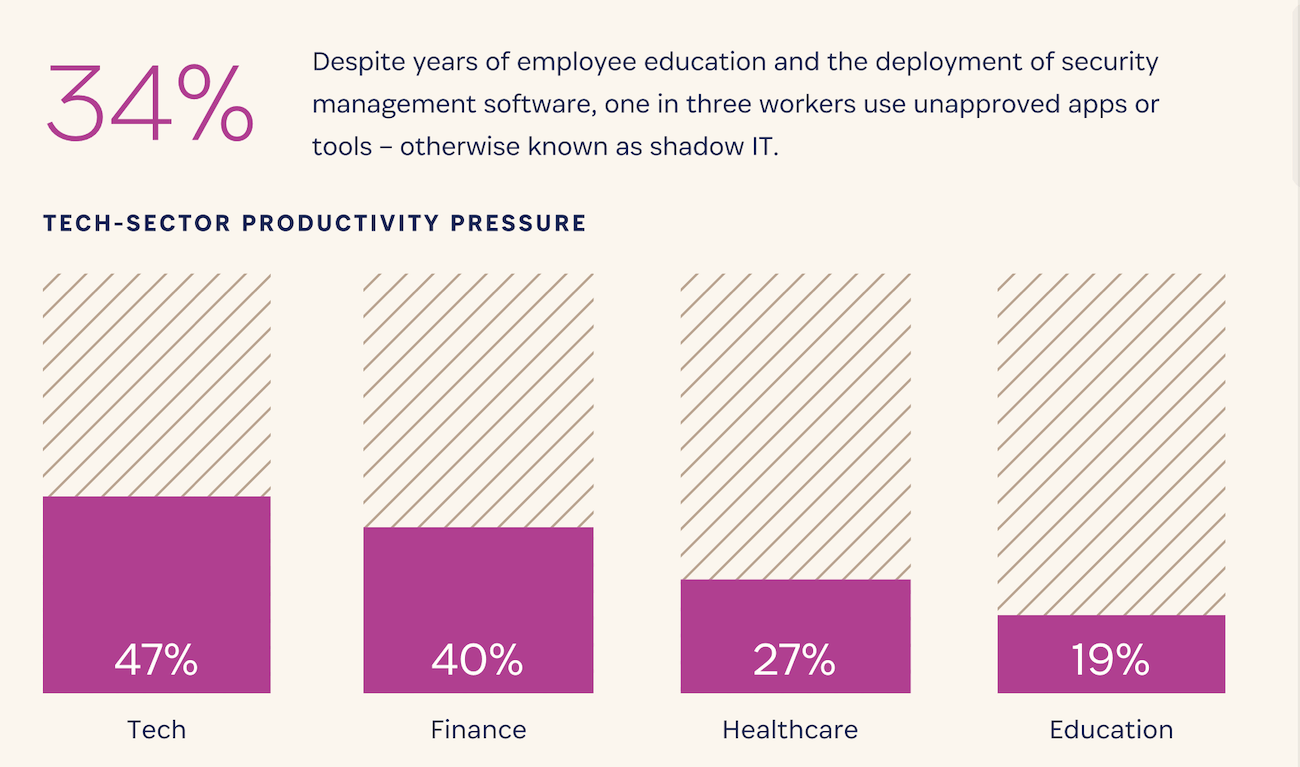
Meanwhile, a 2023 survey by Kolide found that 47% of companies allow their workers to access company resources on unmanaged devices.
So, a little unscientific, back-of-the-napkin math tells us that around half of companies have these vulnerabilities. (In reality, the number is probably bigger, because these problems are inherently invisible until something goes wrong.)
This seems bad. How did we get here?
here are two big factors that have widened the Access-Trust Gap in the past few years:
- The proliferation of SaaS apps
- The growth of hybrid work.
In the first case, the number of apps used by the average organization has exploded since the 2010’s. One study found that in 2015, the average company used 8 SaaS apps, by 2020 it had grown to 80, and by 2022 it was a whopping 130 apps. Moreover, workers increasingly seek out and purchase these apps without IT’s knowledge or approval. (That doesn’t mean your company isn’t paying for those apps, by the way, it just means that workers make a budget instead of an IT request.)
Ideally, you would want all these apps protected by SSO, so authentication is more secure and IT can manage identities from a central dashboard. Unfortunately, that’s extremely difficult to achieve even for the apps you do know about, given the dreaded SSO tax that frequently makes this feature unaffordable.
The other factor at play is the growth of a “work-from-anywhere” culture, which had been building for a while but received a major boost from the pandemic. When workers left the office, many companies adopted BYOD (Bring Your Own Device) policies, or simply accepted that they couldn’t stop users from working on their preferred, personal devices. And why couldn’t they stop them? Because of all those SaaS apps that you can log into from any device, without needing to be on a corporate network or VPN.
Thus, you can see that these three seemingly disparate problems – unsecured identities, apps, and devices – are really all part of the same phenomenon.
Closing the Access-Trust Gap
Let’s be clear: there is more than one way to address the problems we’ve just gone over.
For example, you could:
- Eliminate BYOD by buying every user a company-owned phone and laptop
- Roll out VDI or similar software for third-party contractors to control their access
- Put every application behind SSO
- Manage employee devices to the degree that they are unable to access any application or website not approved by IT.
The problem with those tactics is that they are extremely expensive, labor-intensive, and damaging to productivity and worker experience.
Now let’s explore how 1Password solves the Access-Trust Gap through 1Password®️ Extended Access Management (XAM). As you might guess from the name, our approach is based not on eliminating all the forms of access that fall outside traditional solutions, but extending protection to them.
Devices
The goal is to allow access to company resources only from devices that are both recognized as known (belonging to an employee) and verified to meet security and compliance requirements. This concept is known as device trust.
There are two options to achieve this:
- 1. Ban BYOD. Prohibit any unmanaged (not enrolled in MDM) device from authenticating to your systems.
- 2. Secure BYOD. Allow unmanaged devices to authenticate, but only if they meet your security requirements (updated software, firewall turned on, etc.).
Regardless of which route you take, 1Password Extended Access Management can help you get there. 1Password Device Trust makes the device itself into an authentication factor, so if a device doesn’t have the agent installed, it can’t log into the company’s apps. That means that if device trust is integrated with a company’s IdP, a bad actor with stolen employee credentials is out of luck unless they also have that employee’s device.
If you want to eliminate BYOD, you could make MDM enrollment a requirement for authentication, and thus lock out personal devices.
Alternatively, you could use device trust to manage devices outside the scope of MDM. Unlike MDM, 1Password Device Trust is suited for personal and contractor devices, because it allows the user to maintain much more agency over their device, and (deliberately) does not have the ability to wipe devices remotely.
That being said, device trust has a lot to offer for endpoints that are enrolled in MDM. It provides admins with much more comprehensive and customizable abilities to check for various device properties. 1Password Device Trust includes a library of over 100 pre-built checks, plus the ability to write custom checks. By contrast, MDM solutions can only manage a few types of issues.
An end user’s laptop can be enrolled in MDM and still be running an unpatched browser, using unsecured software, and have plaintext credentials sitting on its hard drive. Device trust, on the other hand, would not permit a user to authenticate until they have fixed these issues.
In conclusion, there’s a bigger argument to be had as to whether those managed devices in the inner circle of the Access-Trust Gap graphic should really be considered “trusted” at all, but for now, let’s move on to the other elements of 1Password Extended Access Management.
User identities and AI agents
Here, the goals are threefold:
- Ensure with a high degree of confidence that a user is who they claim to be – let’s call that secure authentication.
- Easily grant and revoke access so workers have the resources they need, but avoid excessive permissions, AKA role-based access control (RBAC).
- Quickly and easily grant and remove access when someone joins or leaves the company, AKA onboarding/offboarding.
In all three cases, the go-to security solution is single sign-on (SSO), but managing those integrations can be difficult and cost-prohibitive, and SSO is not without shortcomings. Some users – such as “break glass” accounts and legacy users – can authenticate without SSO, which means they can’t be managed through it. Also, SSO was not designed to protect AI agents.
1Password Extended Access Management approaches this problem from multiple angles. Trelica by 1Password allows for the discovery and centralized management of all SaaS apps and users, even those unmanaged by SSO. 1Password Enterprise Password Manager shores up authentication for apps that aren’t compatible with SSO. It ensures workers are using secure, unique passwords, as well as enabling more secure forms of authentication, such as passkeys.
When it comes to AI, 1Password’s agentic AI security capabilities help enterprises distinguish between humans and AI agents, apply access controls dynamically, and scale autonomous AI safely. 1Password enables productivity and enterprise-grade security by eliminating hardcoded secrets, supporting least-privilege access, and delivering visibility into AI agent interactions, all within a Zero Trust framework.
Key capabilities available today include:
- 1Password SDK for Agentic AI : Programmatic management of vault items allows developers to build AI workflows that securely read, write, share, and rotate secrets at runtime.
- 1Password Service Accounts: IT and developers can create scoped API keys for AI agents to retrieve secrets from 1Password vaults, without exposing full human credentials.
- Enterprise Password Manager: Provides vaults to securely store secrets for AI agents to access service providers to automate tasks, as well as provide audit logs to track machine identity for enterprise security teams.
Applications
Finally, IT and security professionals need to get visibility into the applications end users employ for work. That in itself is a huge challenge, because you have to collect relevant data without accidentally scooping up information about an employee’s personal apps. But the overall goal, much like with devices, is to ensure that only apps that are known and secure can access your company’s resources.
Once you’ve identified the apps employees use for work, you can do three things:
- Ban unsanctioned shadow IT that you have determined to be a security risk or a financial burden.
- For shadow IT apps you don’t object to, implement SSO to make them more secure.
- For both managed and unmanaged apps, eliminate unnecessary access for licenses that are going unused or permission levels that are not appropriate.
The first two goals here are primarily about security, while the third is more about budget (although users who maintain access to resources after they no longer need them can lead to data breaches, as in the Drizly hack).
Trelica by 1Password enables administrators to accomplish all three goals by discovering all apps being used for work and surfacing that list to admins, indicating whether those apps are being managed by SSO, who is using them, and how often.
Conclusion: Mind the gap
As we said in the introduction, gaps are acceptable until they’re not. Once a gap becomes so wide that it’s more of a canyon than a crack, people start getting worried and writing blog posts.
We’ve now lived through years of preventable data breaches stemming from weak credentials, unsecured devices, and shadow IT – so much so that even the annual Verizon Data Breach Investigation Report is starting to sound a little fed up.
Clearly, the Access-Trust Gap is something we can no longer live with. Thankfully, with 1Password Extended Access Management, we don’t have to.
To learn more about how 1Password Extended Access Management can help close the gaps in your security stack, reach out to us here.
 by Elaine Atwell on
by Elaine Atwell on