At RSAC 2025, we announced Extended Device Compliance, a new capability within 1Password Device Trust that enforces device posture Checks before allowing access to web applications, including those not protected by single sign-on (SSO). Extended Device Compliance redefines industry expectations for device trust solutions, ensuring devices are secure and compliant even when users access apps outside traditional admin control.
The Access-Trust Gap: Securing unmanaged apps and devices
The way organizations operate has undergone drastic evolution over the past few years. Employees often work remotely, using a wide range of devices and applications. While security tools like SSO and MDM help secure IT-managed applications and devices, they fall short when users access apps outside this perimeter or use personal devices. This creates what we call the “Access-Trust Gap,” the security risks posed by unmanaged identities, devices, applications, and AI-powered tools accessing company data without proper governance controls.
Most device trust solutions work by enforcing device compliance as part of a user’s authentication to SSO-enrolled apps. But this approach has limitations: it only protects apps behind SSO, leaving many unmanaged or unknown applications out of reach. This makes it difficult for security teams to discover shadow IT, assess usage patterns, and protect sensitive data across their full app ecosystem.
1Password Device Trust takes a different approach, one designed for how people actually work today.
Extended Device Compliance is built into the 1Password ecosystem, combining 1Password Device Trust and the 1Password browser extension to confirm device health before allowing access to any web app, not just those behind SSO. Enforcement occurs directly in the browser, allowing posture Checks to be performed when a user navigates to a protected web application. The result: security policies that aren’t confined to a login screen, but follow users across browsers, devices, and the apps they rely on most.
Solving the Access-Trust Gap with Extended Device Compliance
Extended Device Compliance emerged from the need to secure the Access-Trust Gap: businesses couldn’t guarantee that devices were secure before accessing any web application. Extended Device Compliance addresses this by utilizing the 1Password browser extension to enforce real-time device Checks directly in the browser, prior to a user logging in. This helps close the Access-Trust Gap, protect sensitive data, and reduce exposure to threats like shadow IT, all without adding complexity for IT teams.
Here are the key capabilities:
- Surfaces employee application usage in a centralized admin dashboard.
- Integrates directly with the 1Password browser extension, no plugins or manual setup required.
- Leverages 1Password Device Trust and the 1Password browser extension to enforce device security Checks at the point of access.
- Guides non-compliant users through clear, step-by-step self-remediation instructions.
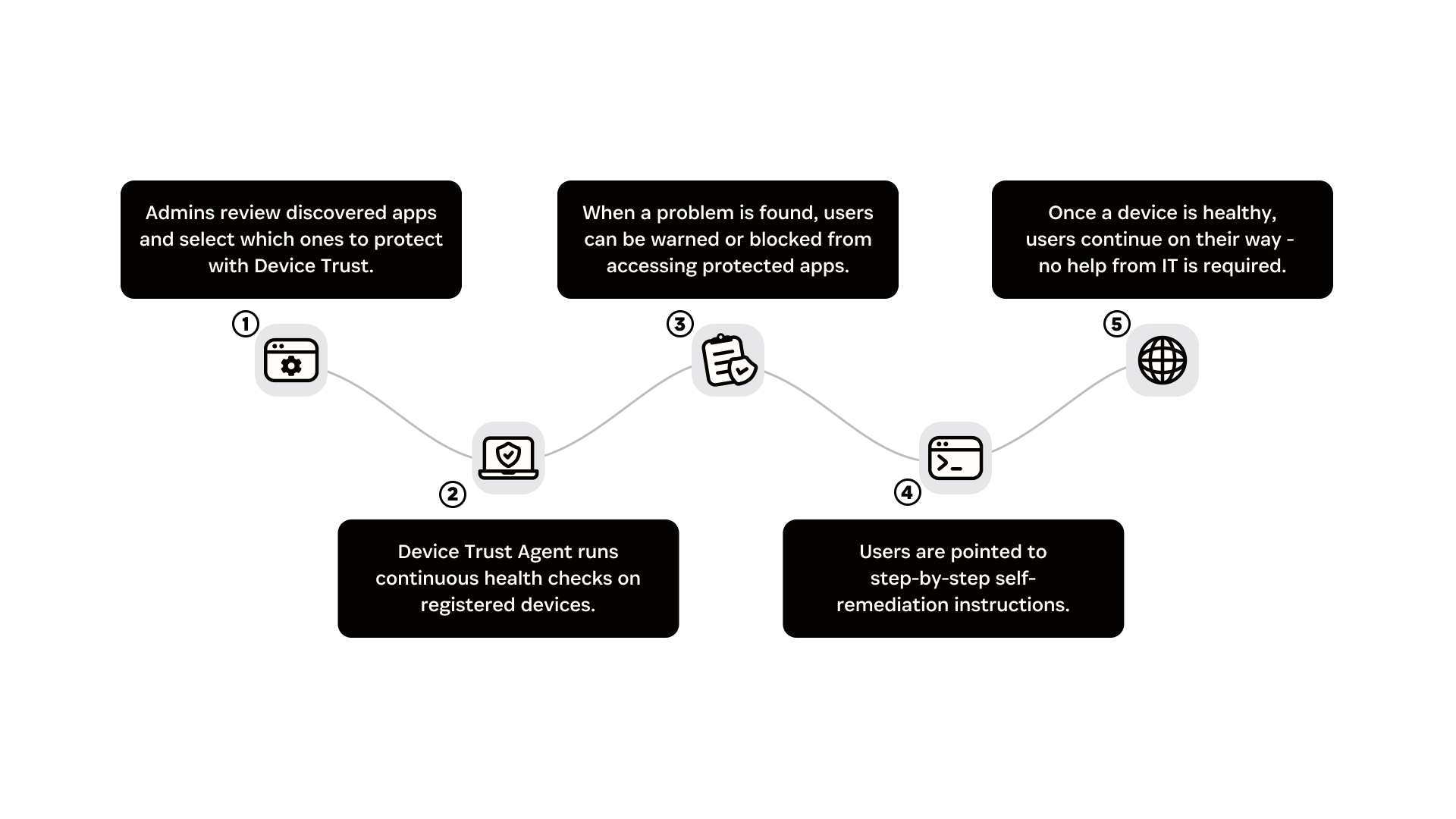
Extended Device Compliance in action
Extended Device Compliance enables organizations to enforce device security without disrupting employee workflows. Here’s what the experience looks like from an admin and end-user perspective when both Device Trust and the 1Password browser extension are running on the device.
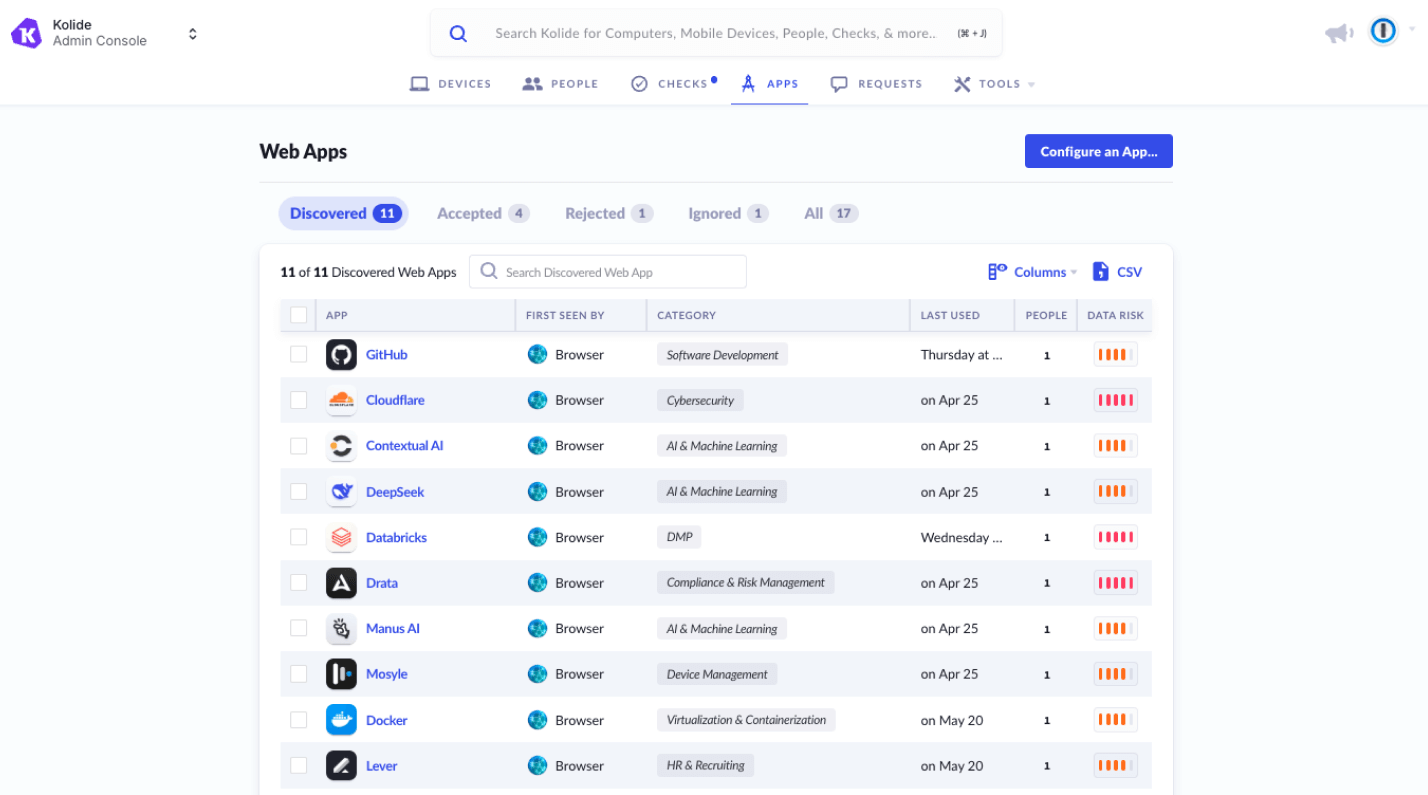
Step 1: Discover applications employees use for work
Admins gain visibility into the web apps employees use for work, including unmanaged and non-SSO apps, via the Discovered Apps dashboard. Discovery is powered by the 1Password Device Trust agent, which scans browser activity and installed desktop apps for a predefined list of work-related applications.
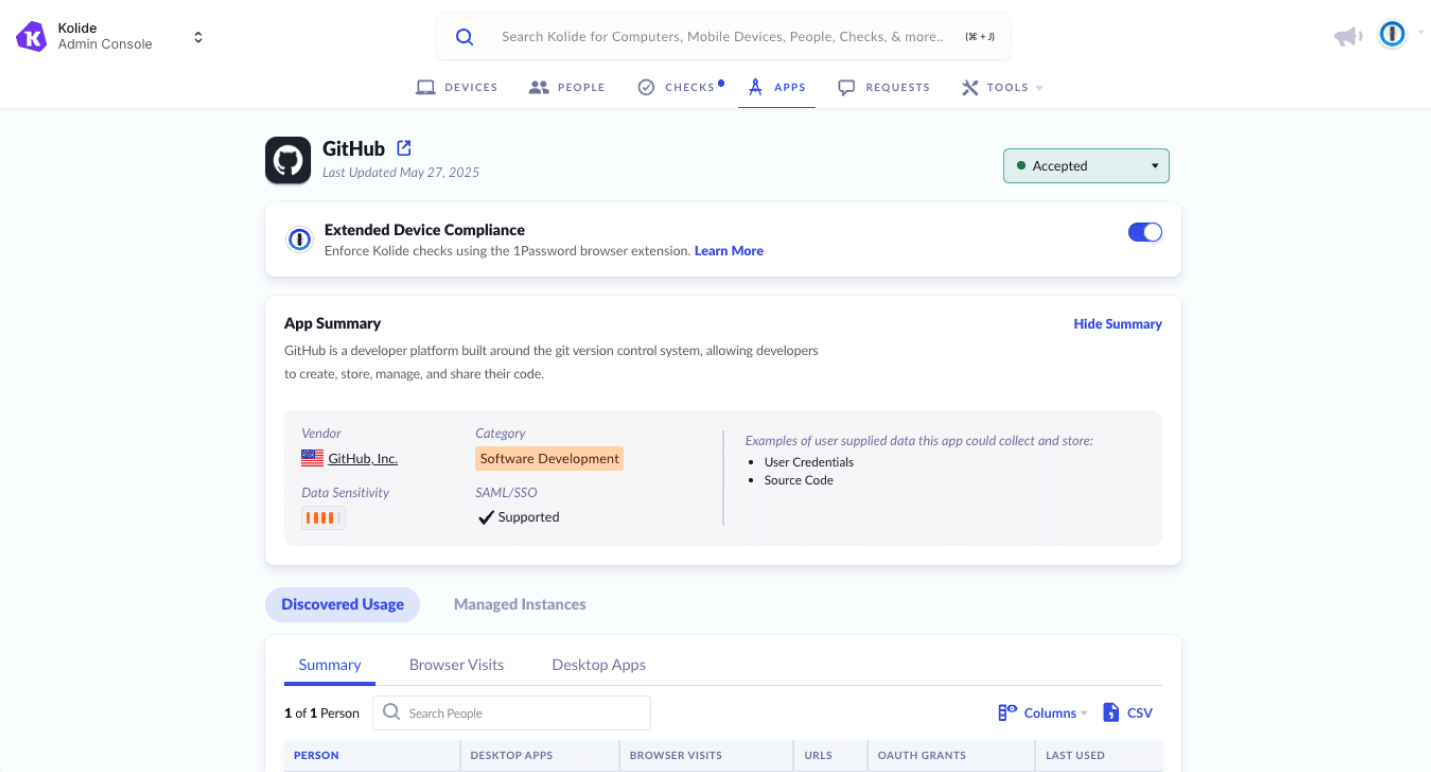
Step 2: Enable compliance enforcement on selected applications
Once discovered, apps can be protected with posture Checks by simply toggling enforcement on. To help admins prioritize which apps to secure, each entry in the Discovered Apps dashboard includes context like category, SSO support, and a data sensitivity score based on the type of information the app handles (e.g. credentials, source code, or financial data).
Step 3: Real-time device compliance Check at login
When an employee accesses a protected application, the Device Trust agent checks the device’s posture against configured security policies, such as OS version, encryption status, and other key signals.
If the device doesn’t meet policy requirements, access to the app is blocked. A clear in-browser message explains what’s out of date or missing, giving users immediate context.
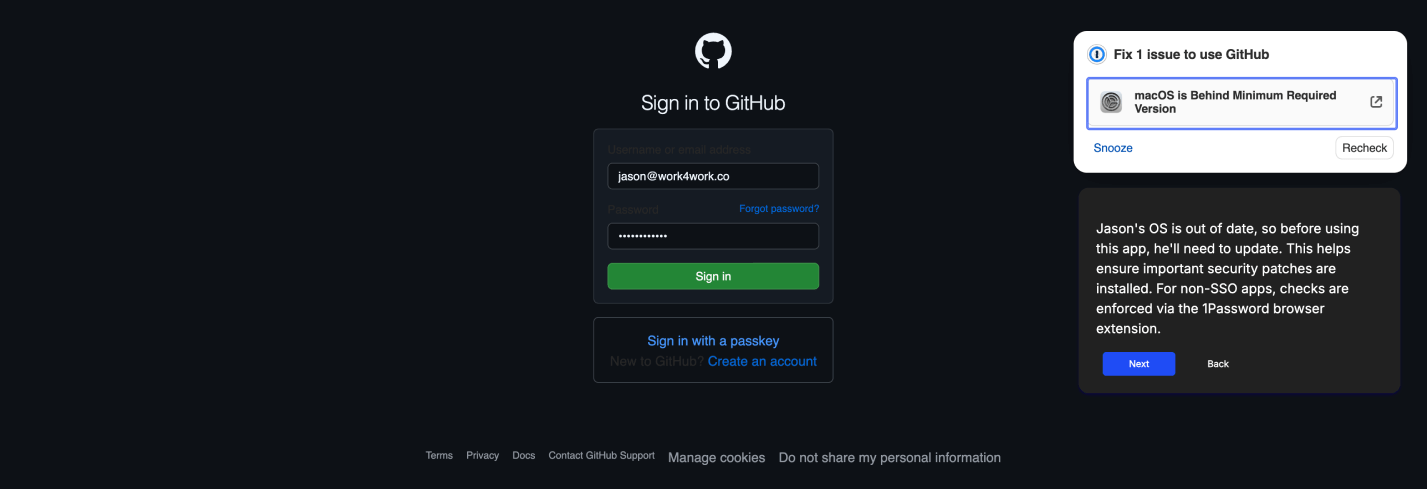
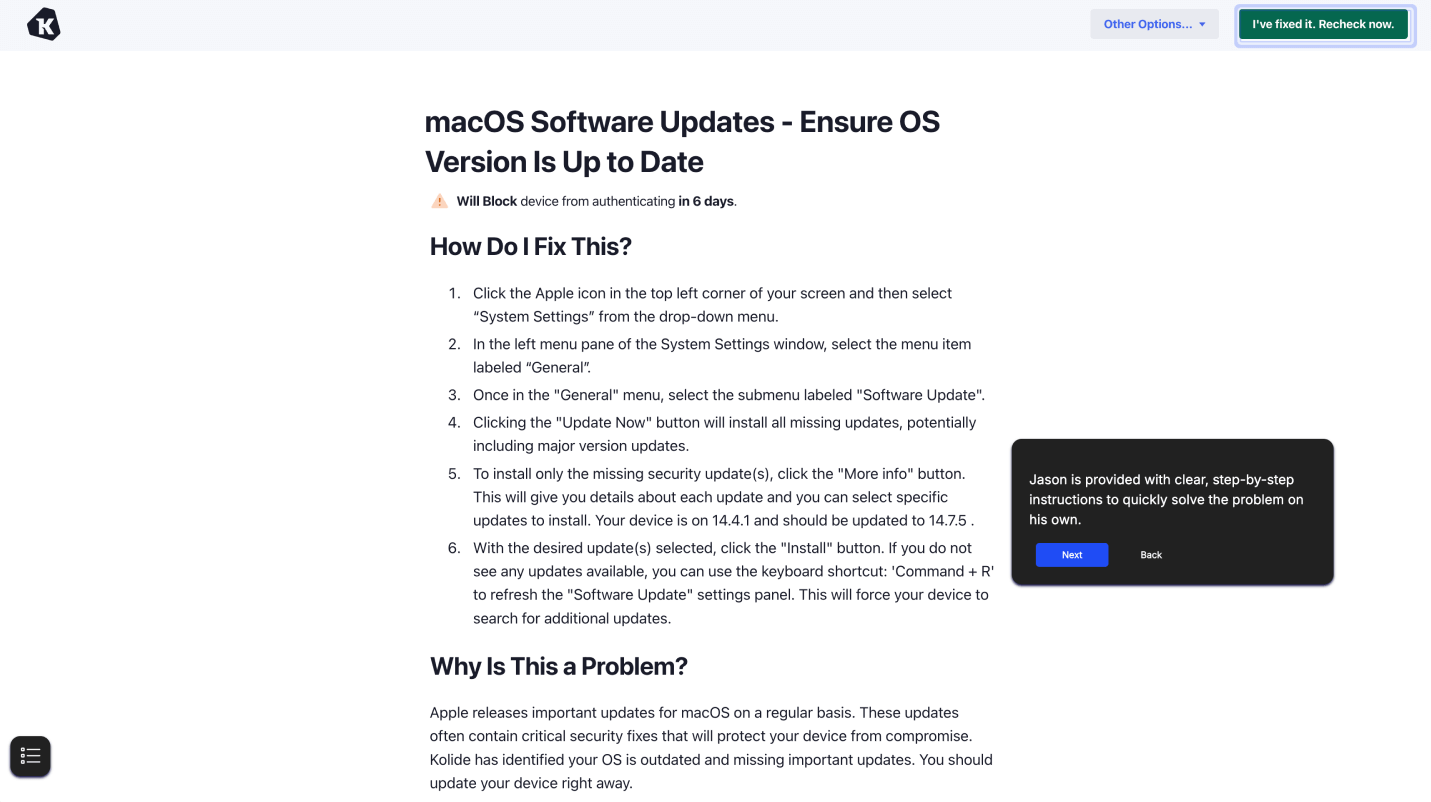
Step 4: Guide users through self-remediation
The 1Password browser extension guides employees through step-by-step instructions to resolve issues on their own, eliminating the need for an IT ticket.
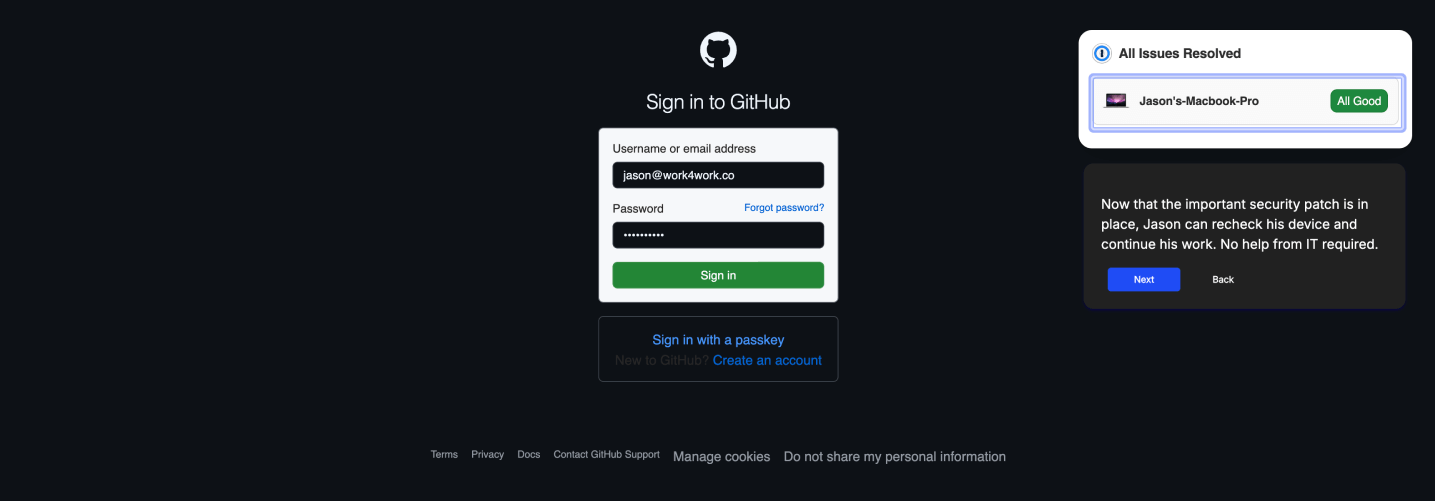
Step 5: Seamless re-access once compliant
Once the user resolves the issue, the extension instantly re-checks the device and unlocks access to the app without requiring any additional steps.
Getting started with Extended Device Compliance
To support different environments, Extended Device Compliance is available in both versions of 1Password Device Trust:
Device Trust Core, built for teams that don’t rely on SSO or don’t have a compatible IdP. It uses the browser extension to enforce compliance across any app, no IdP integration required.
Device Trust Connect, built for organizations that use Okta, Microsoft Entra, or Google Workspace. It combines Extended Device Compliance’s browser-based enforcement with identity-layer protection, allowing posture Checks to happen both at login (via the IdP) and in the browser (via the extension).
This dual-layer model is what sets 1Password Device Trust apart. It’s a solution that doesn’t stop where most solutions do.
If you’re ready to close the Access-Trust Gap by securing unmanaged applications and devices, we’re here to help. Schedule a demo to see Extended Device Compliance in action and visit the Device Trust product page to learn more.

 by Evan Sandhu on
by Evan Sandhu on