The differences between 1Password and Keeper go a lot deeper than passwords.
If you’re comparing 1Password and Keeper (and it seems like you are, since you’re reading this article) then it pays to be well-informed before you make a purchase.
Keeper and 1Password both provide Enterprise Password Managers (EPMs), which are the foundational products of both companies. So if you’re here to compare password managers, we’ve got you covered.
But, while EPMs do a lot to keep systems secure, they work better with the help of a more holistic security suite that goes beyond credential management. Fortunately, this is something that both our companies also offer. Keeper provides a lightweight Privileged Access Management (PAM) solution, while we provide 1Password Extended Access Management. (XAM).
So, in the interest of giving you a complete comparison of our products, we’ll use this article to contrast Keeper and 1Password in three areas: credential management, device trust, and the impacts they have on your business and users.
We’ll start with an overview of the security solutions offered by our two companies.
What is Privileged Access Management (PAM)?
PAM is a type of security solution that’s all about securing and monitoring privileged accounts–administrators and others with access to highly sensitive information.
Keeper is just one vendor in the PAM category, and there are some variations between PAM products, but the critical capabilities of PAM include:
Privileged credential management: PAM solutions scan for privileged credentials, and then take steps to secure their access. That might mean rotating credentials, using an EPM to manage those logins, or and other methods
Session management: When a user begins a privileged access session, PAM solutions include the ability to monitor and record their actions during that session.
Keeper PAM: Keeper PAM is a more lightweight take on the PAM product category. Part of what differentiates it from more traditional PAM solutions is that it’s completely cloud-based. In their words, Keeper PAM consolidates three “disparate PAM tools into a unified platform.” Those tools are: the Keeper EPM, the Keeper Connection Manager (KCM), and the Keeper Secrets Manager (KSM).
All of these tools together can meet some of the critical PAM requirements, but it’s still a less robust solution than traditional PAM, which is part of why Keeper PAM isn’t recognized as a fully-fledged PAM solution by companies like Gartner and Forrester.
Regardless, the real question, if you’re comparing 1Password vs Keeper, should be: which company meets the specific security needs of your team?
What is Extended Access Management XAM?
Extended Access Management (XAM) is a new product category, distinct from PAM, Identity Access Management (IAM), and Mobile Device Management (MDM), though with elements of all three.
The goal of XAM is to take a more holistic approach to access management, in order to account for vulnerabilities outside the scope of other solutions.
In a nutshell, the reality of doing business today – with hybrid work, the proliferation of SaaS apps, and BYO-devices – has created several security weaknesses. There’s a gap between the users, applications, and devices that businesses actually trust (the ones they manage and know are secure), versus all the logins, devices, and apps that can access sensitive data in practice.
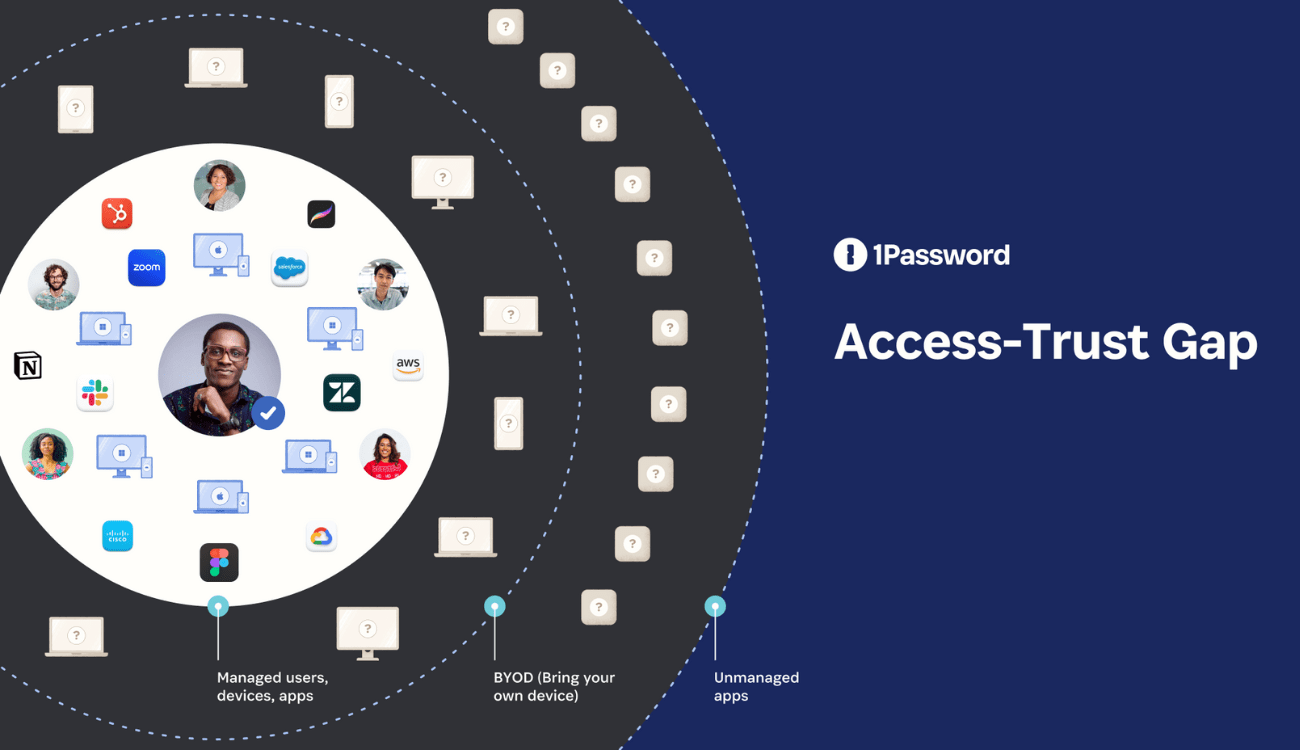
XAM seeks to bridge this “access-trust gap.” To do so, it needs to bring visibility and enforcement to things like employee personal devices, shadow IT apps, and third party contractor identities.
Here are a few critical components of XAM:
- Device trust: ensure that a device is both known and in a secure state before it accesses company resources.
- Application insights: visibility and oversight over the applications that employees use for work, not just the ones approved by IT.
- User identity: the ability to verify the identity of users before they’re allowed to access sensitive data (think SSO and MFA).
- Enterprise credential management: tools to manage and secure end-user access to shared credentials.
1Password Extended Access Management: our XAM solution achieves these goals through our 1Password EPM and Device Trust solutions, combined with Application Insights and User Identity (coming soon). By combining the abilities of each, we’ve made a solution that can secure every sign-on, from every app, on every device.
As you can see, while there is overlap between XAM and PAM, these two solutions use different methods to achieve different goals. PAM is an intensive security solution appropriate for a small subset of users. XAM is a more user-friendly solution designed for your entire workforce.
To understand the consequences of these differences, we’re going to dig into three areas of our business: Credential management, device trust, and business impacts.
We’ll start with a direct comparison of the component that we have in common: our EPMs.
Credential management
You likely came here because you’d heard of our EPM. But just in case you need a refresher … what is an EPM?
Enterprise password managers store and encrypt users’ login credentials in order to discourage users from re-using the same password or, for example, putting them on a sticky note next to their desk. EPMs typically come with a password generator to ensure that users are using unique passwords, and they also allow you to share login information with other authenticated employees.
All of the above is true for both 1Password and Keeper. But there are also important differences between our products, starting with the features that come standard, versus the ones you have to pay extra for. As you can see in the table below, 1Password EPM includes many critical features as part of our standard product, while Keeper treats them as add-ons.
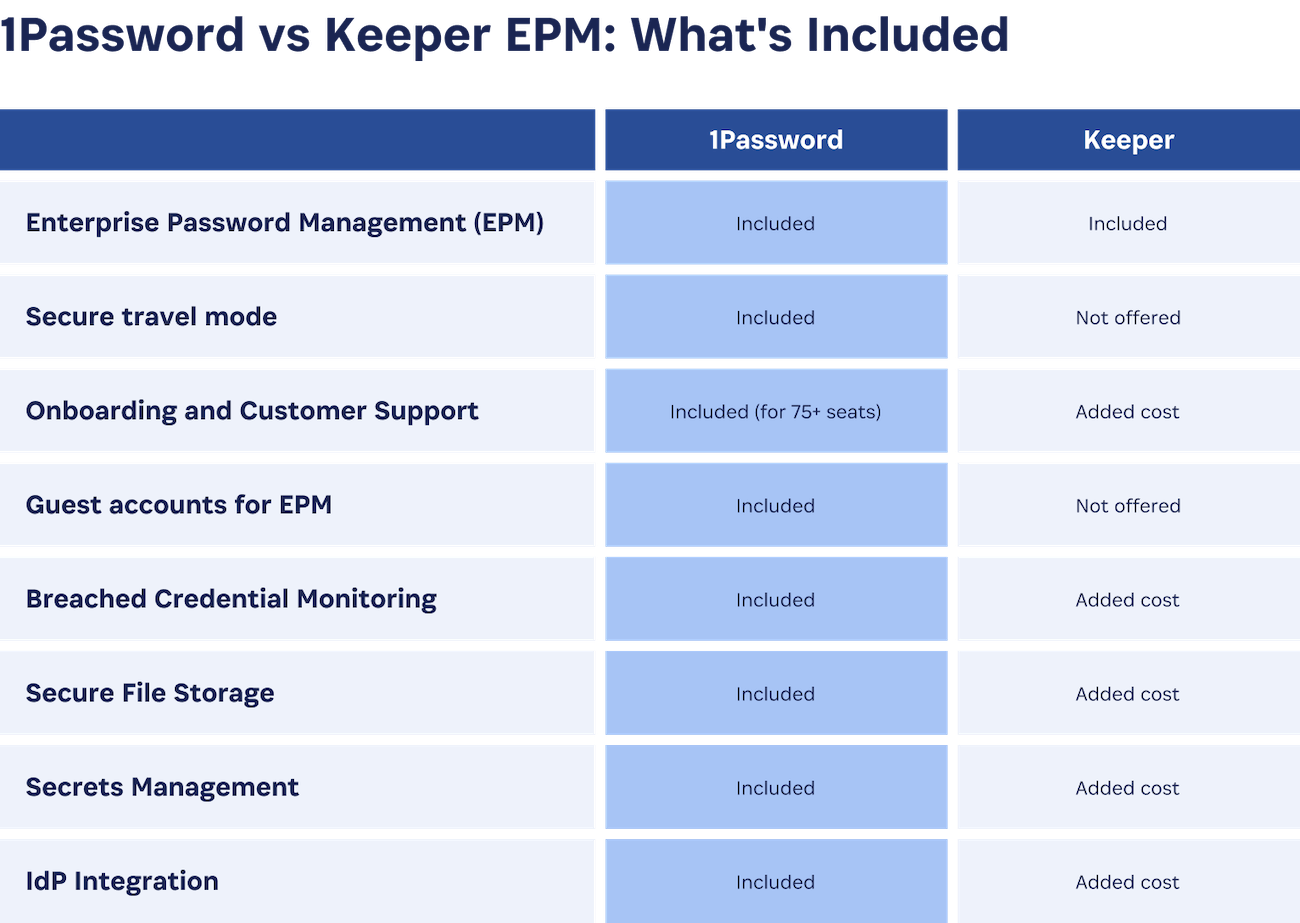
Let’s dig a little deeper into the factors that set our EPMs apart.
Encryption
Both Keeper and 1Password EPM use AES-256 encryption. When you use either service, all of the decryption is done locally on your device. We both also operate using a zero-knowledge architecture, which means that nobody at either company can see your passwords.
The reason 1Password EPM consistently wins over Keeper in security comparisons is that we go one step further, with a 128-bit secret key for account access. This key is next to impossible to crack, and keeps accounts safer from attack than a master password alone, which is what Keeper has.
1Password also uses a password-authenticated key exchange (PAKE) to protect the user’s password and adds an additional layer of security to authentication.
Breach monitoring
Both Keeper and 1Password have the ability to alert users when a password for their account has been compromised and leaked on the dark web. 1Password’s service is called Watchtower, while Keeper’s is BreachWatch.
With 1Password, Watchtower alerts are included in your company plan, whereas Keeper’s BreachWatch costs extra.
Secrets management
Keeper describes their secrets manager as a core element of their PAM solution. But they also sell it as an add-on that doesn’t come standard on even the enterprise tier of their password manager. On top of that, it’s less robust than 1Password’s secrets manager, and its integrations are more difficult to deploy. Let us explain what we mean by that.
Keeper’s secret manager has an installable ssh agent, but that requires their CLI to run – and Keeper CLI is only available for their Enterprise plan. They also charge an extra fee for SDKs and CI/CD integrations.
And, while their offering is integrated with a number of services, it doesn’t have a REST API available for non-native platforms to use the service.
1Password, however, provides a built-in SSH agent and full CLI. Access to SDKs and CI/CD integrations are also part of the core product–at no extra cost.
1Password’s Secrets Automation also supports several plugins/SDKs, as well as a REST API to be used on any other platform.
Third-party audits
Keeper and 1Password both conduct regular third-party security audits. Keeper, however, maxes out their bug bounty at $10,000 (or they’ll ask you to pay, if you happen to be a reporter who wrote an article about a Keeper bug).
1Password proudly has the highest bug bounty program of any password manager (hack us, and you could get 1 million dollars).
Secure travel mode
1Password includes a secure travel mode, which allows you to limit the amount of information that’s stored on your individual device during travel. This way, in cases where border or custom officials ask a user to unlock their phone, or where devices are stolen or confiscated, they can ensure that highly sensitive data still isn’t seen. Only the vaults marked “safe to travel” will stay on the device.
Keeper does not have a secure travel mode.
Onboarding and customer support
Keeper charges for support, with prices increasing depending on the size or needs of your company.
1Password EPM, however, includes onboarding and customer support for any account over 75 seats; admins get the help of a dedicated team as they roll out the solution.
Device trust
Once you’ve secured your workforce’s credentials via an EPM, your next step should be to secure their devices. But, because Keeper PAM works through a remote browser add-on, it has little oversight beyond the work that gets done in the browser.
A lot of vulnerabilities can lurk on devices, including malware that can slip upstream via the browser. It’s critical that the devices that access sensitive systems are patched, healthy, and free from vulnerabilities. Moreover, it’s critical that employees only use devices that are associated with their identities–otherwise bad actors using stolen credentials can log into your systems.
IAM and PAM tools can’t limit access from unhealthy devices. Indeed, most security solutions, even if they offer some limited information about devices, can only work to secure company-owned and managed devices. That leaves you with no way to ensure the safety of personal and contractor devices.
How XAM solves for device trust
Device trust is a subset of zero trust security that only allows trusted and healthy devices to access company systems.
1Password Extended Access Management comes with a sophisticated, industry-leading device trust solution that integrates with your identity provider’s authentication flow. If a user’s device is found to be compromised, the user will not be allowed to authenticate until they have fixed the problem.
It also provides a complete inventory of all of the endpoints able to access company systems, and works on macOS, Windows, Linux, iOS, and Android.
Device health
1Password Extended Access Management offers a rich and comprehensive look at a device’s health, that far exceeds the capability of MDM solutions.
That includes over 100 pre-built policy checks, that do things like ensuring the browser and OS are updated, ensuring the firewall is on and security software is properly configured, and that sensitive data is not sitting around on the hard drive.
In addition to this library of checks, 1Password Extended Access Management also includes the ability to write custom checks around specific vulnerabilities you’re concerned with.
And if users don’t fix those vulnerabilities in a timely manner, then they’re blocked from authentication.
Self-serve remediation
Sorry, what was that? If users don’t fix their device vulnerabilities?
You heard us.
Self-serve remediation is one of the signature features of 1Password Extended Access Management, and it’s a big part of what makes our solution so effective and user-friendly.
If a device fails a posture check, 1Password Extended Access Management will alert the user immediately, tell them how to fix it via easy-to-follow instructions, and let them know how long they have to fix it before they’ll be blocked from authentication. This minimizes disruptions to productivity, educates end-users, and reduces IT support tickets.
1Password vs Keeper: which is right for your needs?
PAM and XAM have some overlap in their use cases, particularly in how they each help with credential management via the EPM. However, these solutions are ultimately suited for different purposes, so in many ways it’s an apples-to-oranges comparison between the two. In fact, you could choose to use both PAM and XAM alongside one another! What’s important is understanding which tool is right for the problems you’re trying to solve.
Keeper PAM
Keeper PAM provides insight into privileged account credentials, and who has access to them. That can help teams follow principles of least privilege, keep highly sensitive data secure, and even guard against insider threats, to a degree. It makes sense that market research shows PAM solutions as being popular in industries known for handling highly secure data–like banking, government sectors, and healthcare.
Still, PAM solutions are typically best suited to larger companies, with enough IT support to dedicate to its implementation and rollout. PAM has long been infamous for being quite complex to roll out. Keeper PAM is cloud-based, which reduces some complexities, but also robs it of some of the power and cohesion of traditional PAM solutions.
Keeper PAM secures privileged access through an agentless browser add-on, which means that any privileged browsing session can be recorded. However, its focus on the cloud and the browser does mean that it will work best for companies whose most privileged admin work can be done primarily through web-based apps.
Keeper PAM, like their EPM, also comes with many hidden costs and complexities, starting with the initial price tag and extending to the additional costs your team incurs depending on the add-ons and support you need to implement and maintain the solution. Those add-ons include things like: secure file storage, customer support, and their reporting and alerts module.
With that in mind, Keeper PAM isn’t likely to provide much ROI for smaller companies, those who don’t have the complex administration structure that it’s designed to serve, or those that host a lot of work or data off of SaaS apps.
1Password Extended Access Management
1Password Extended Access Management uses device trust, which looks for security issues beyond the browser. It protects the credentials and devices of every user, as opposed to focusing only on your most privileged accounts. And this is important, since most users have access to some form of sensitive data, and even the lowliest account can be a launchpad for a privilege escalation attack.
Its flexibility in the ability to share or store secrets is also ideal for companies that need to work with third-parties.
1Password is also a good choice for organizations that want to prioritize user experience and privacy. Our solutions are proudly transparent about the data we collect on user activity, which is why users are willing to install us on their unmanaged, personal devices.
Conclusion
While Keeper and 1Password are competitors in the EPM business, in many ways, PAM and XAM are quite complementary; one protects highly privileged access, and the other fills in the access-trust gap.
But even on its own, 1Password Extended Access Management provides a flexible and user-friendly way of protecting against credential-based attacks, ensuring the health of the endpoints in your fleet, and giving you visibility into shadow IT.
We would love to have an honest discussion with your team about how XAM can help you meet your security goals–whether you’re currently using PAM, IAM, or something else. Let us help you make the right choice for your company.
If you want an honest discussion with a supportive team, please reach out to us.

 by Rachel Sudbeck on
by Rachel Sudbeck on