Traditional cybersecurity practices often work to obstruct users rather than help them. In this article, we explore this phenomenon and ways to refocus on user-centered security.
At 1Password, we believe that IT folks genuinely want to help their users. We speak to IT leaders every week, and we can feel their excitement when we discuss tools that hold the promise of improving the work lives of end users.
If this is the norm — and we genuinely believe it is — why do so many employees see IT teams as obstructors? Is it because of the tools? The organizational structure? Or simply a perception issue?
Whatever the root cause, this animosity between end users and IT security is a problem. And the first step of solving a problem is identifying it, describing it, and giving it a name. (And end-user frustration, thy name is security.)
Not too long ago, Kelly Shortridge coined a new term: security obstructionism (SecObs). Kelly defines SecObs as the policies, tools, and practices that result in outcomes that impede progress under the guise of maintaining security.
Even though Kelly uses the term with her tongue firmly planted in her cheek, we think that the underlying sentiment of the piece has significant merit.
In this piece, let’s take this term at face value, explore how it self-perpetuates within organizations, and find ways for everyone in IT and security to avoid falling into the SecObs trap.
What is security obstructionism?
Instead of achieving better security outcomes to support a business, SecObs causes IT teams to use security outputs as a proxy for progress. Kelly’s piece shows many visceral examples of SecObs at your business, including:
Forced device restarts (as a first measure), arbitrary password resets, access approval, key rotations, and other policies that leave users unable to work.
Vulnerability management processes that create long lists of unimportant triage items, which back up workflows and impact operational efficiencies.
Manual security reviews or change approvals that block teams from shipping new code without the go-ahead of the security team.
Phishing simulations or other training conducted with a “gotcha” mentality, creating tensions between employees and the IT team (and potentially leadership.)
Interfering with or shutting down digital transformation initiatives (e.g., no-code platforms that empower citizen developers to build and publish apps.)
The use of bossware as an “insider threat” detection tool, such as keyloggers and screen recording.
Mandatory but perfunctory employee training that fails to address knowledge gaps or improve measurable security outcomes.
A culture that expects employees to follow security rules blindly without understanding why things are done.
Essentially, any security measure that requires the excessive hands-on involvement of the security and IT team has the potential to turn into SecObs tactics.
What’s wrong with security obstructionism?
Now you may say: at least the IT team is doing something to keep the company safe … but is it?
SecObs focuses on security output rather than outcomes. The misdirected emphasis can cause a company to spend a lot of time and money on busy work (e.g., locking and unlocking access, superficial security training) without achieving meaningful results.
The highly manual processes that drive SecObs only create bottlenecks that impact employee productivity. They can also hamper more impactful digital transformation efforts that automate and democratize IT and security tasks.
Moreover, many detection and monitoring methods favored by SecObs are less than honest and transparent. Employees don’t know what agents are running on their devices and who has access to their data. The lack of trust often creates friction that can ultimately harm the company’s cybersecurity program.
Instead of proactively cooperating with IT, employees are more likely to go behind the security team’s back. For example, they may use personal devices or other forms of shadow IT to handle company data, making it harder to track and secure sensitive information.
To see the flaws of SpecObs in action, look no further than the healthcare industry. We’ve written previously about the creative ways medical practitioners have found to get around hospital cybersecurity. This isn’t because these end users are lazy or don’t care about security; it’s because they want to do their jobs, and their work is being continuously interrupted by having to log in more than 200 times a day.
Meanwhile, IT and security teams are blocked by their own share of SecObs. For instance, vulnerability and risk management programs that expect them to manually prioritize and patch an ever-growing pile of CVEs – most of which pose no real security risk. All while dealing with the conflicting pressures to secure sensitive data, work within tight budgets, get plans approved by executive leadership, and meet various compliance standards like SOC or ISO.
SecObs hamstrings innovation, diminishes operational efficiency, erodes employee trust, and even harms security outcomes.
How to achieve better cybersecurity outcomes
SecObs is baked into many existing security solutions, so overcoming it isn’t easy. Many applications claim to reinforce IT security but, in effect, create roadblocks to improving network security outcomes. Security requires friction. But there’s a limit to how much friction it can add before it starts to hurt more than it helps.
Companies must make conscious efforts to avoid falling into the SecObs trap. But how?
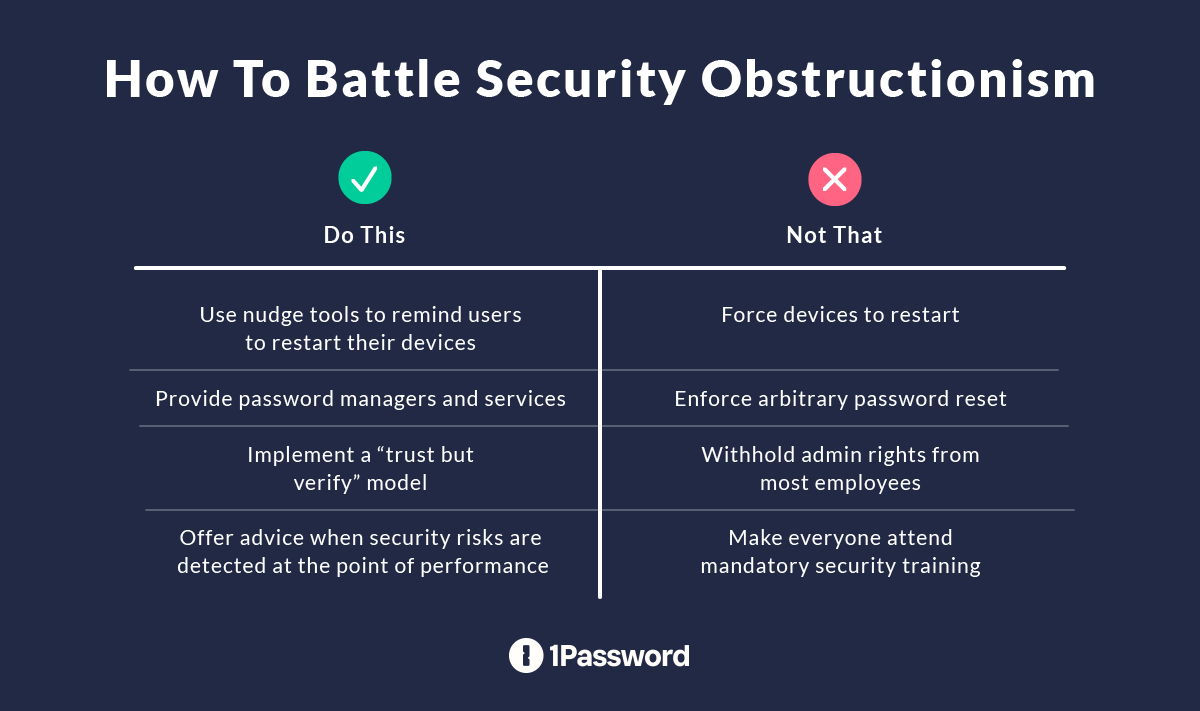
Device restarts
Imagine how frustrating it is if your laptop reboots when you’re in the middle of an important task. Forced device restart is not only intrusive, but also impacts productivity, and can even cause data loss. It conveys that the company doesn’t respect employees' time and privacy.
Instead, use tools like 1Password Device Trust. These give you the ability to enforce compliance without relying on forced restarts. Our device trust agent warns users ahead of time when their device is in an unsecure state, and tells them how and when to remediate the issue. 1Password Device Trust only blocks devices when they’ve passed the deadline for the update. Until then, employees have flexibility and control over their workflows, with the ability to install updates when they decide. This is just one way of improving cybersecurity ecosystems with the user in mind.
Password management
According to the 2024 Verizon Data Breach Investigations Report (DBIR), stolen credentials have factored into almost one-third of breaches over the last 10 years. And yet, our own study found that 61% of employees use weak passwords.
But forced password resets or arbitrary password requirements are not the answer to this problem – they add needless friction for end users, with very few security gains. In fact, they’re likely to harm security, but many companies still use them.
Of course, passwords themselves are a notoriously weak authentication factor. But rolling out SSO or passwordless auth can take time, or may not be suited for every login. Solutions like enterprise password managers can help users generate secure passwords and mitigate risk when there is evidence that a password was potentially compromised in a breach. And yet, many companies still fail to roll out this table stakes security, even if it provides the best experience for end-users.
Of course, when we talk about access management, we also have to talk about multi-factor authentication. We’ve written previously on the ways it can fall short, but using passwordless factors, like passkeys, can help prevent unauthorized access without forcing users to jump through endless hoops of authentication.
Security education
Imposing interruptive mandatory security training may check a compliance box, but does little to bridge the knowledge gap and show employees how your security policy relates to their job functions.
Instead, letting employees self remediate security issues teaches them best security practices in the moment, instead of in the abstract. 1Password Device Trust runs regular posture checks on employee devices. When there’s an issue, it provides detailed instructions on how to fix it. This is far more effective than watching one training video a year, as it engages employees in security in real time, and lets them learn by doing.

Such automation frees the security team from having individual conversations with every user when they do something that puts the company at risk. It also provides end users with the critical information they need to learn about an issue, fix it on their own, and prevent it from happening in the future, improving security in the long term.
Mindset changes to overcome SecObs
To truly overcome SecObs, IT leaders and teams must change their mindset around security. Their job shouldn’t be about “protecting the company from employees' stupidity.” They must start from a mindset of trusting that employees will do the right thing when given the right information. (This includes understanding that not doing the right thing will result in consequences, such as being blocked from authenticating.) Build policies with the principles of Honest Security in mind.
As such, you need the tools to educate employees and teach them how to take appropriate actions at the point of performance. Next, you need to take an “outcome over output” approach to security. The truth is that in today’s fast-paced digital world, it’s not feasible to create an airtight environment.
We’ll restate this for emphasis. There’s no such thing as perfect security, no matter how much you lock down your users' devices.
If you want realistic ways of reducing the likelihood of cyber incidents, you need a cybersecurity strategy that encourages users to be proactive.
When we focus on outcomes rather than output, we need to understand that security works best when it works with people, rather than against them. Tools that prioritize the end user experience are tools that users are more likely to embrace. Don’t use solutions that disproportionately hamstring your fellow employees in the pursuit of an impossible goal (you can’t mitigate every threat). Instead, focus and prioritize your mission on the highest impact vulnerabilities, and on the highest impact solutions.
 by Jason Meller on
by Jason Meller on