From project management software to plugins that correct your grammar, it seems like a new tool for supercharging workers’ productivity launches every day. While that’s great for innovation, there’s a downside: the accounts employees create without a business’s authorization or awareness, known as shadow IT.
At first glance, shadow IT might appear harmless. The problem is, without the oversight and direction of IT, it’s easy for employees to unwittingly create vulnerabilities in even the tightest of security setups.
How prevalent is shadow IT?
There’s plenty of anecdotal evidence of how disruptive shadow IT accounts can be, but we wanted data.
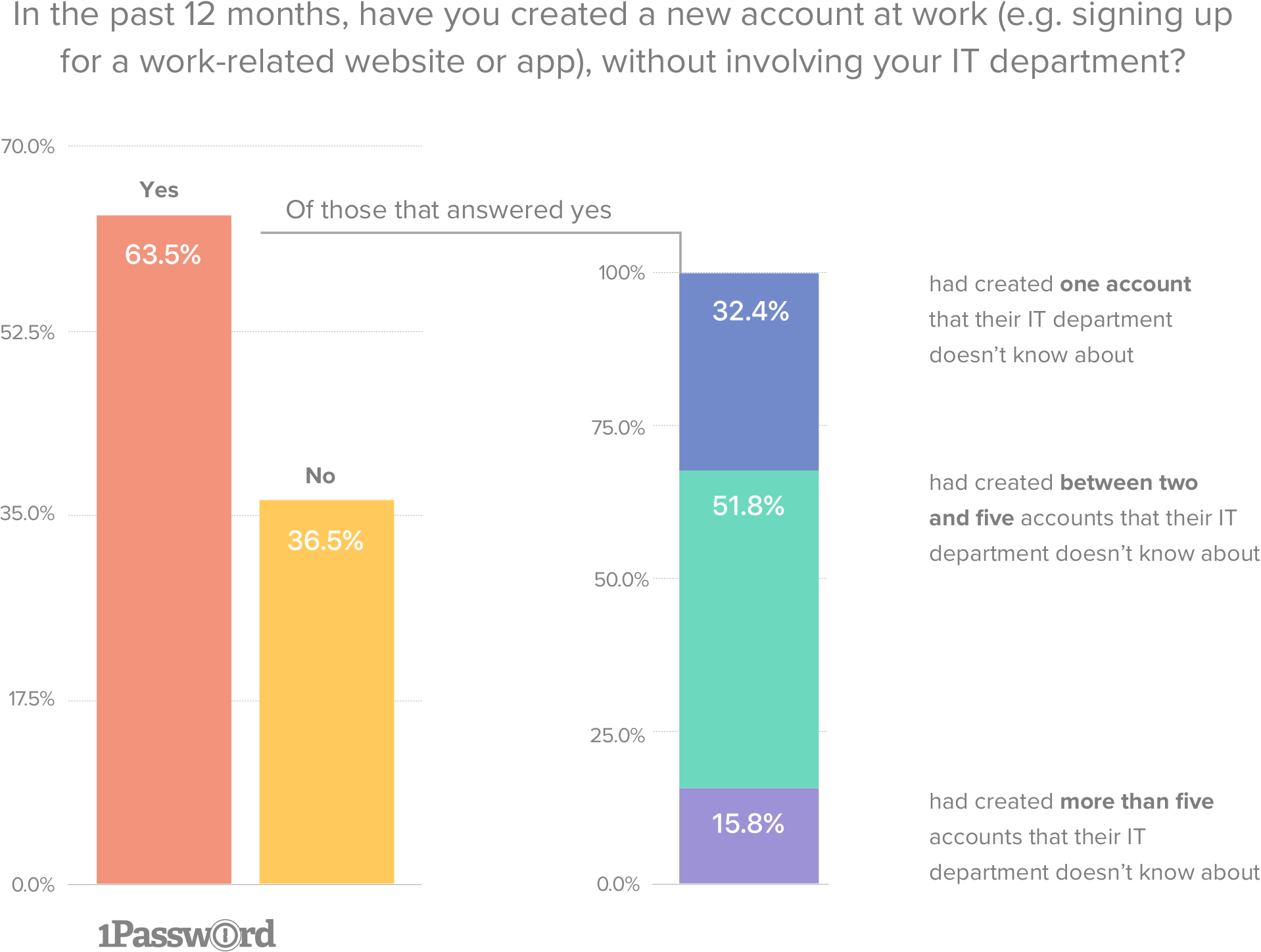
So, we surveyed a representative sample of 2,119 U.S. adults who work in an office with an IT department and use a computer for work (see end of post for methodology), and found that a staggering 63.5% (± 1.03) of respondents have created at least one account in the past 12 months that their IT department doesn’t know about:
- Yes 63.5% (± 1.03)
- No 36.5% (± 1.03)
Of those that answered yes:
- 32.4% (± 0.67) had created one account that their IT department doesn’t know about
- 51.8% (± 0.67) had created between two and five accounts that their IT department doesn’t know about
- 15.8% (± 0.67) had created more than five accounts that their IT department doesn’t know about
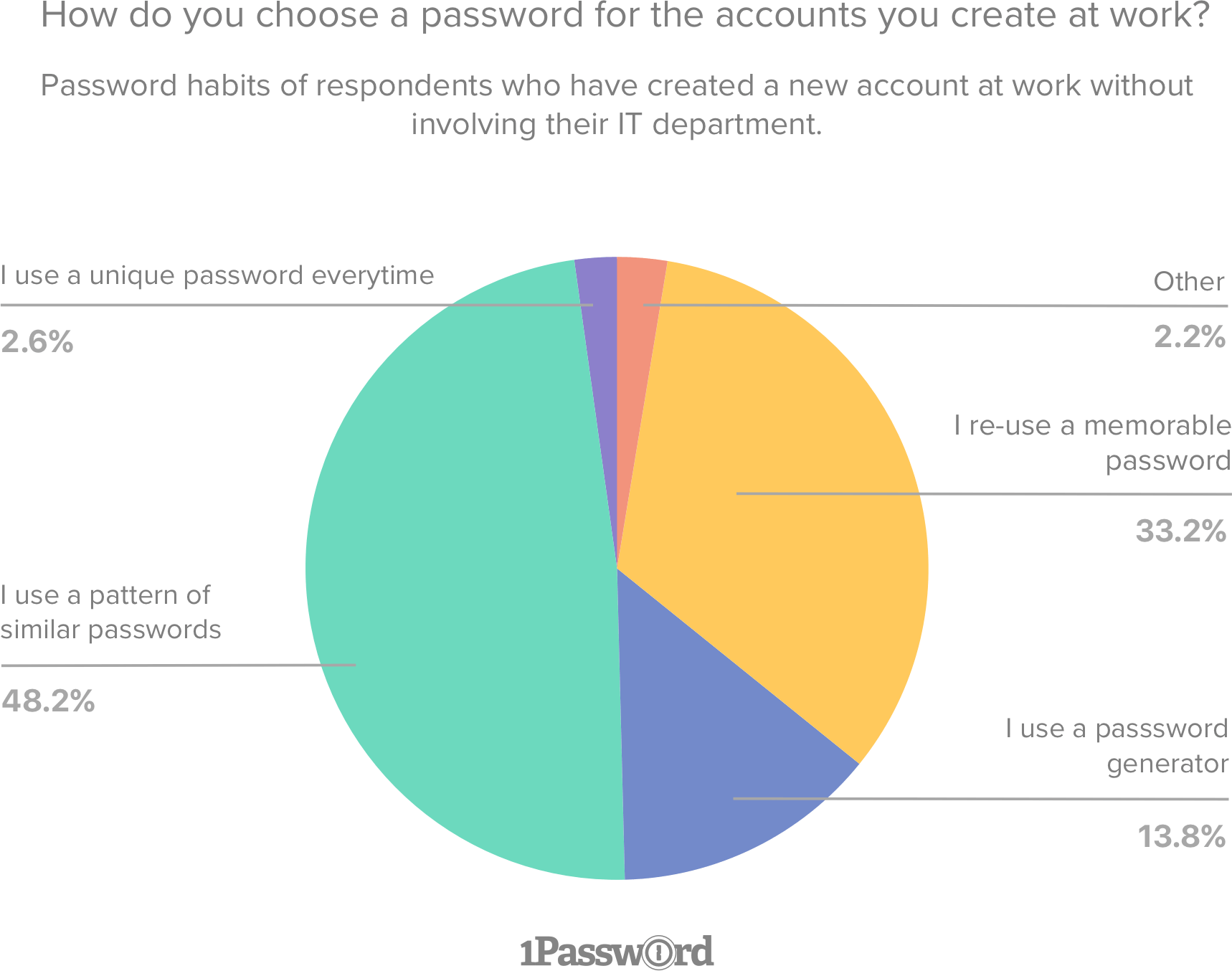
What’s more troubling is that 33.2% (± 1.03) of people who have created shadow IT accounts reuse memorable passwords, and 48.2% (± 1.03) use a pattern of similar passwords. Only 2.6% (± 1.03) said that they use a unique password every time.
The dangers of shadow IT
So, why is this a problem? Carlos in Marketing opens an Airtable account, and Anita in Legal uses Grammarly to check for grammatical errors. Often, these services are free to use and make it easier for employees to do their jobs. Ultimately that’s a good thing, right?
But when employees use services without the authorization of the IT team, it brings risks. Say Carlos populates Airtable with customer data for his email campaigns, and Anita checks sensitive legal documents in Grammarly. Without thinking about it, they’re sharing a lot of important data with external companies that IT doesn’t even know about.
If one of these services suffers a breach, the company won’t know it affects them, which leaves them powerless to secure their data after the event. It also means they’ll be unable to disclose it to their customers. This could leave any company facing costly fines and a huge loss of trust in its operations.
And, when over 80% of data and privacy breaches are due to poor password practices, the risk multiplies when employees use weak, reused, or memorable passwords for the services they’ve signed up to. If those login details are compromised, attackers could use that information to access other accounts, which may also hold sensitive data.
Who has access?
Shadow IT can also cause problems when an employee quits or is fired; 20.5% (±0.40) of those surveyed reported getting locked out of a work account because a colleague left the company.
But who loses access isn’t the only concern: If an employee leaves, they’ll retain access to the accounts they’ve created outside of IT’s purview. At worst, this company data could be shared with a competitor; at best, it’s left dormant and hidden, but it still puts the company at risk if the service is breached.
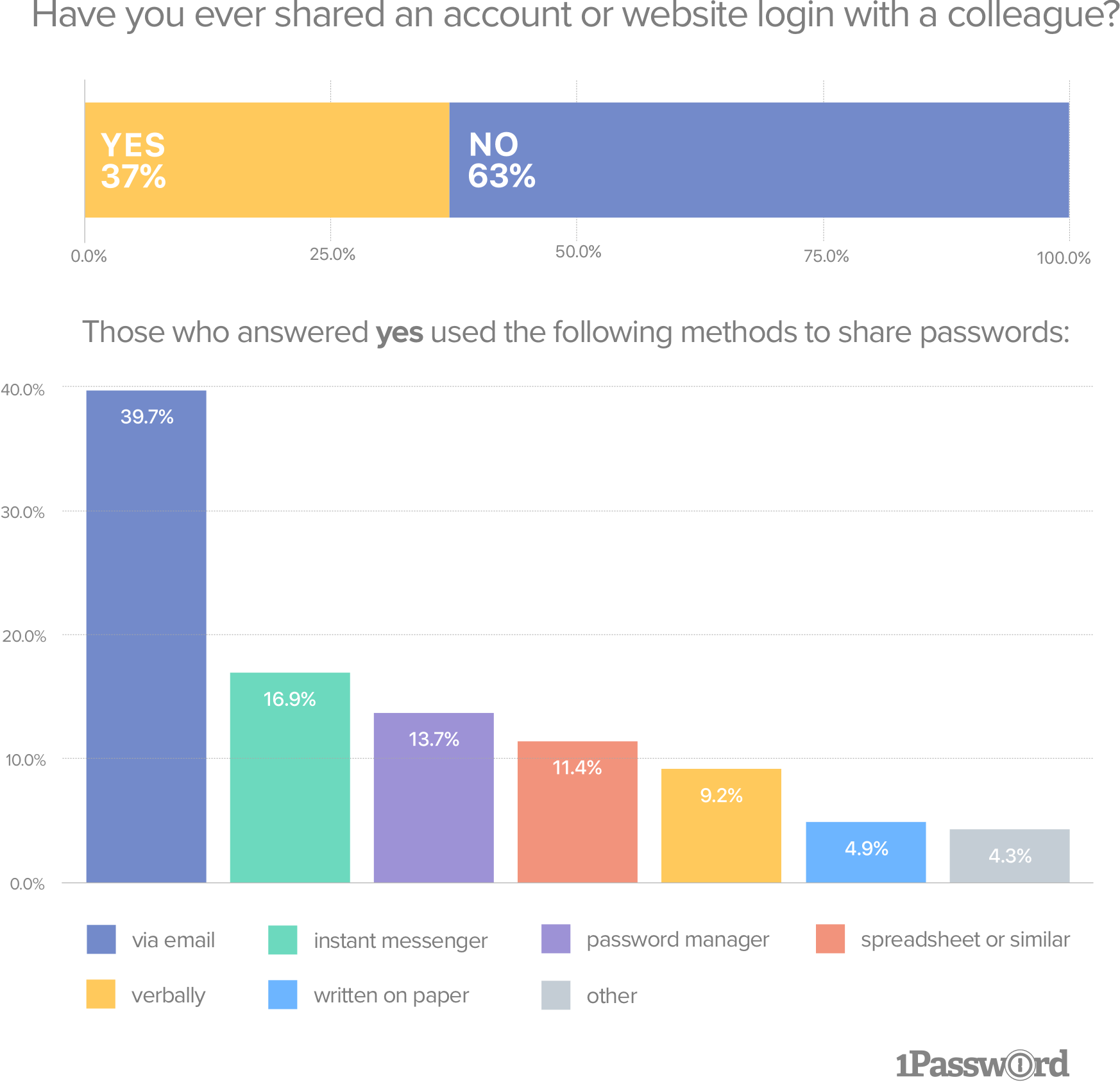
Our research also found that 37.0% (± 2.04) of respondents had shared an account with a colleague. The most popular methods of password sharing were worryingly insecure, with email (39.7% (± 1.46)) and instant messenger (16.9% (± 1.46)) coming out on top. Here’s the full breakdown:
Have you ever shared an account or website login with a colleague?
- Yes 37.0% (± 2.04)
- No 63.0% (± 2.04)
Those who answered “yes” used the following methods to share passwords:
- 39.7% (± 1.46 ) email
- 16.9% (± 1.46 ) instant messenger
- 13.7% (± 1.46 ) password manager
- 11.4% (± 1.46 ) spreadsheet or similar
- 9.2% (± 1.46 ) verbally
- 4.9% (± 1.46 ) written on paper
- 4.3% (± 1.46 ) other
Even more concerning are the password habits of those using insecure digital methods (for example, instant messenger, email, spreadsheet) to share these passwords – 51.1% (± 0.99) use a pattern of memorable passwords, and 37.8% (± 0.99) will reuse passwords.
That means 88.9% (± 0.99) of people who share passwords through insecure digital methods either use password patterns or reuse passwords. It’s a huge risk to share passwords insecurely online, and it’s even riskier when those passwords could be used to access other accounts.
Understanding unseen passwords
The problem is two-fold: The symptom of shadow IT is unseen passwords. Your business may have a system in place for securing the credentials of the accounts they’ve approved, but what about when people start using services outside that list?
These login details may be stored on employees’ phones, in cloud-hosted spreadsheets, or in plain-text documents, creating untraceable holes in a business’s security. That’s on top of the risks we’ve already detailed above.
But banning shadow IT altogether has its drawbacks. It slows employee productivity as every new service or app will need approval from the IT department, creating a bottleneck and more work for everyone. It also halts innovation and creates resistance to finding new and better ways of working. Businesses need to find a way to bring it all back under their control without hindering their employees’ ability to excel in their roles.
Security facilitates innovation
To overcome this and encourage productivity and process improvements, businesses must create a safer environment in which shadow IT can exist, rather than banning it outright.
Businesses that use a password manager like 1Password are better positioned to secure any account, whether they know about it or not – employees can generate strong, unique passwords and save them in a secure and shareable way. This addresses the inclination to reuse passwords or share them using insecure methods.
We’re growing our teams responsible for customer education because we know that when it comes to security, it needs to feel easy and convenient. When it does, over time, employees’ confidence grows and security habits change for the better.
These practices need to continue at home, too, which is why we offer a free 1Password Families membership to everyone who uses 1Password Business. When security is seamlessly integrated into employees’ professional and personal lives, it makes them inherently more aware of the risks associated with opening new accounts and the importance of securing their credentials.
After those good security habits are in place, even accounts outside the view of the IT team will be protected with a strong and unique password. And if these credentials are stored securely, they’ll remain in your hands, even after an employee leaves.
By catching and protecting the accounts IT doesn’t know about, 1Password is uniquely situated to solve the issue of shadow IT and unseen passwords – without slowing productivity, stifling innovation, or creating bottlenecks.
Methodology
These results are based on the December 2019 polling of a representative sample of 2,119 American adults (18+) via SurveyMonkey’s Audience platform. Survey respondents were paid.
 by Jeff Shiner on
by Jeff Shiner on

Tweet about this post